Webhacking.kr write-up: old-24
1 minutes to read| Link | point | tag |
|---|---|---|
| old-24 | 100 | PHP |
Welcome back for another webhacking.kr CTF challenge. Today’s challenge is about a simple PHP filter bypass.
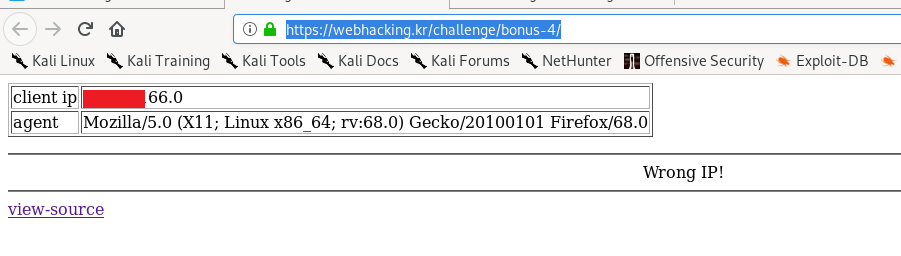
The front page shows my remote IP address and user agent. Let’s inspect the code.
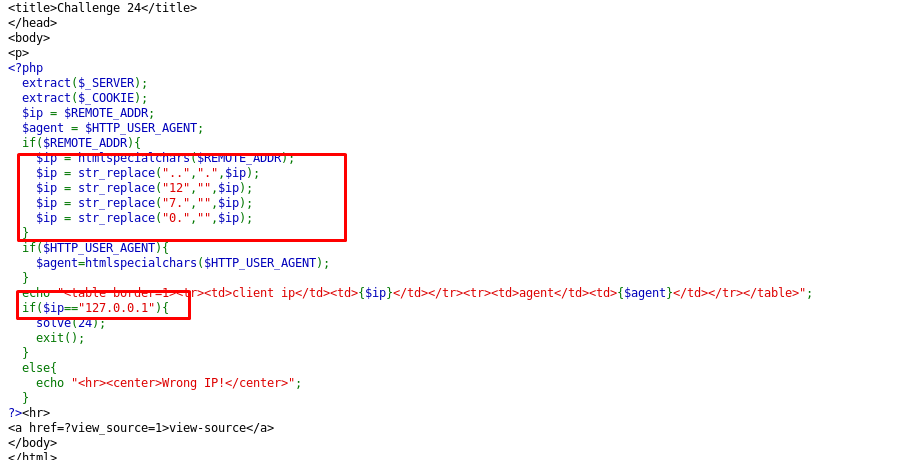
Referring to the code, the remote address has to be 127.0.0.1 or a local address to solve the challenge. Let’s put the local address issue aside first, how do we bypass the replacement filters? To bypass the filters, the $ip variable has to be
112277...00...00...1
The red labeled text will be replaced to nothing while the two dots (..) will be replaced by a single dot (.). In the end, we get 127.0.0.1 after the replacement.
Alright, let’s talk about the remote address. Since the input address is not a valid IP address, we can forget about the X-forward-for. However, if you noticed the source code again, you will notice the PHP script extract the $_SERVER as well as the $_COOKIE.
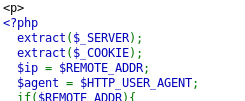
From there, we can replace $REMOTE_ADDR from $_SERVER[‘REMOTE_ADDR’] by assigning the same variable naming from the cookie.
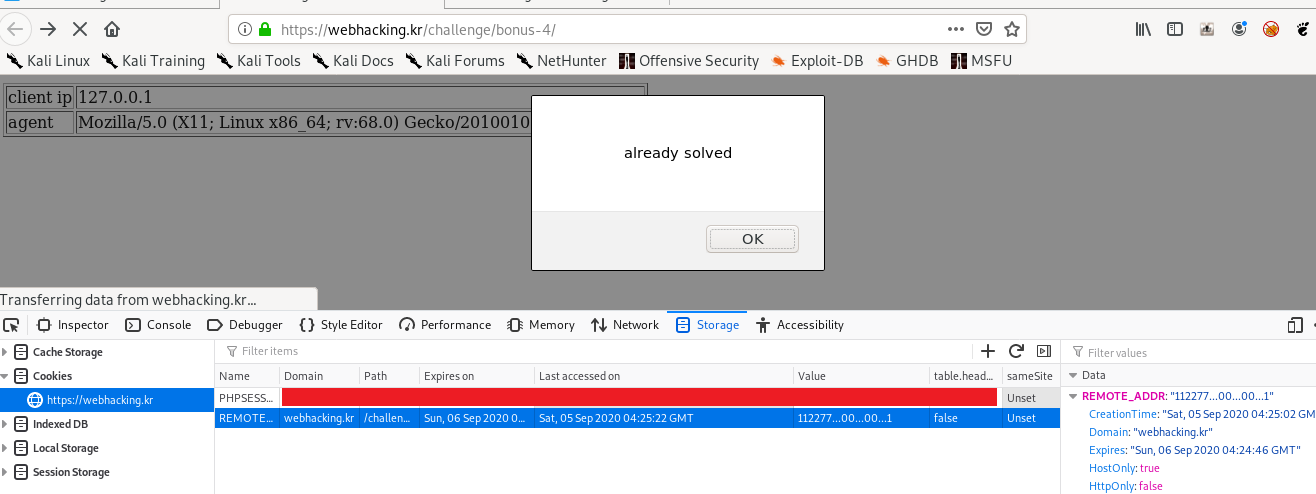
The $REMOTE_ADDR is actually from $_COOKIE[‘REMOTE_ADDR’].
tags: webhacking.kr - phpThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)