Webhacking.kr write-up: old-26
1 minutes to read| Link | point | tag |
|---|---|---|
| old-26 | 100 | PHP |
Howdy there, welcome back to another webhacking.kr CTF write-up. Today’s challenge involves with some PHP script.
There is nothing we can do for the front page. Let’s check the source code.
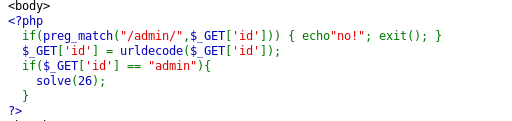
Key on the PHP script. To solve the challenge, we have to submit the GET request where ?id=admin. However, the keyword, admin is filtered by the script.
There is another notable urldecode() function which serves as an important aspect to complete the challenge. The URL code for admin is
%61%64%6d%69%6e
The above-encoded URL is directly recognized by PHP as ‘admin’ where the filter still valid. Also, the urldecode() serves no use at all. How about performing another URL encode?
%2561%2564%256d%2569%256e
Alright, the PHP unable to interpreted the above-encoded text to ‘admin’ anymore, since %2561 makes no sense. Since PHP is a sequential programming, with urldecode() function came after the filter, the above encoded text will be converted to %61%64%6d%69%6e or admin while bypassing the filter.
The final payload should be look like
?id=%2561%2564%256d%2569%256e%20
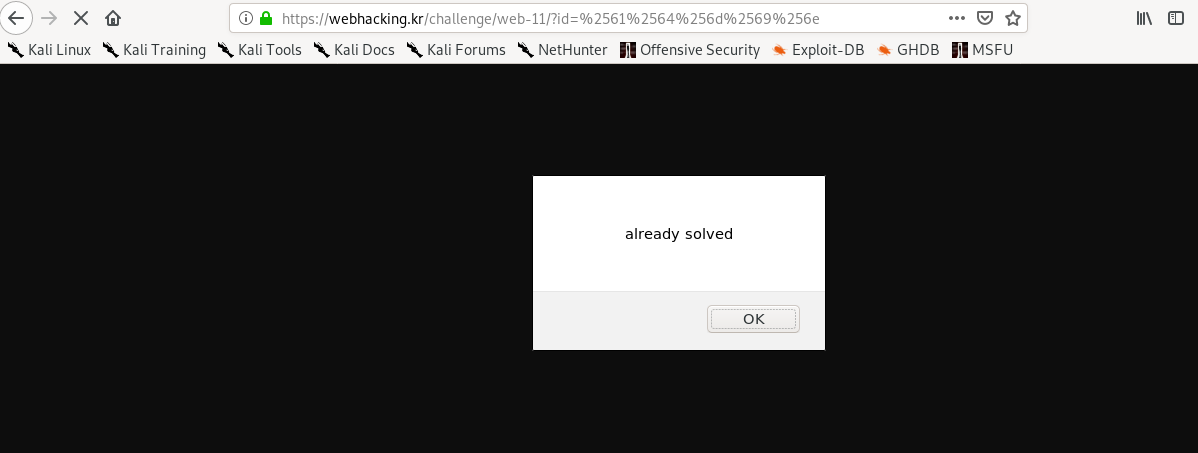
Thanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)