Short CTF: hackertest
11 minutes to read
Hackertest is an online hacker simulation with 20 different levels. Each level requires a unique skill to complete with. At the end of the challenge, you should have you JS, PHP, HTML, and even critical thinking skill getting improved. Have fun!
- Level 1
- Level 2
- Level 3
- Level 4
- Level 5
- Level 6
- Level 7
- Level 8
- Level 9
- Level 10
- Level 11
- Level 12
- Level 13
- Level 14
- Level 15
- Level 16
- Level 17
- Level 18
- Level 19
- Level 20
Level 1
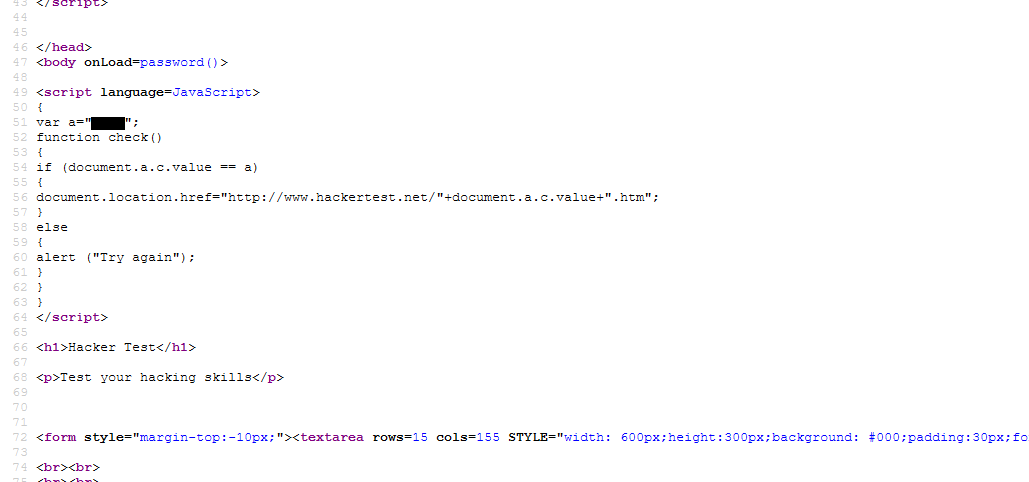
The first level’s password is located inside the JS script source code. Remember, the parameter of variable a is declared as some sort ASCII, do not confuse with the real NULL
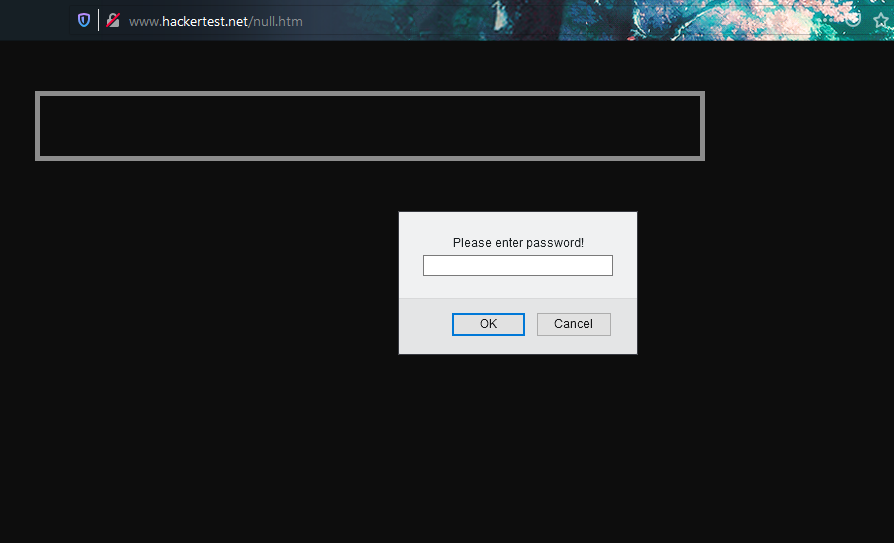
Parse the parameter and proceed to next Level.
Level 2
On the first arrival, you will be greeted by a password text box. Simply ignore the text box by clicking cancel and check the source code.
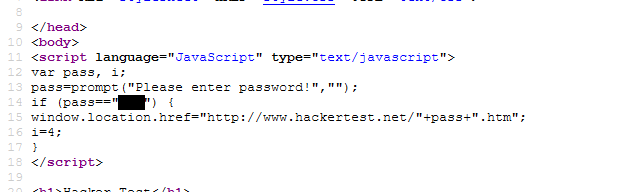
Similar to the previous level, the password is located inside the script. Refresh the page and enter the password.
Level 3
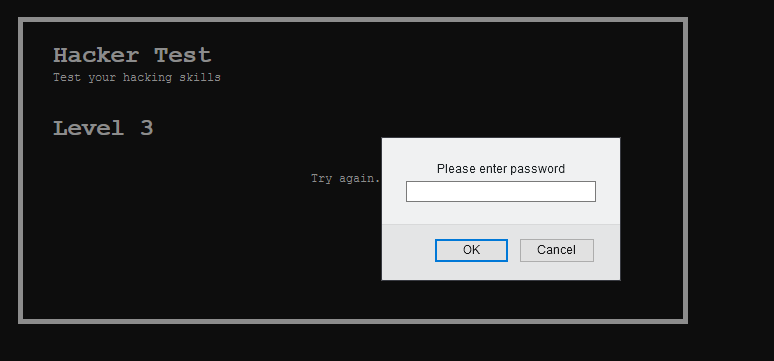
Yet another text box, guess you knew the drill. Ignore the text box by clicking cancel. After that, check the source code.
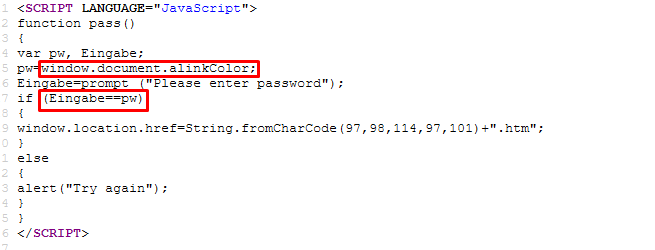
The password is on the pw variable and somehow we need to know the value of alinkColor. The task can be easily solved by using a console, simply type
window.document.alinkColor;
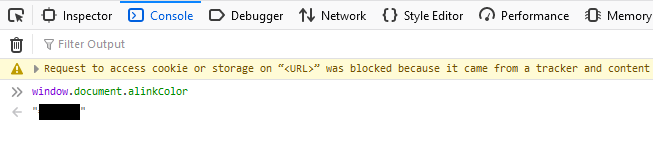
The link color is black.
Level 4
Level 4 is skippable.
Level 5
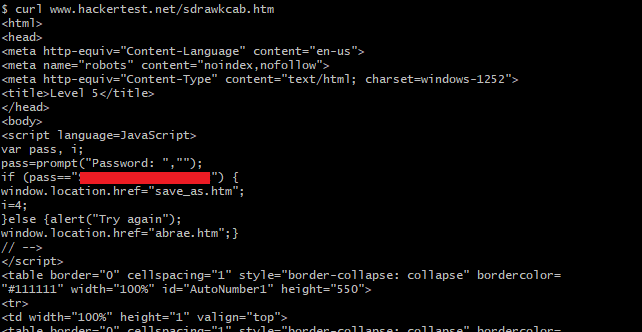
For this level, you can’t simply ignore the text box where it will take you back to the previous stage if you try to ignore it. There is numerous way to solve this challenge and my approach is using curl command.
