THM write-up: c4ptur3-th3-fl4g
4 minutes to read
Link: https://tryhackme.com/room/c4ptur3th3fl4g
This is yet another CTF challenge from tryhackme. This is my first blog post after the holiday and the challenge covers the very basic codes and hashes cracking. Hope you enjoy the write-up.
Task 1: Translation and shifting
This task required the challenger to perform a translation or shifting certain ciphers such as ROT13, ROT47, Morse code, etc.
Task 1-1: Leet a.k.a l33t
Leet is a form of font which is used mostly on the internet. Is a famous font used by numerous hackers.
This is a straight forward task, you can guess the answer easily. Or, using this converter.
Task 1-2: Binary to ASCII
Binary is a type of machine language.
Copy the cipher code into the converter.
Task 1-3: Base32
Base32 is a common transfer encoding. It consists of 32-char set. These char-sets are usually alphabet in uppercase.
Put the cipher code into the converter
Task 1-4: Base64
Base64 is another common transfer encoding. It consists of 64-char set. These char-sets are usually alphabet in uppercase and lowercase.
Put the cipher code into the converter
Task 1-5: Hex to ASCII
Hex consists of 16 bits of binary. It is also known as base16.
Copy the cipher into the converter
Task 1-6: Rot 13
Rot 13 or known as rotate 13 is a form of Caesar cipher which rotate in 13 times.
Punch in the cipher into the converter
Task 1-7: Rot 47
Rot 47 or known as rotate 47 is another form of Caesar cipher which rotate in 47 times. It encode almost all visible ASCII character.
Copy the cipher into the converter
Task 1-8: Morse code
Morse code is a combination of signal made of short and long impulsion (dot and dash). It was designed for telecommunication.
Put the cipher into the converter
Task 1-9: BCD to ASCII
Binary-Coded Decimal (BCD) is a base10 encoding technique.
Punch in the cipher into the converter
Task 1-10: Multiple cipher
This task consists of multiple ciphers. Challenger required to decode the cipher from the previous task
- Cipher1: Base64
- Cipher2: Morse code
- Cipher3: Binary to ASCII
- Cipher4: ROT 47
- Cipher5: BCD to ASCII
Task 2: Hashes
A hash can be cracked using hashcat either by brute force or dictionary. However, it is not a 100% guarantee that the hash can be cracked using the hashcat. For this task, the author suggested using a brute-forcing. However, it is impossible as the permutation is too large and it will take more than a day. The only way to do that is to decrypt it using online tools such as md5decrypt. This is because the hashed text has been stored in their database.
Task 2-1: MD2
This task can be done using this online tool.
Task 2-2 to Task 2-7
From this task onward, the hashes can be cracked using md5decrypt.
- Task 2-2: MD4
- Task 2-3: MD5
- Task 2-4: NTLM
- Task 2-5: SHA512
- Task 2-6: SHA256
- Task 2-7: SHA1
Task 3: Spectrogram
This task is easy. Just download any sound or wave analyzer tool such as aducity. For this task, I going to use wavepad. Simply open the downloaded wave file and open it up in TFFT (Tool > TFFT). A message will be revealed.
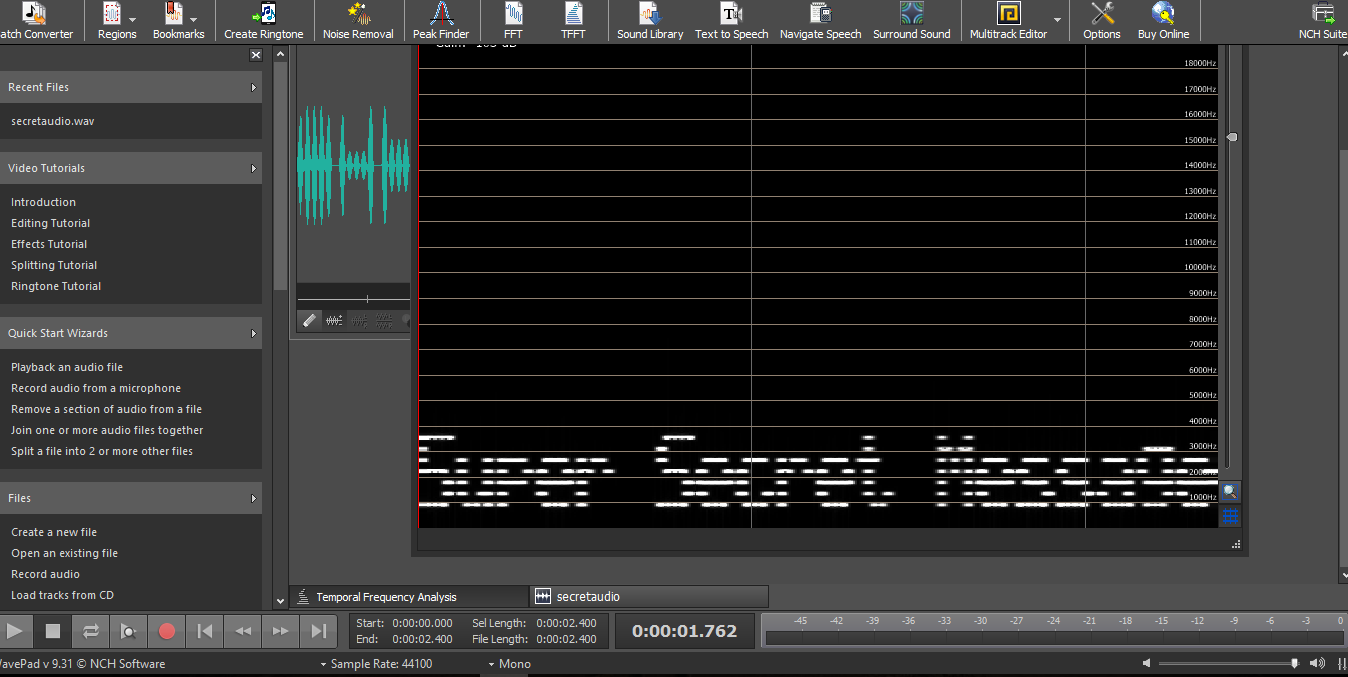
Task 4: Steganography
This task can be solved either by an online tool or steghide. I prefer steghide. The hidden file within the image can be extracted using the following command
steghide extract -sf stegosteg.jpg
After that, a file named steganopayload2248.txt will be extracted from the image as shown in the figure below.
