Webhacking.kr write-up: old-33
5 minutes to read| Link | point | tag |
|---|---|---|
| old-33 | 200 | PHP |
Hello there, welcome back to another longest write-up in webhacking.kr. This room contains 10 sub-challenges which is suitable for you to sharpen up your PHP skill.
- Challenge 1
- Challenge 2
- Challenge 3
- Challenge 4
- Challenge 5
- Challenge 6
- Challenge 7
- Challenge 8
- Challenge 9
- Challenge 10
Challenge 1
Let’s look at the source code
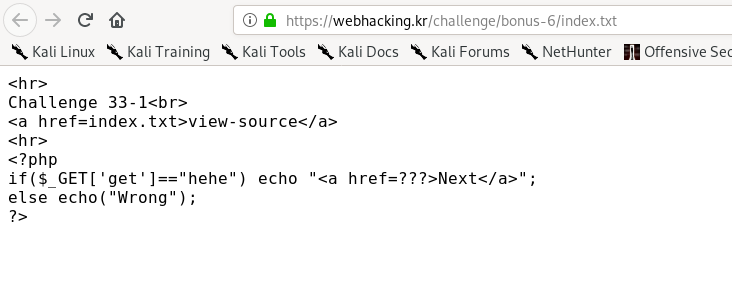
You are required to send a GET request to complete the challenge.
https://webhacking.kr/challenge/bonus-6/?get=hehe
Challenge 2
How about the source code?
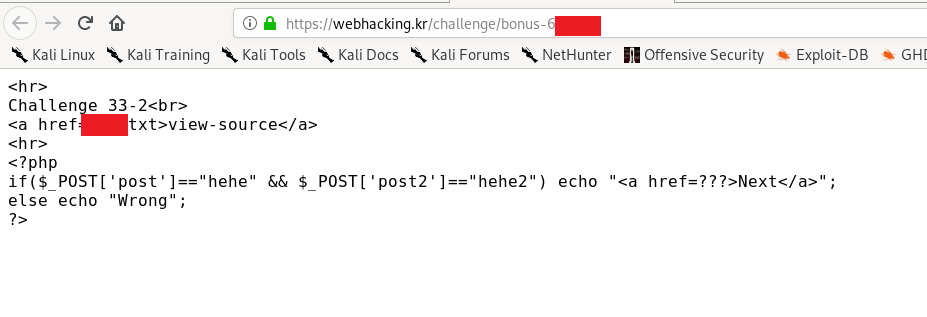
It seems we have to send two post request to the server. It can be done either using a browser or burp suite. For this instance, I’m going to use the built-in request function inside the firefox.
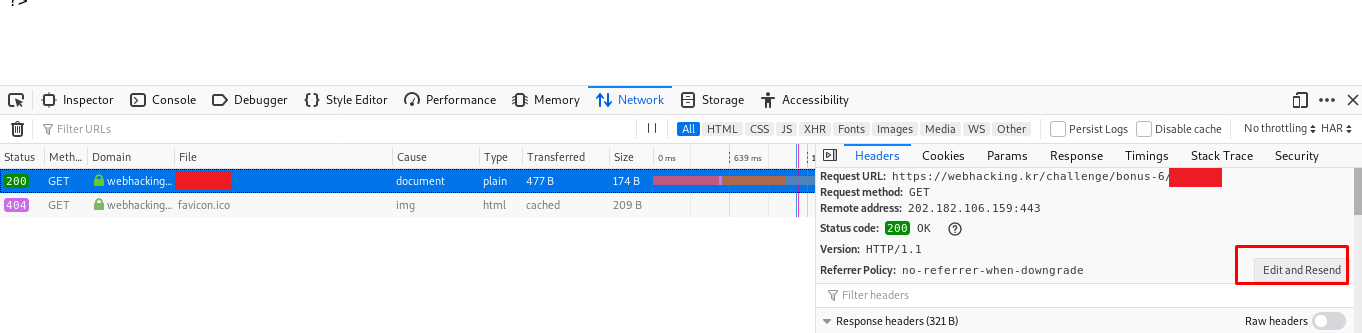
Make sure you have change the method and the POST data before proceeding.