Level 6
As usual, ignore the text box and check the source code.
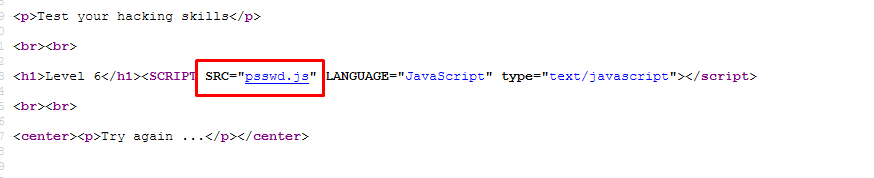
Guess what! The password is inside the .js file. That is all you need to know.
Level 7
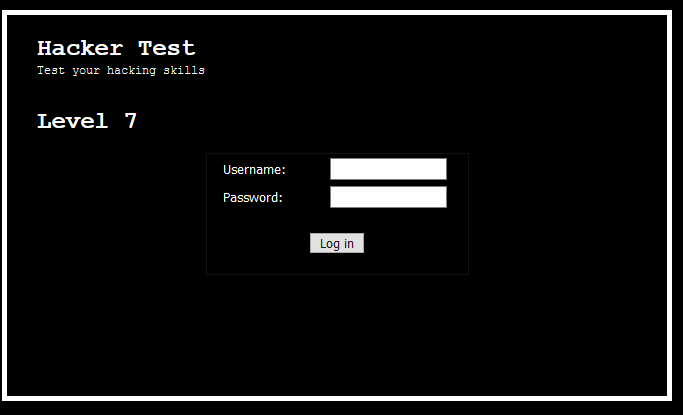
A login form, cool! If you are going to brute-force or using sqlmap on the login form, you are going way too far. The answer is in the source code which can be missed easily.
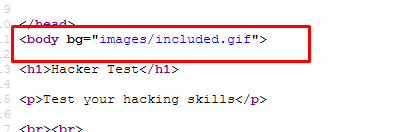
Yes, I’m talking about the GIF file. The credential is within the file, bottom right.
Level 8
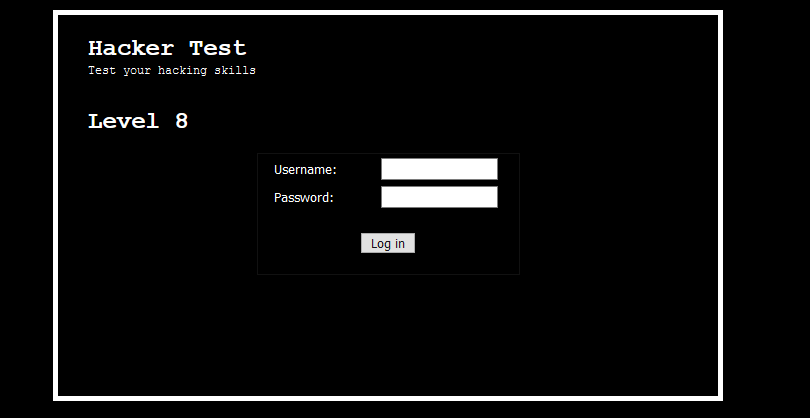
Another login form and this time nothing can be missed in the source code or does it? If you try to login with the wrong credential, you will be present with a page.

Check the source code and you will notice something familiar.
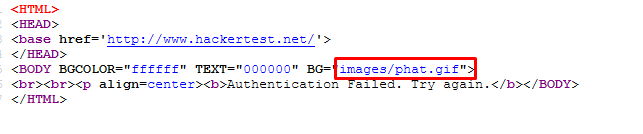

After that, look at the bottom right. a hint about .psd file. The file can be download using the following url.
http://www.hackertest.net/images/phat.psd
By using an online photoshop tool, remove all the watermark to reveal the credential which located on the bottom right.
Level 9
Level 9 is rather an easy level throughout the entire hackertest. The password is encoded in base64 and somehow located at the bottom of the source code.
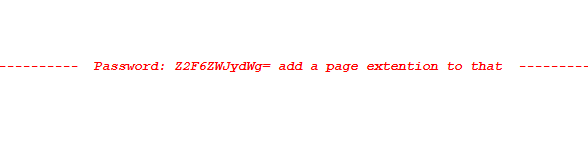
Decode the base64 and the next Level challenge is located at
http://www.hackertest.net/(decoded base64).php
Level 10
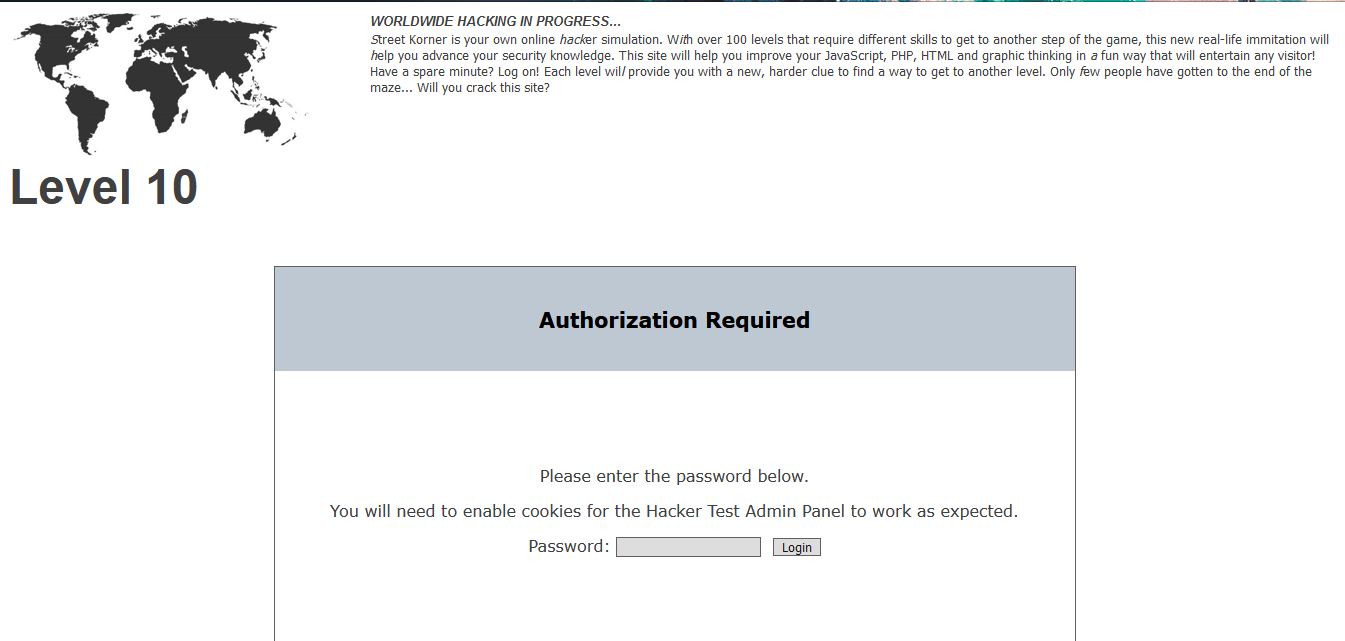
Look, we got a brand new interface. First of all, do not let the instruction fool you out as critical thinking skill is required to solve this challenge. If you tried to look at the description inside the source code, something is off.