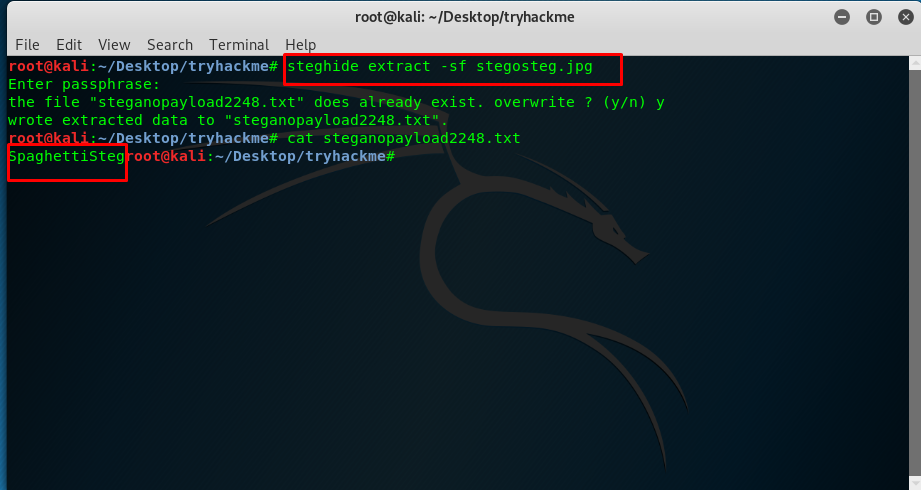
Task 5: What is inside the file?
This task cannot simply be solved by steghide. There is another dumb way to do it which is open the file as a txt. Both answers for the task is on the last few paragraphs.
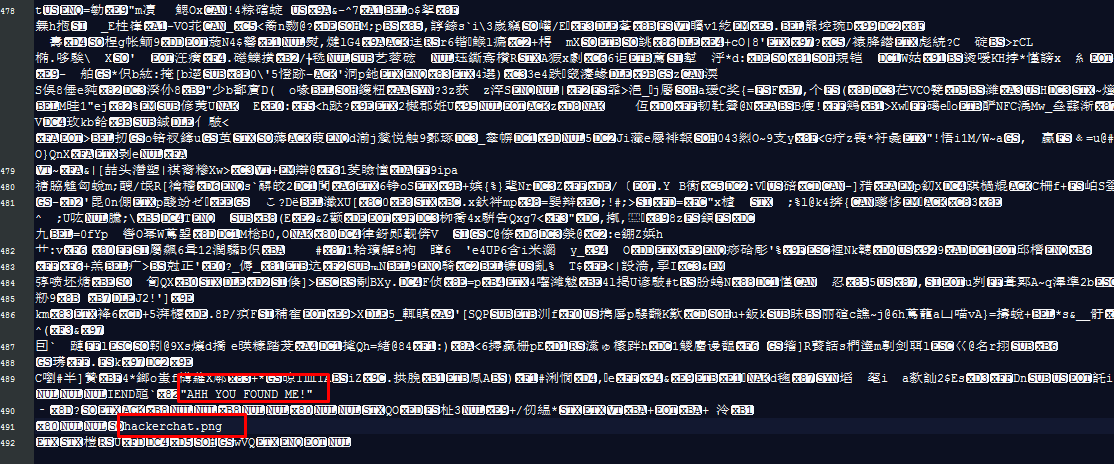
You can use ‘strings’ command in Linux too.
Conclusion
Task 1 is enlightening me as it covers more on basic of ciphering. However, Task 2 is a little bit of disappointed as the description made some confusion for beginners. Other than that, well done to the creator of the room. That’s all for my second CTF challenge, until next time!
tags: tryhackme - CTF - stego - hashThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)