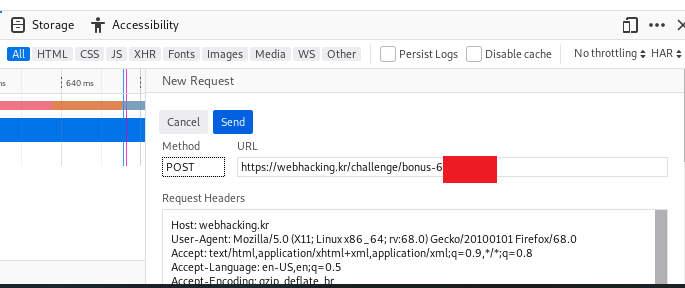
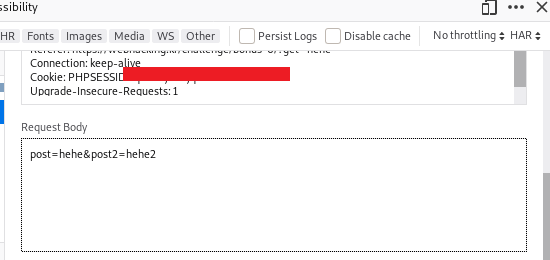
After you have done, double click the response and proceed to the next level.
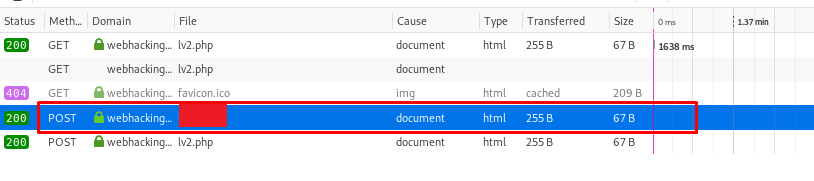
Challenge 3
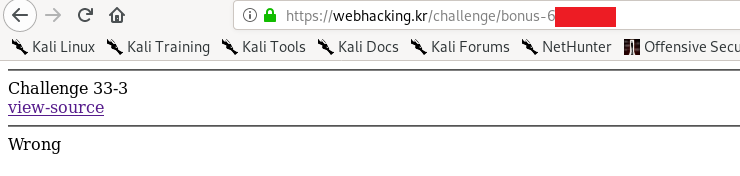
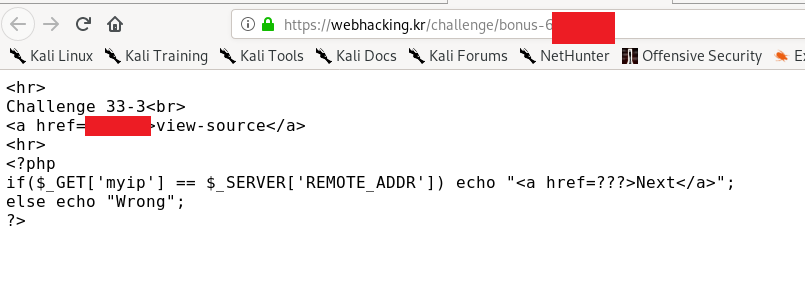
Google your own IP address and send the request
https://webhacking.kr/challenge/bonus-6/<reducted>.php?myip=<your IP address>
Challenge 4
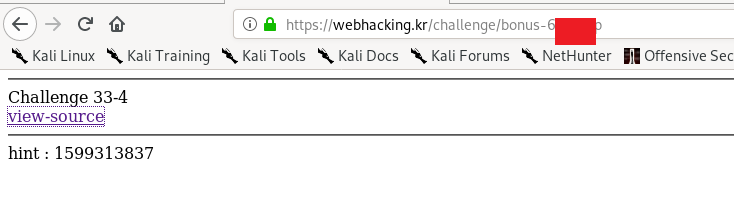
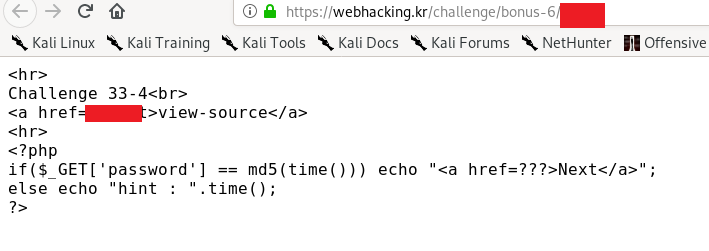
This challenge is a bit tricky where you have to refresh the page at the correct timestamp. My advice is to put the value with + 60 to 100 seconds delay. For example, the current timestamp is 1599313837, add 100 seconds makes 1599313937. After that, convert the delayed timestamp value using the following Linux command or online tool
echo -n 1599313937 | md5sum
Keep refreshing the page until you matched the timestamp on the hints.