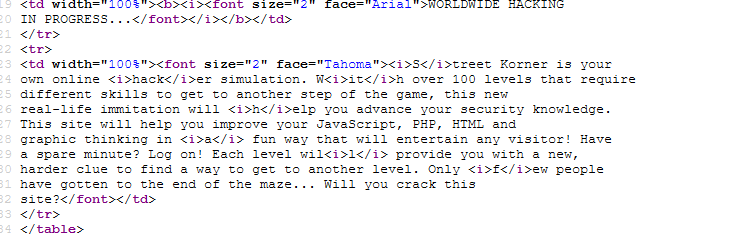
Some of the word or letter is italic. Combine those letters and you should obtain the password for the challenge.
Note: The password is in lower case, including the first letter.
What’s happening? An empty page? Tried check with the source code.
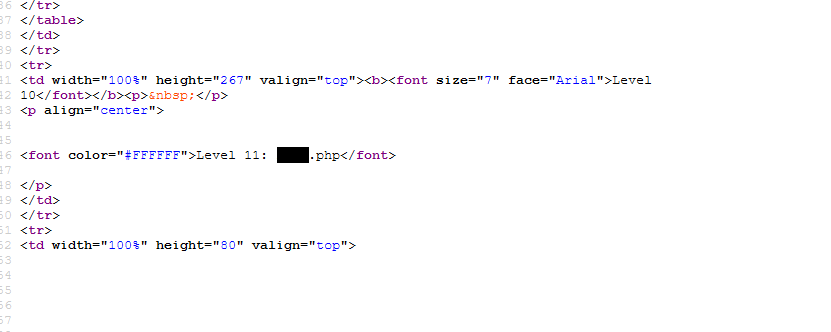
Visit the hidden page for next level.
Level 11
What are you looking at? Source code?
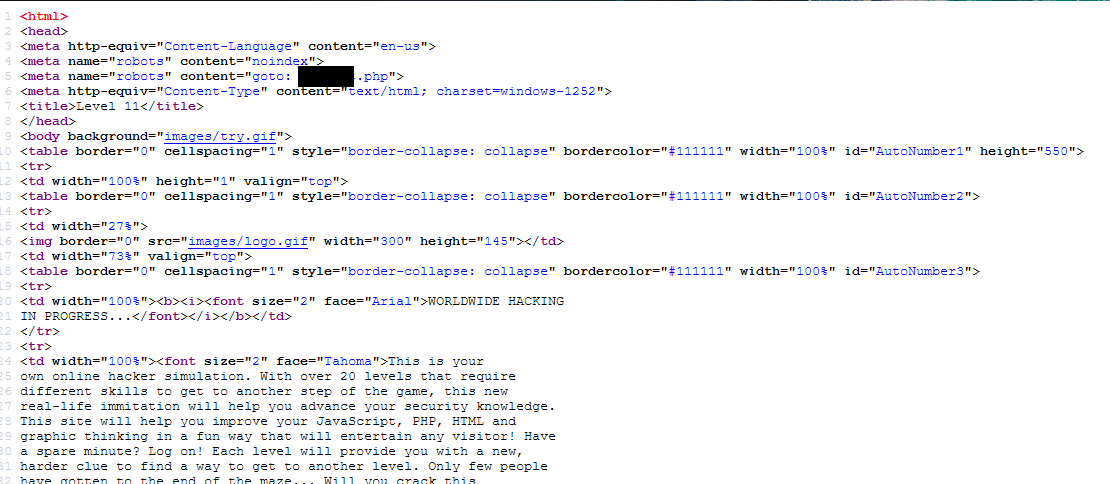
Yup, inside the source code.
Level 12
If you compared the logo to the previous page, we have a JPG logo instead of a GIF. Those are the 3 letters mentioned on the page. Something must be hidden inside the JPG file.
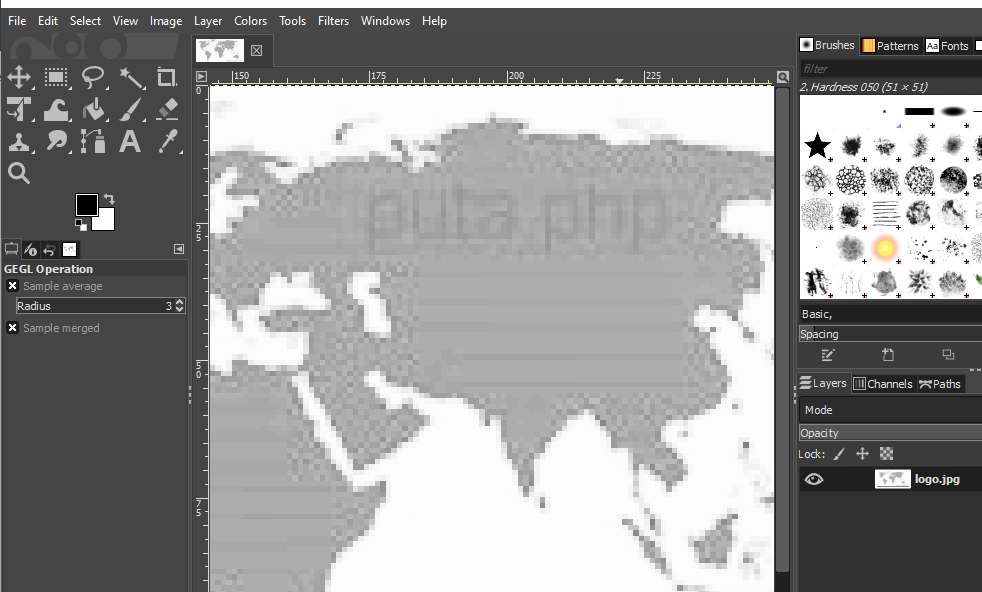
Playing around with the contrast and shadow. You’ll notice there is something on the Russian continent. It is a bad Spanish word.
Level 13
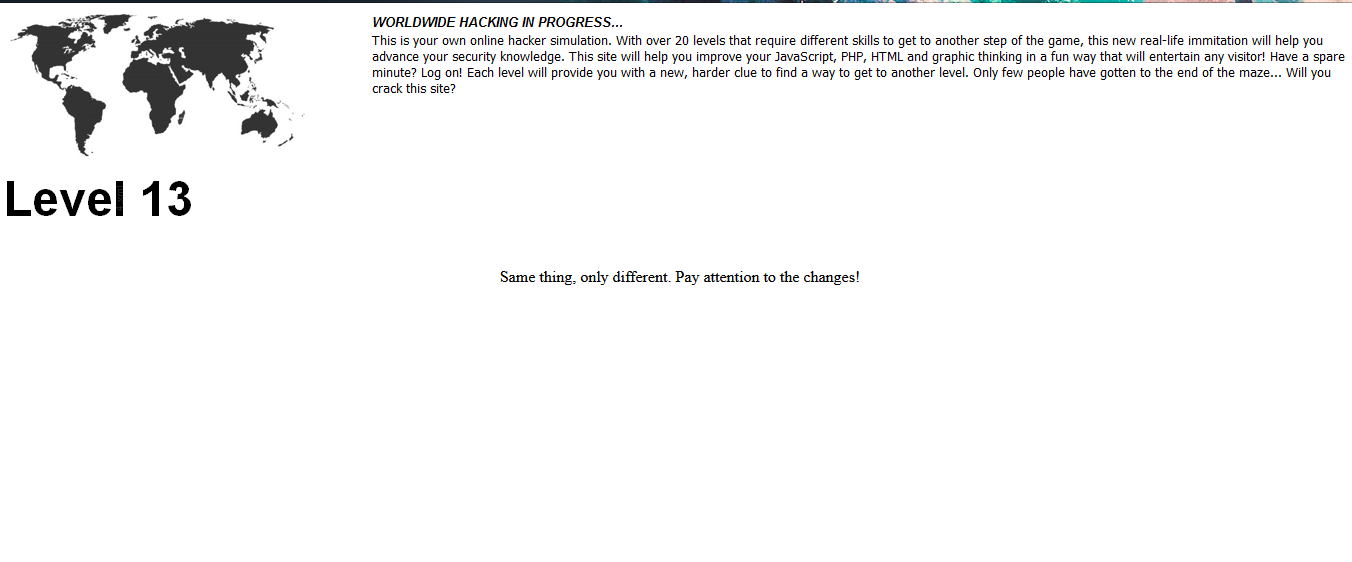
Similar to the previous level, check the hidden .php inside the given image. The image needs to investigate is the word ‘Level 13’ itself.
