Webhacking.kr write-up: old-6
3 minutes to read| Link | point | tag |
|---|---|---|
| old-6 | 100 | Session hijacking, scripting |
Welcome back to another webhacking.kr CTF challenge. Today, we are going through for another session hijacking but this time we have to complete the challenge with basic scripting.
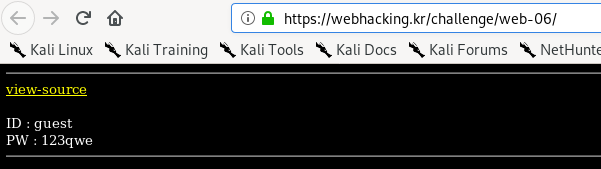
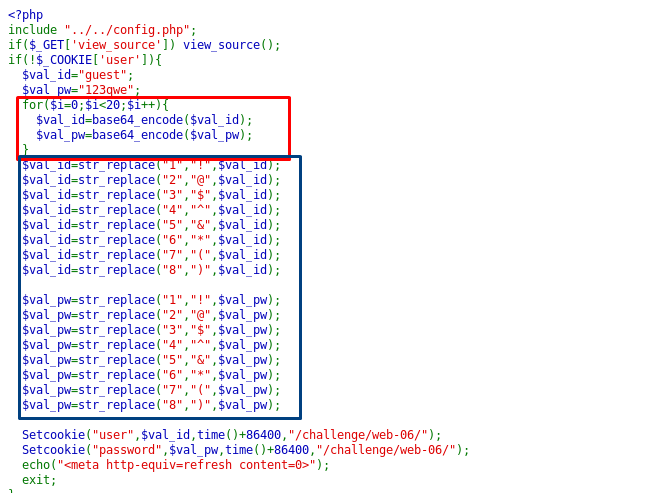
On the front page, we are greeted with ID and PW and we have no idea what is the credential used for. By studying the given source code, the credential was assigned into the cookies. Before that, both ID and PW values are encoded with base64 for 20 times (red box). Then, some of the characters on the encoded credential is replaced with special characters (blue box).
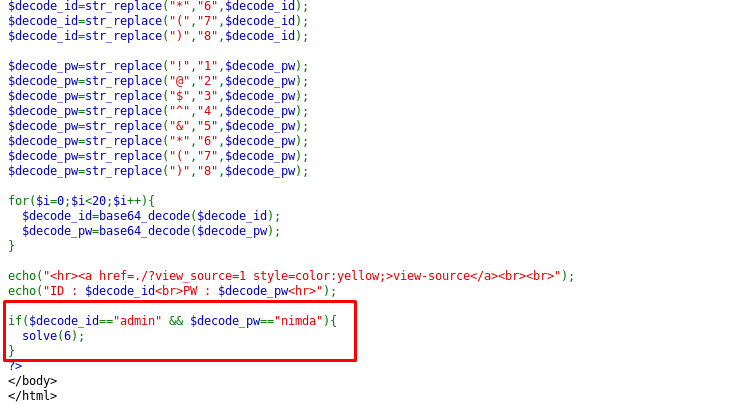
If you scroll to the bottom of the page, you will notice that the credential used to solve the challenge is admin:nimda. Hence, our main goal is the hijack the cookie with the given credential by repeating the above steps.