Challenge 5
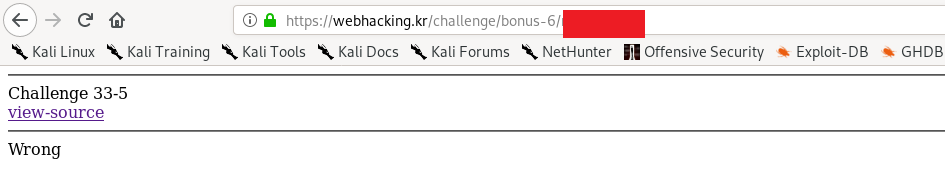
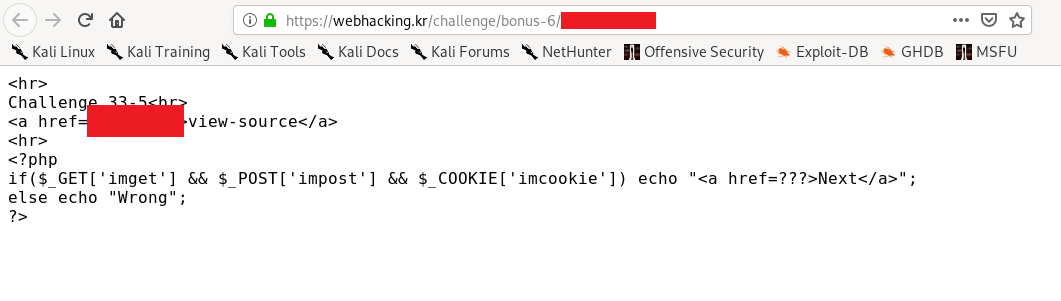
Similar to challenge 2, this time you have to submit a dummy cookie, GET and POST request.
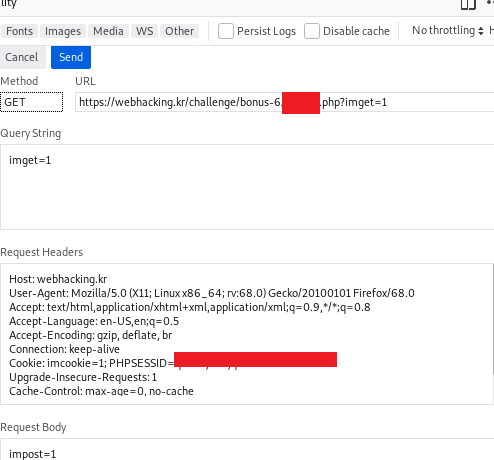
Double click the response and proceed to next level.
P/s: If the above method doesn’t work, try adding the cookie value manually to the browser.