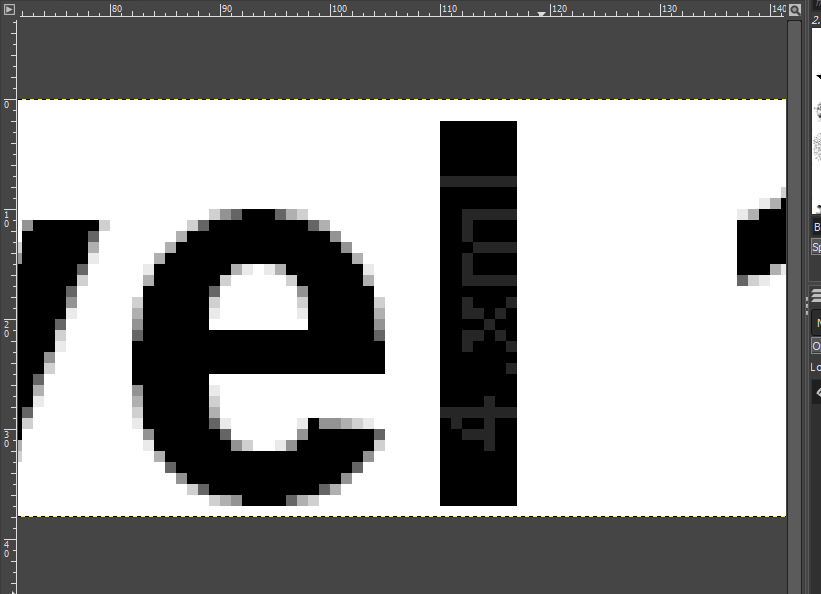
An XML file huh. Well, the next level hint is inside the file.
Level 14
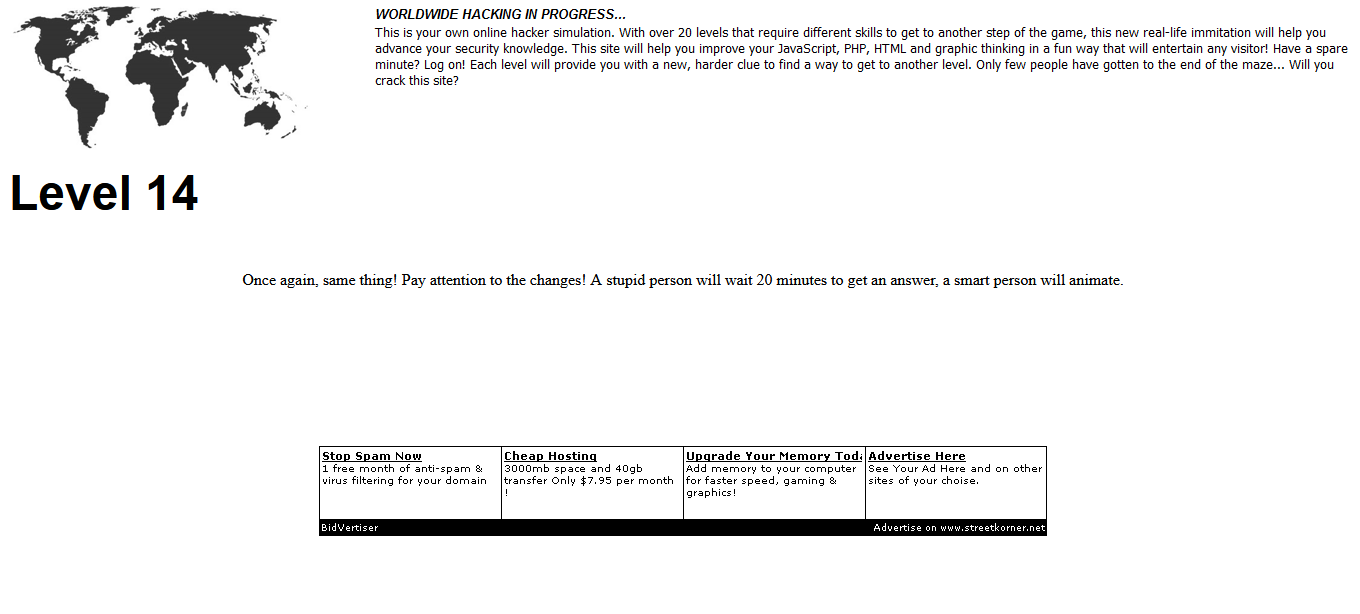
I’m freaking love this level because I was getting troll so hard by the advertisement GIF. You can either wait for 20 minutes for the gif to show you the answer or simply complete the challenge using GIMP.