- Encode the ‘admin’ and ‘nimba’ in base64 for 20 times
- Replace some of the characters associates with the source code
- Encode the base64 with URLencode as the cookies are in URLencode format
import base64
import urllib.parse
user = b"admin"
password = b"nimda"
for i in range(20):
user = base64.b64encode(user)
password = base64.b64encode(password)
euser = user.decode('utf-8')
epass = password.decode('utf-8')
#string replacement to url encode instead of symbol
euser = euser.replace('1','!').replace('2','@').replace('3','$').replace('4','^').replace('5','&').replace('6','*').replace('7','(').replace('8',')')
epass = epass.replace('1','!').replace('2','@').replace('3','$').replace('4','^').replace('5','&').replace('6','*').replace('7','(').replace('8',')')
#urlencode
euser = urllib.parse.quote(euser)
epassword = urllib.parse.quote(password)
print("\033[1;31;40m user id: \033[0m")
print(euser)
print("\033[1;36;40m user password: \033[0m")
print(epassword)
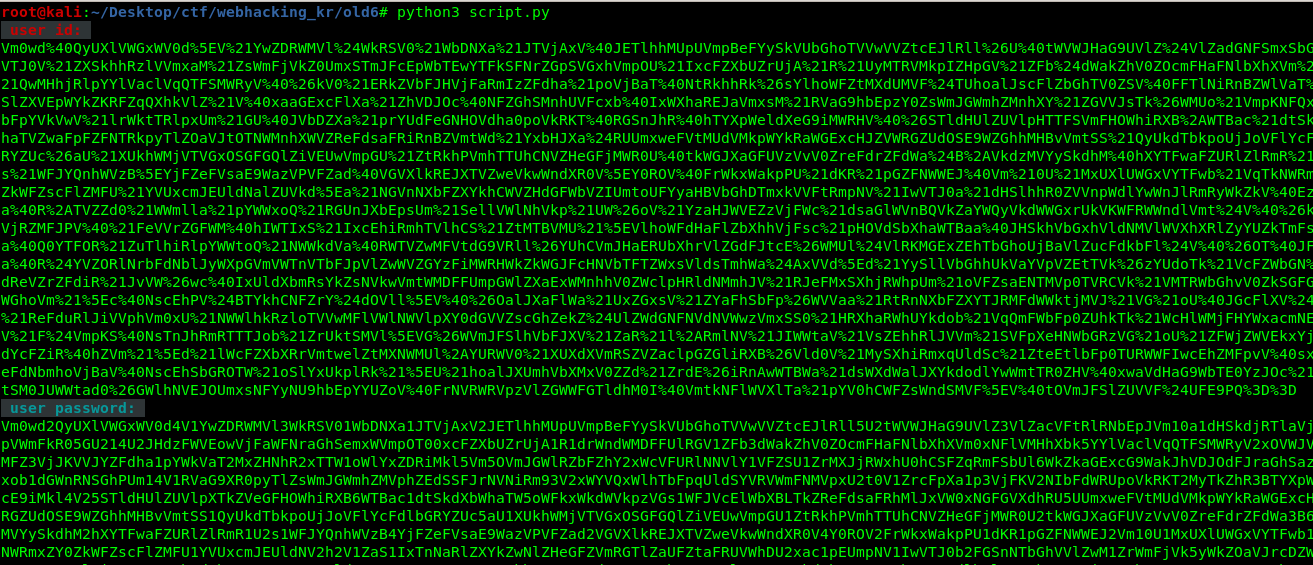
After that, copy the encoded id and password into the ‘user’ and ‘password’ cookies, respectively.
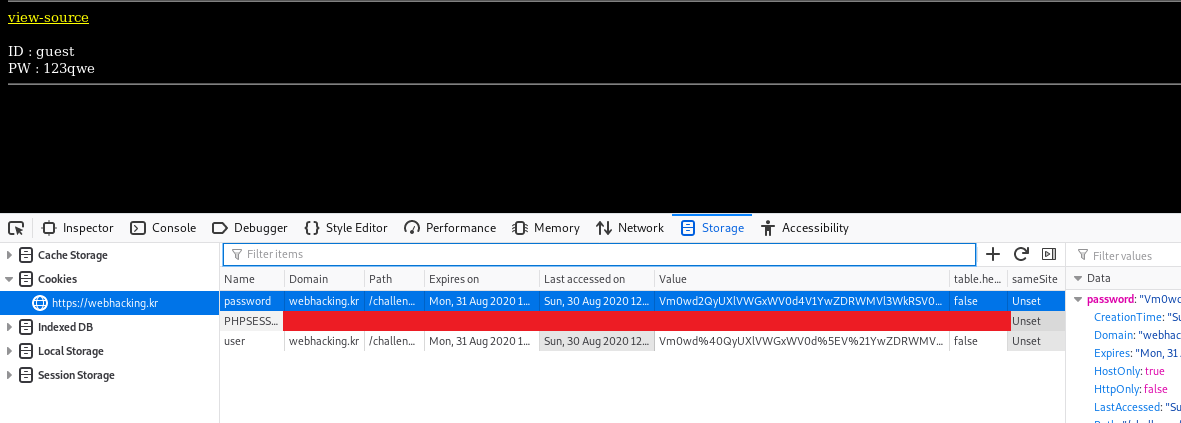
Refresh the page and solve the challenge.
Thanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)