Challenge 6
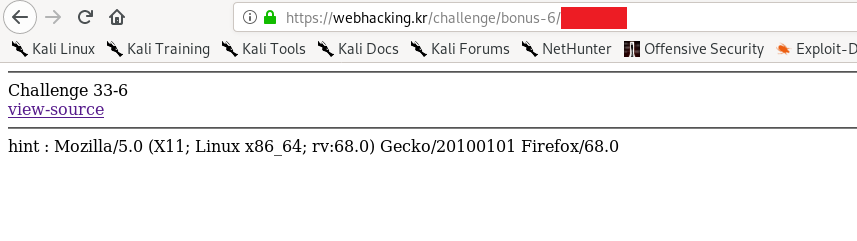
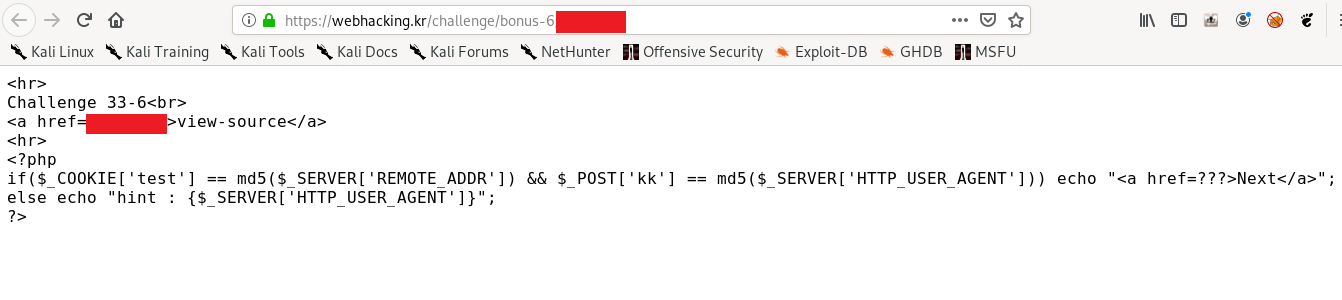
Similar to challenge 2 also but with cookie value test=md5(Remote ip address) and POST value kk=md5(user-agent).
Submit the request and double click the response and proceed to the next level.
P/s: If the above method doesn’t work, try adding the cookie value manually to the browser.
Challenge 7
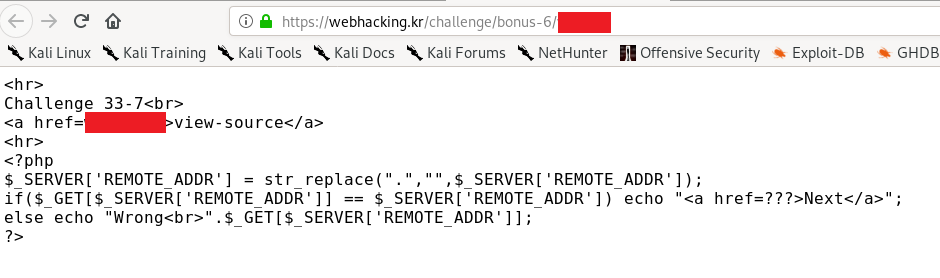
This challenge might be confusing if you are not familiar with PHP. This is a get request with the same naming and value. First of all, obtain your own public IP address via google. For example, my public address is 127.0.0.1 (just for demonstration purpose), removing the dot due to the replace function, we have 127001. The answer to the next level is
https://webhacking.kr/challenge/bonus-6/<reducted>.php?127001=127001
Challenge 8
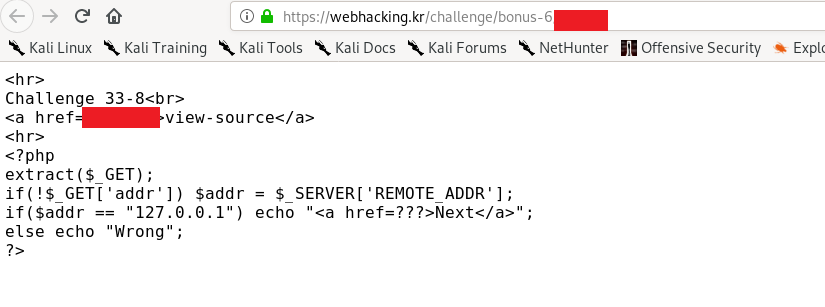
By default, the $addr is your public IP address. This challenge is simple, we can replace the $addr variable by sending a GET request.