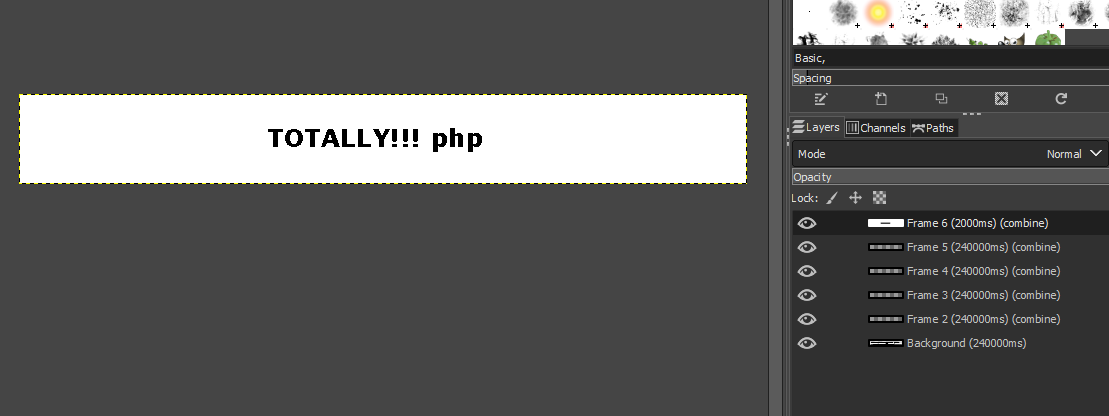
The next level PHP is on frame 6 which only shows after 20 minutes of static animation. The next level is totally.php
Level 15
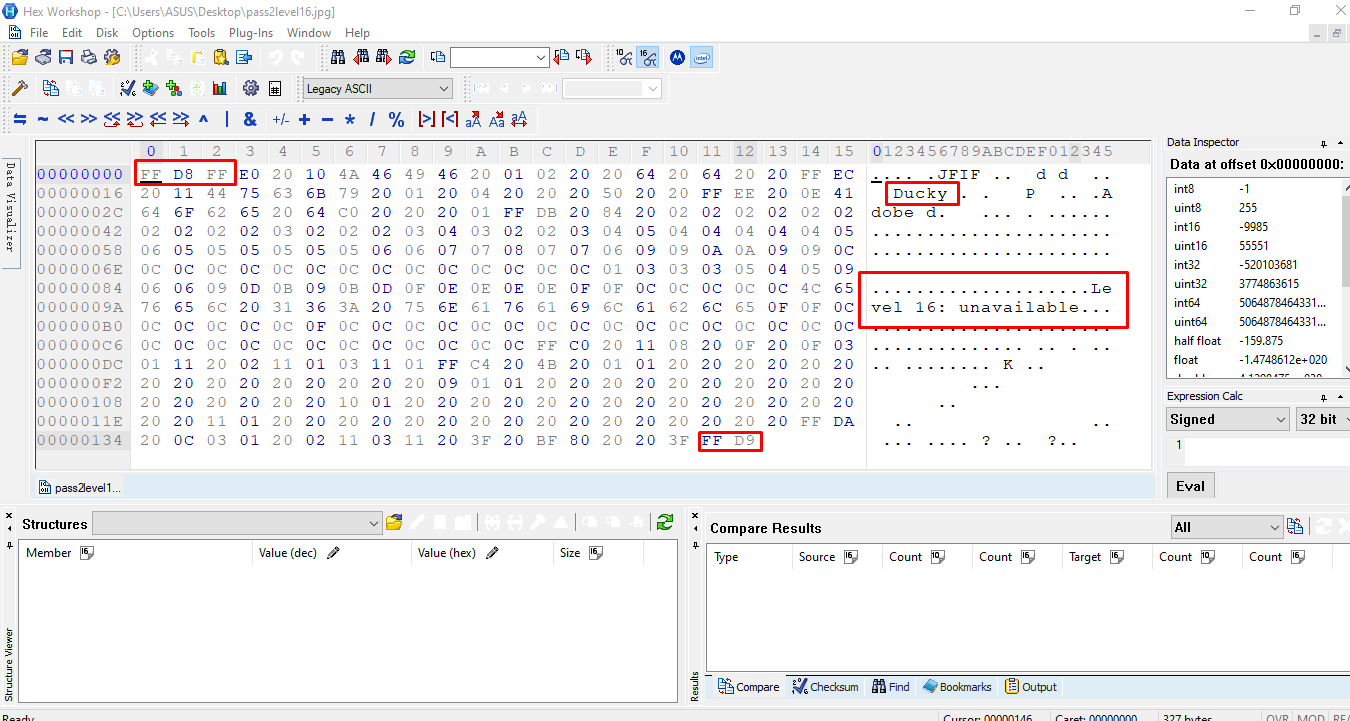
Upon clicking the link, we will receive a broken JPGimage. After investigating the image using hex edit, the header and footer of the image are correct. However, the content seems to be corrupted and there are two hints on the broken JPG.
- Ducky
- Level 16: unavailable
Ducky.php does not yield any good result. However, /unavailable (without extension) lead to the following page
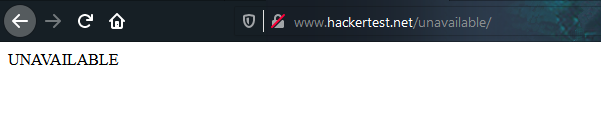
As for the source code
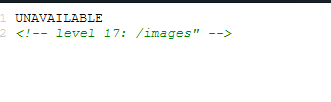
I’m guess level 16 is not actually broken after all. It just another trick.
Level 16
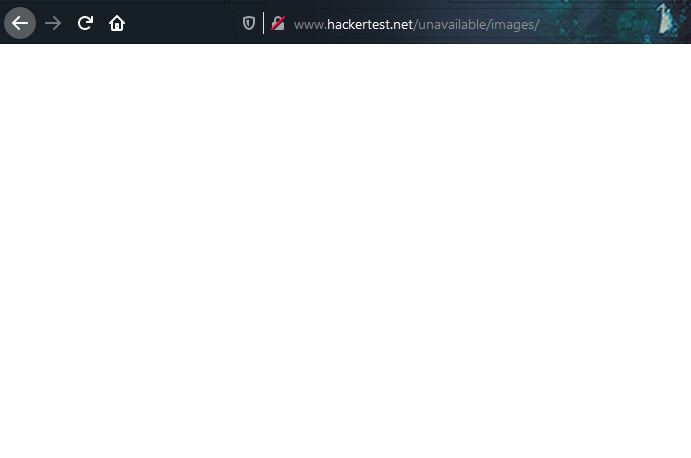
An empty page! Let see what is inside the source code.
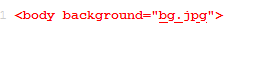
A JPG, let’s check that out.
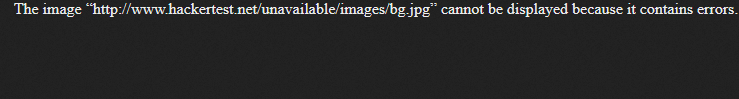
Shoot! Another broken image. Time for another hex edit.
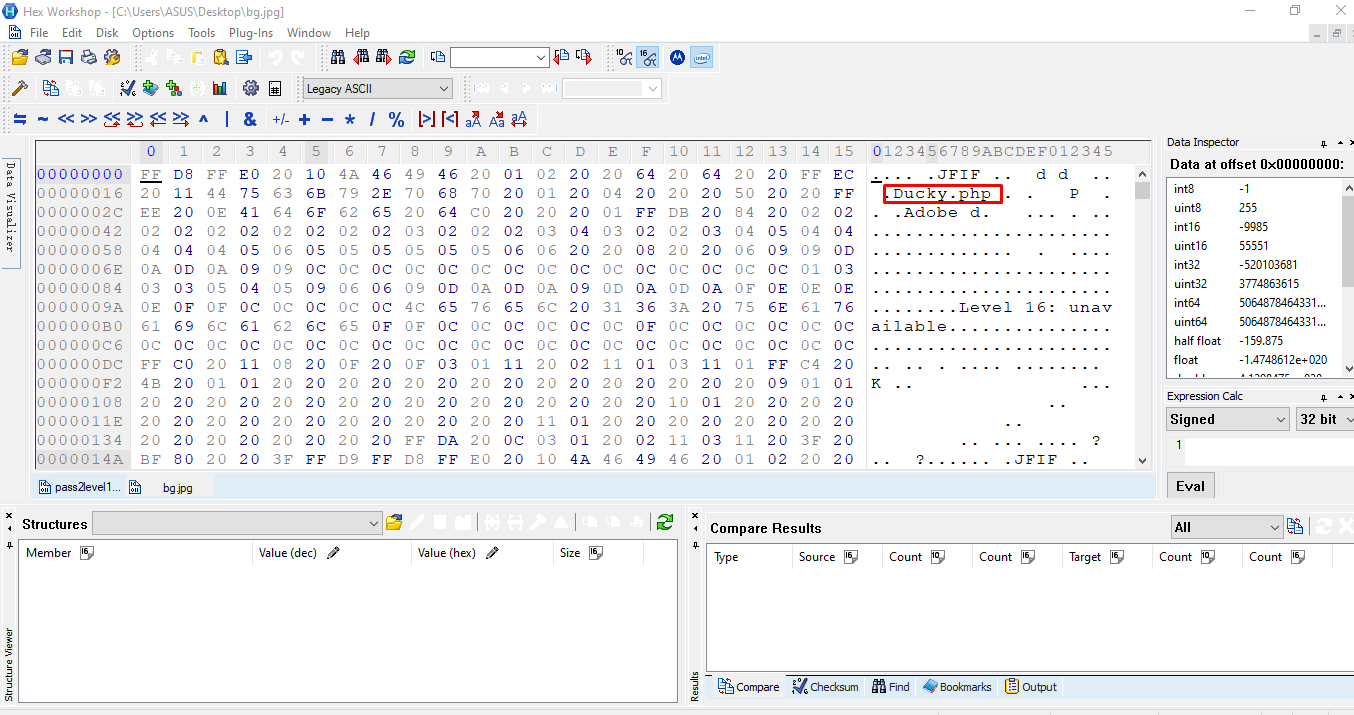
The next location is ducky.php under /unavailable directory. That is why we can’t reach it in the first place.
