Webhacking.kr write-up: old-19
1 minutes to read| Link | point | tag |
|---|---|---|
| old-19 | 150 | Session Hijacking |
Hello, welcome back for more webhacking.kr CTF challenge. Today’s menu is session hijacking.
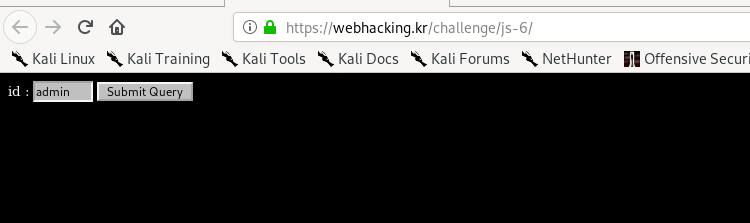
Alright, our main target for the challenge is to log in to the page as an admin. However, submitting the query returns the following result.
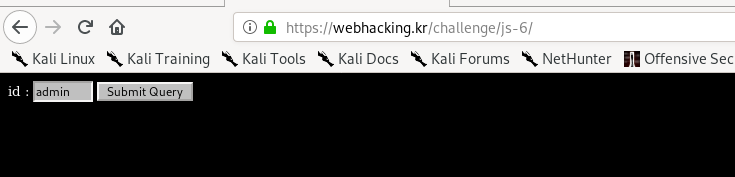
Everything is too good to be true. Try submitting another query with a different value and take a good look at the cookie.
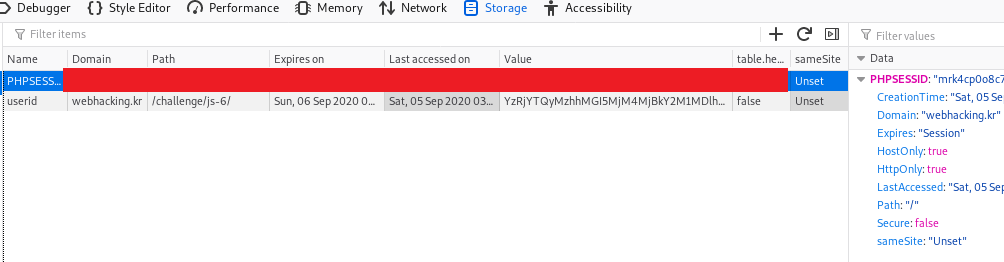
The userid contains a base64 encoded value. When doing another two good try, I came with the following outcome
| Input value | decoded cookie value |
|---|---|
| 1 | c4ca4238a0b923820dcc509a6f75849b |
| 2 | c81e728d9d4c2f636f067f89cc14862c |
| 12 | c4ca4238a0b923820dcc509a6f75849bc81e728d9d4c2f636f067f89cc14862c |
Guess you have noticed the pattern. It just a concatenate of the salted value of each input character. Since ‘admin’ is our targeted keyword, I had to submit ‘admi’ and ‘n’ in the query. In summary, the result looks like
| Input value | decoded cookie value |
|---|---|
| admi | 0cc175b9c0f1b6a831c399e2697726618277e0910d750195b448797616e091ad6f8f57715090da2632453988d9a1501b865c0c0b4ab0e063e5caa3387c1a8741 |
| n | 7b8b965ad4bca0e41ab51de7b31363a1 |
| admin | 0cc175b9c0f1b6a831c399e2697726618277e0910d750195b448797616e091ad6f8f57715090da2632453988d9a1501b865c0c0b4ab0e063e5caa3387c1a87417b8b965ad4bca0e41ab51de7b31363a1 |
Encode the salted cookie value to base64 format.
MGNjMTc1YjljMGYxYjZhODMxYzM5OWUyNjk3NzI2NjE4Mjc3ZTA5MTBkNzUwMTk1YjQ0ODc5NzYxNmUwOTFhZDZmOGY1NzcxNTA5MGRhMjYzMjQ1Mzk4OGQ5YTE1MDFiODY1YzBjMGI0YWIwZTA2M2U1Y2FhMzM4N2MxYTg3NDE3YjhiOTY1YWQ0YmNhMGU0MWFiNTFkZTdiMzEzNjNhMQ%3D%3D
Replace the userid cookie value with the above text, refresh the page and pwn the challenge.
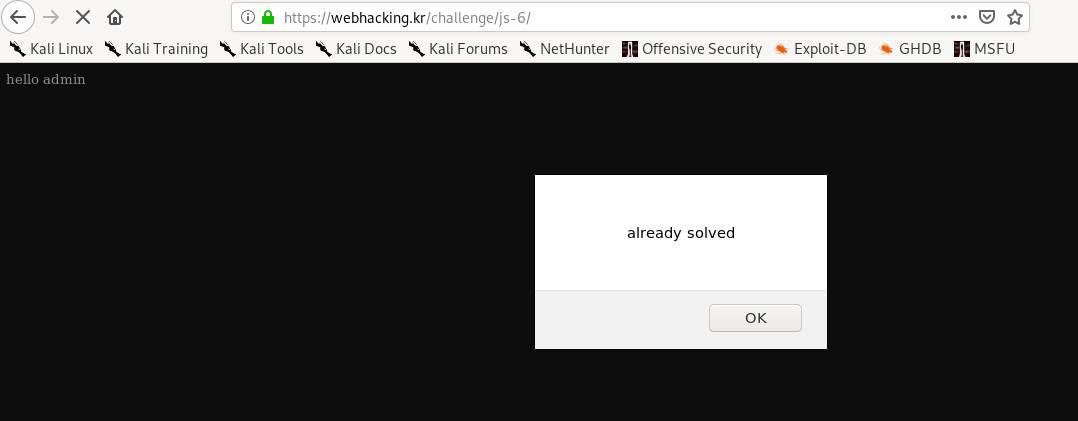
Thanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)