https://webhacking.kr/challenge/bonus-6/<reducted>.php?addr=127.0.0.1
Challenge 9
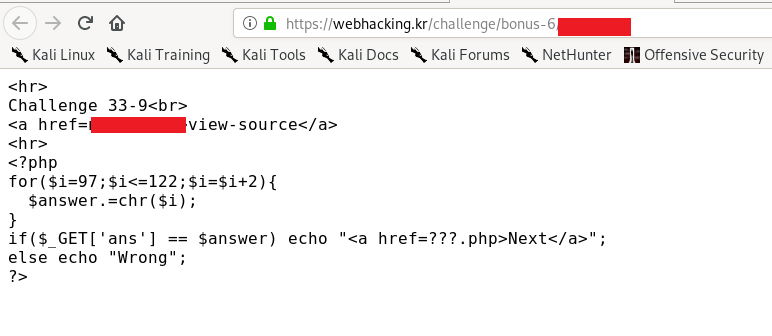
The answer is the converting the decimal number 97,99,101,103…121 to ASCII character.
Submit the answer in get request format.
https://webhacking.kr/challenge/bonus-6/<reducted>.php?ans=<The ASCII>
Challenge 10
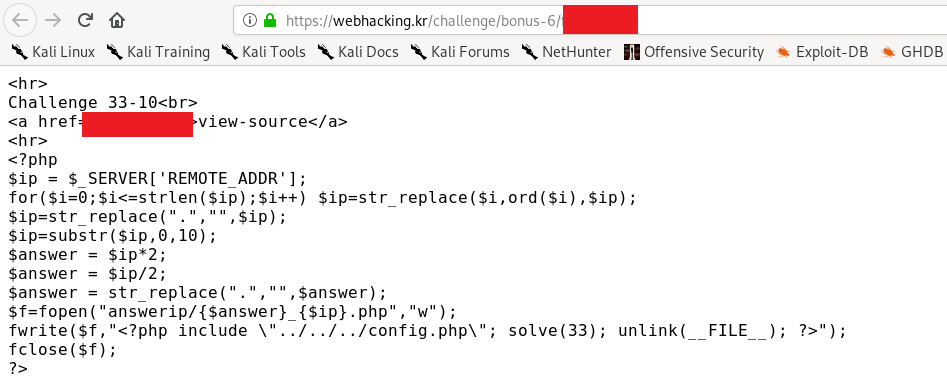
Let me explain the PHP code line by line
//server obtain your public ip
$ip = $_SERVER['REMOTE_ADDR'];
//A small loop to replace the ASCII numeric to decimal.
for($i=0;$i<=strlen($ip);$i++) $ip=str_replace($i,ord($i),$ip);
//Replace dot to nothing
$ip=str_replace(".","",$ip);
//obtain the first 10 characters
$ip=substr($ip,0,10);
//Some mathematic
$answer = $ip*2;
$answer = $ip/2;
//No more decimal
$answer = str_replace(".","",$answer);
//Write the flag on the designated php file
$f=fopen("answerip/{$answer}_{$ip}.php","w");
fwrite($f,"<?php include \"../../../config.php\"; solve(33); unlink(__FILE__); ?>");
fclose($f);
At the end of the challenge, we have to know the final value for $answer and $ip. Once we have both values, visit the following URL to complete the challenge.
https://webhacking.kr/challenge/bonus-6/answerip/<$answer>_<$ip>.php
P/s: If you are lazy, use an online compiler.
Phew, what a challenge.
tags: webhacking.kr - phpThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)