Level 17
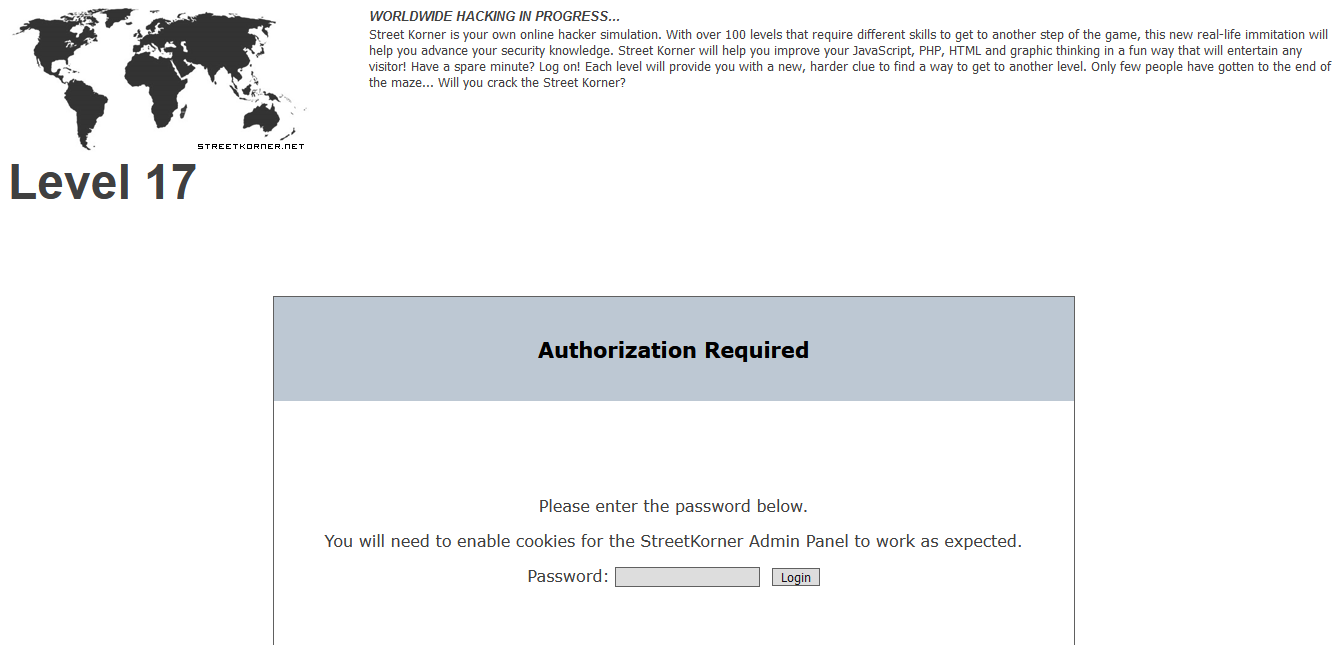
Deja-vu? Actually not. There is a hidden text in white color. You can either highlight the whole page using ctrl-a or check the source code.
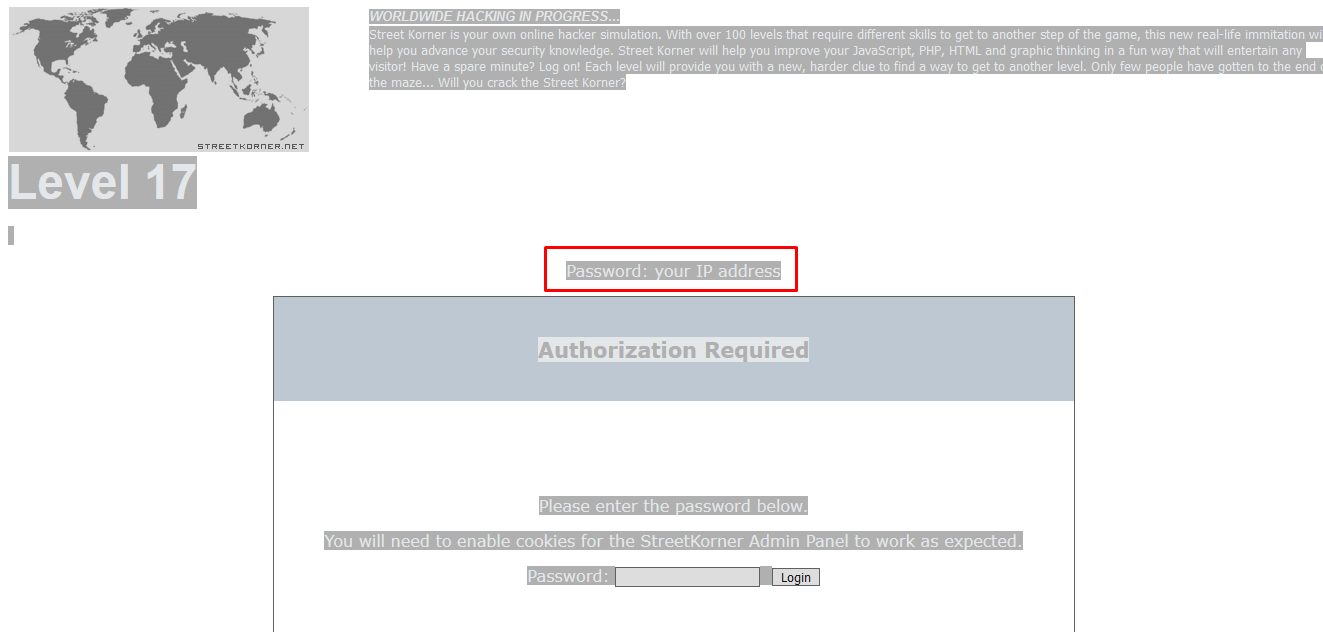
Just google your own IP address and solve the level. Easy!
Note: Level 18 is on upper level directory which is not inside the /unavailable directory.
