Webhacking.kr write-up: old-23
| Link | point | tag |
|---|---|---|
| old-23 | 200 | XSS |
Welcome back for more webhacking.kr CTF challenge. Today challenge is cross-site scripting (XSS)
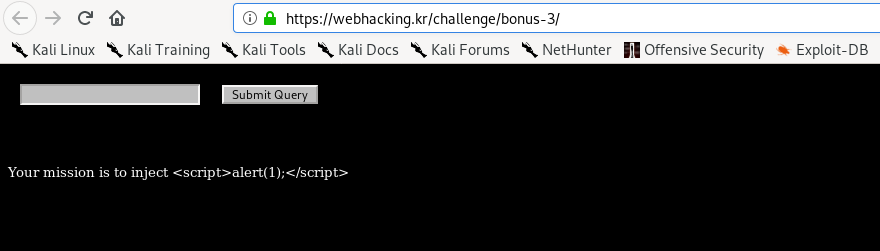
Your objective is to inject a simple XSS payload to the query (given by the challenge itself). However, the input has been sanitized or filtered where it only accepts a single alphabet but multiple special characters and numbers. To solve this challenge, I used the null-byte (x00) bypass. Since there is no way we can input the null byte on the input field, the best way is through the URL.
https://webhacking.kr/challenge/bonus-3/index.php?code=<s%00c%00r%00i%00p%00t>a%00l%00e%00r%00t(1);</s%00c%00r%00i%00p%00t>
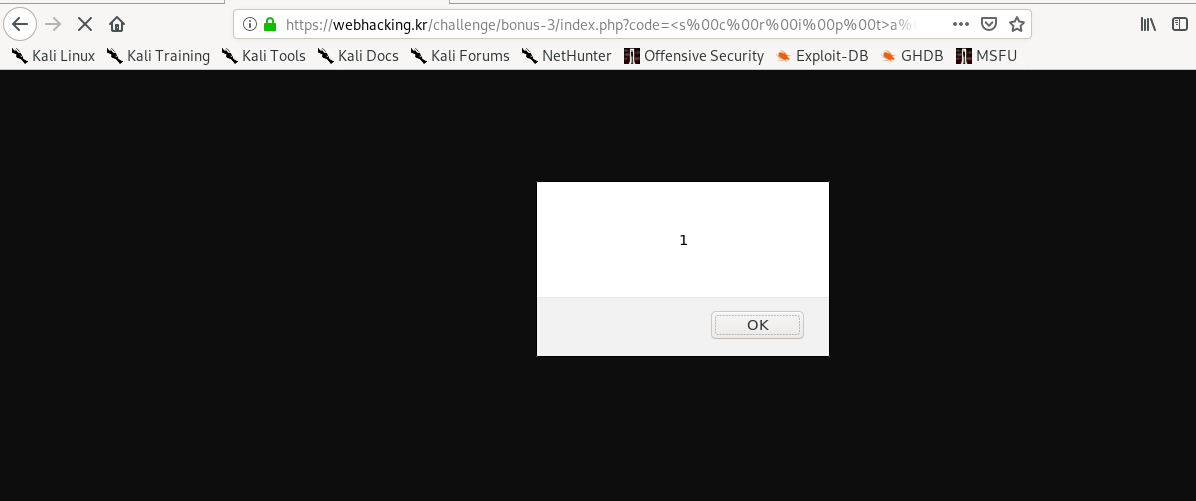
Thanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)