Level 18
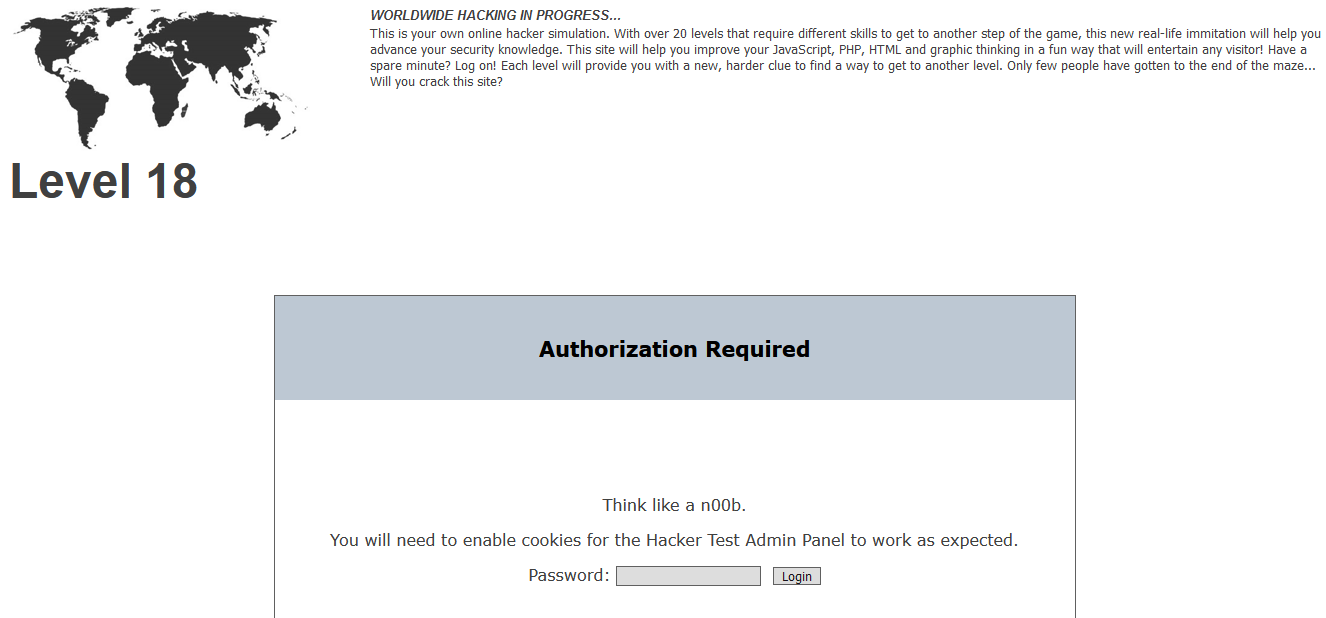
Check the error code at the bottom of the page, eventhough the error is not an actual error.
Level 19
Well, I can said the level is similar to level 14. Check out the level20_pass.gif. GIMP solve everything.
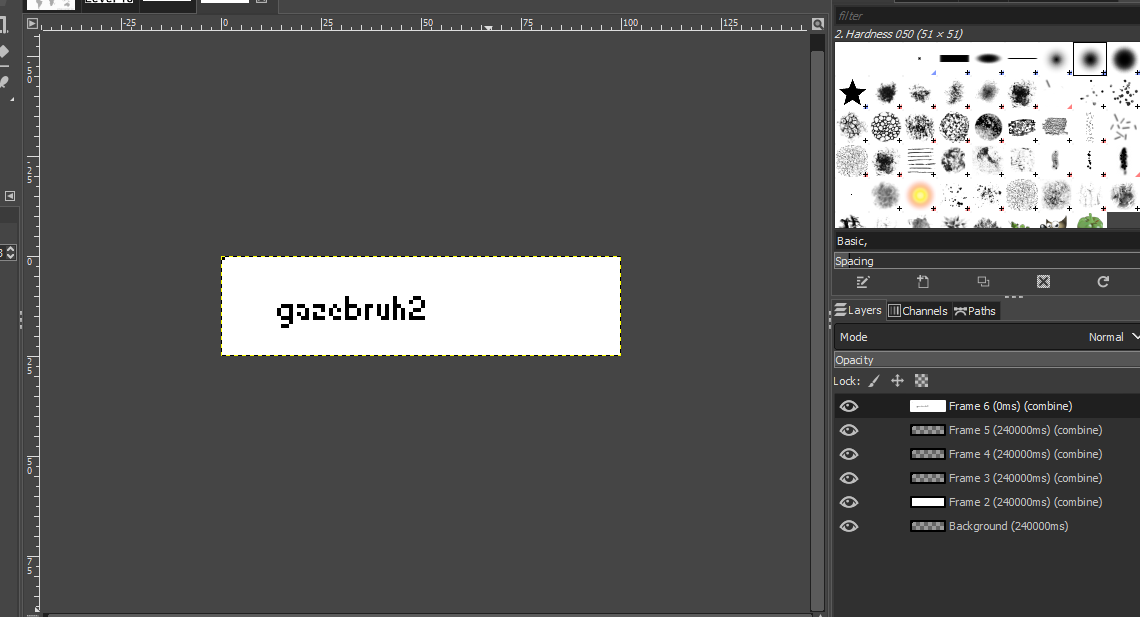
0 second show time, you will never get it. The final level is gazebruh2.htm Took me some time to brute force it.
Level 20
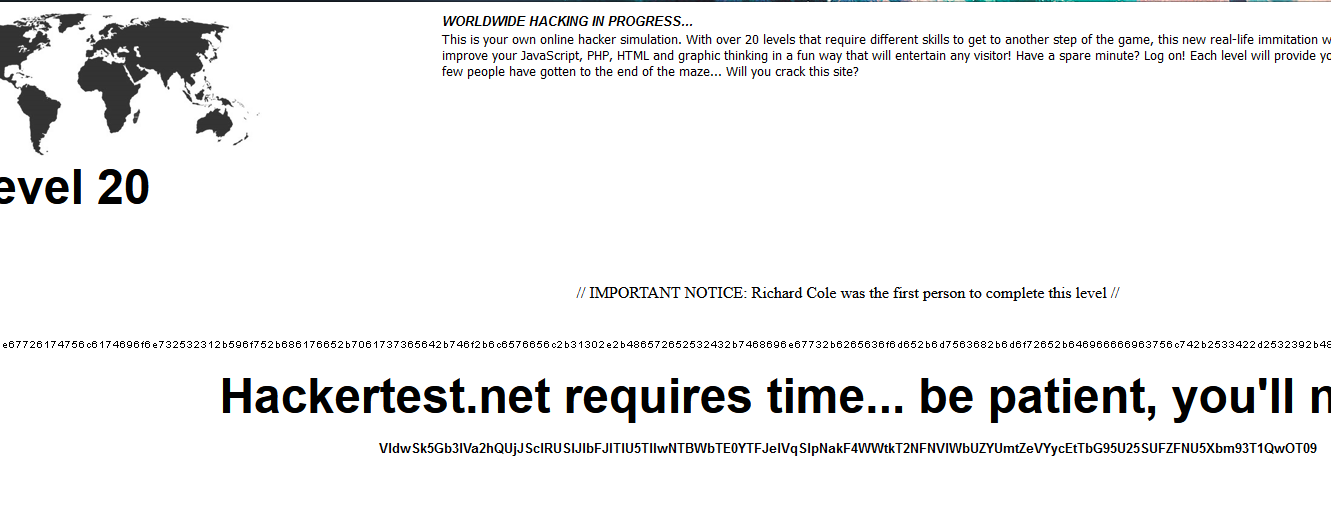
Time for the final boss. There are few things I wanted to check with.
ASCII
The ASCII on the page
436f6e67726174756c6174696f6e732532312b596f752b686176652b7061737365642b746f2b6c6576656c2b31302e2b486572652532432b7468696e67732b6265636f6d652b6d7563682b6d6f72652b6469666663756c742b2533422d2532395b486f70652b796f752b6765742b7468726f7567682532312b456e6a6f792e
is translated as
Congratulations%21+You+have+passed+to+level+10.+Here%2C+things+become+much+more+diffcult+%3B-%29[Hope+you+get+through%21+Enjoy.
Nothing special, just some encouraging words.
Base64
This is a multi encoded base64
VldwSk5Gb3lVa2hQUjJSclRUSlJlbFJITlU5TlIwNTBWbTE0YTFJelVqSlpNakF4WWtkT2NFNVlWbUZYUmtZeVYycEtTbG95U25SUFZFNU5Xbm93T1QwOT09
which decoded as
Go to www.streetkorner.net/gb now.
By the way, the domain is empty.
Hidden text
Highlight the entire page using ctrl-a or check the source code reveal the hint for the challenge.
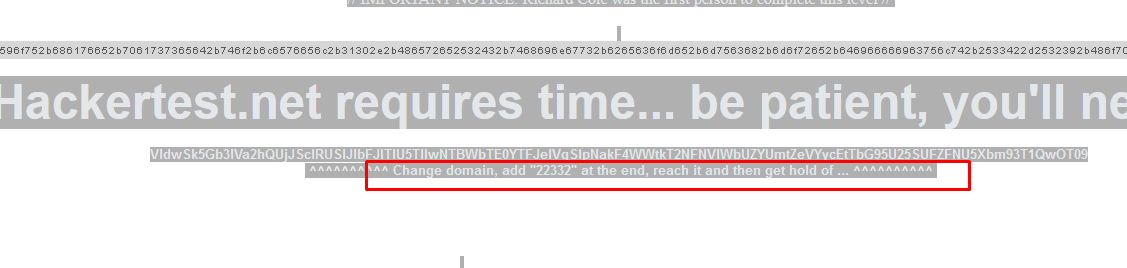
The hint has something to do with the link we just found out earlier. From
www.streetkorner.net/gb
to
www.hackertest.net/gb22332
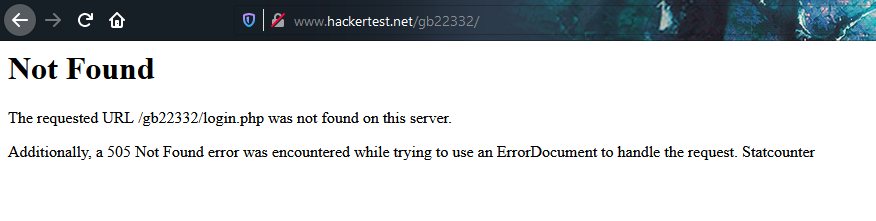
We got something out of ordinary, 505 is HTML version not support and I was able to access the site all the time but now? After checking the source code, I found some interesting stuff.
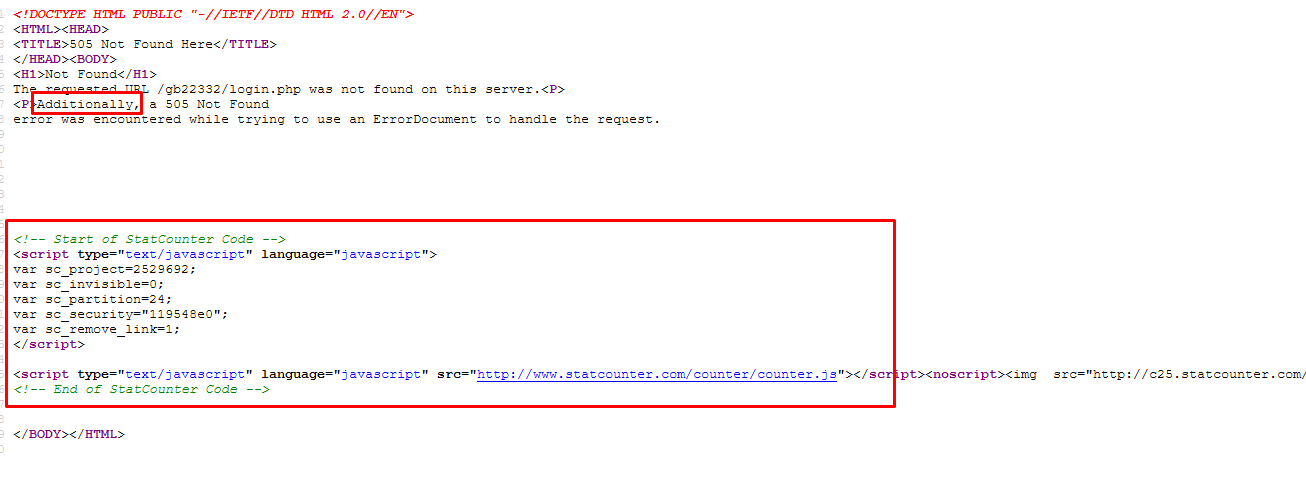
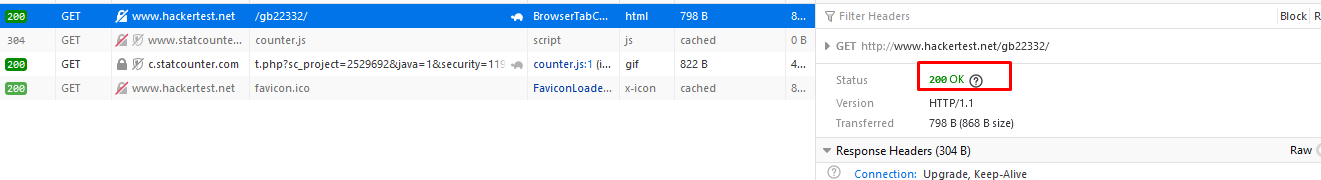
The StatCounter code is within the page. In short, this is not a genuine error page. The status code is 200, not an actual 505. Something is off.
How about
www.hackertest.net/505
Yes, the 505.
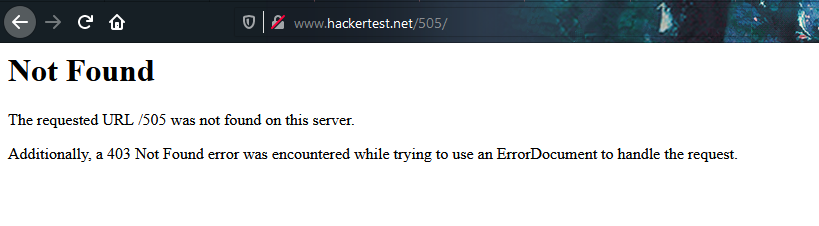
Can’t fool me this time, the next URL is
www.hackertest.net/505/403

The answer is 42, if you google the statement. The next URL is
www.hackertest.net/42.php
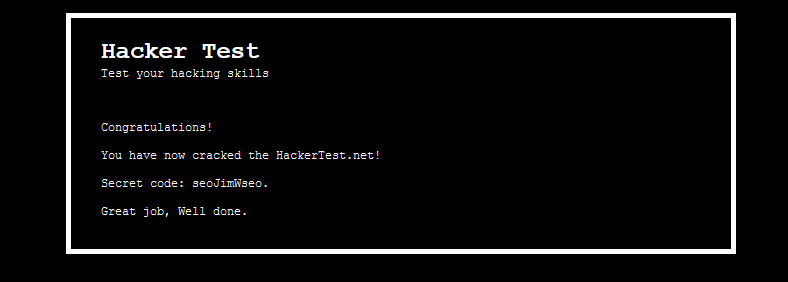
That’s it, we just finished the hackertest. What a journey!
tags: php - js - critical_thinkingThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)