CTFLearn write-up: Forensics (Medium)
5 minutes to readHello there, another welcome to another CTFlearn write-up. As for today, we are going to walk through the Medium level forensics. Let’s do a quick start.
1) 07601
Link: https://ctflearn.com/challenge/97
This one is simple. First of all, let’s check the hidden files using the binwalk.
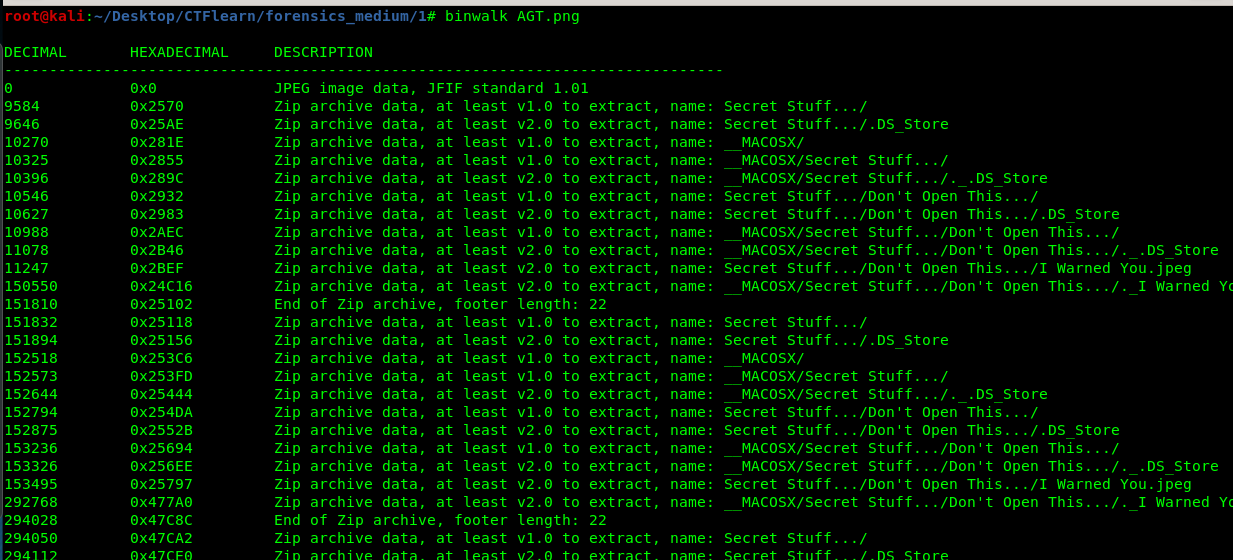
We have a lot of stuff inside the image file. Without thinking twice, extract all the files with the following command.
binwalk --extract --dd=".*" AGT.png
The flag is hidden inside the “ I warned you.jpg’ file. By checking the file type, it is a data file instead of a jpeg.
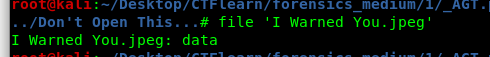
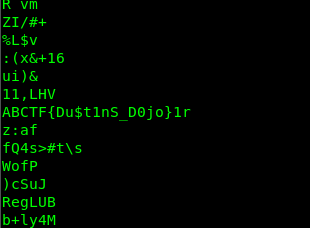
Use a command like ‘strings’ to read the flag.
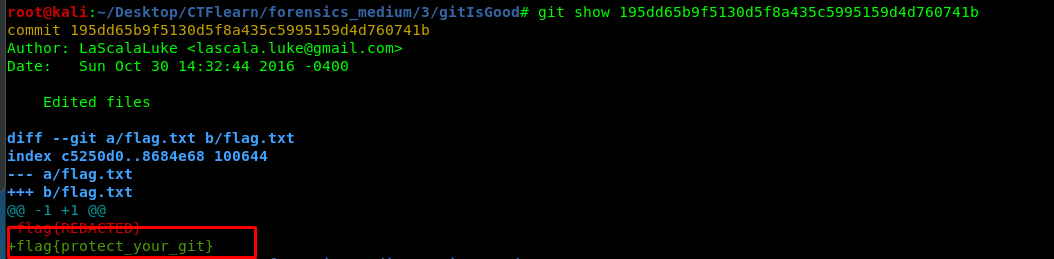
2) Git Is Good
[Link: https://ctflearn.com/challenge/104]
First of all, extract the file and read the log.
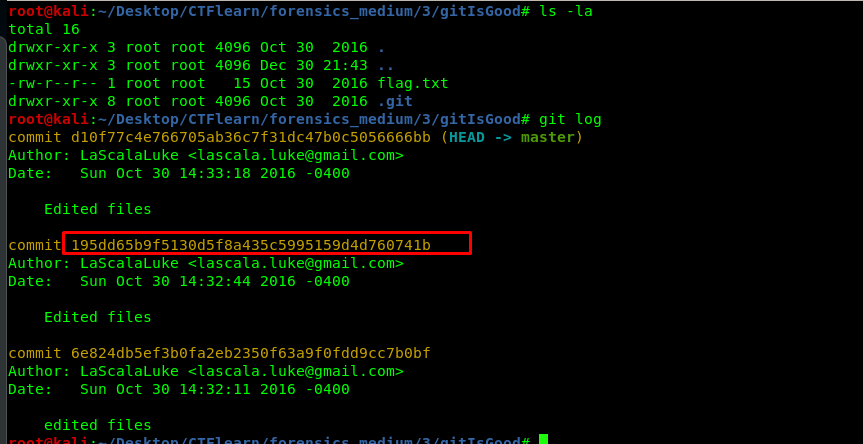
The flag is hidden on the second commit. Use git show to reveal the flag.
3) Up For A Little Challenge?
Link: https://ctflearn.com/challenge/142
For this task, you have to look really deep. First and foremost, locate a MEGA URL inside the download image. (Using strings command)
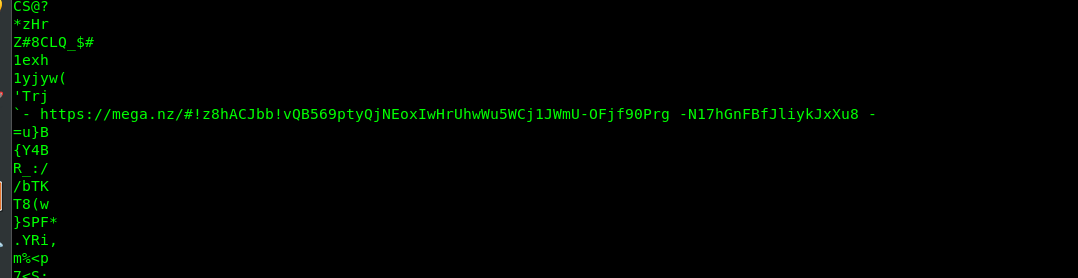
By visiting the MEGA URL, you will get a ZIP file.
Extract the zip file and ignore the ‘Loo Nothing Becomes Useless ack’ as it has nothing to do with the challenge. There is one password-protected zip file.

The extension is a cover-up.
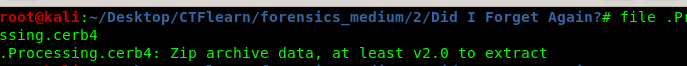
Problem is, where is the password? The password is located at the first downloaded picture where you find the mega URL. (Nothing Is As It Seems)
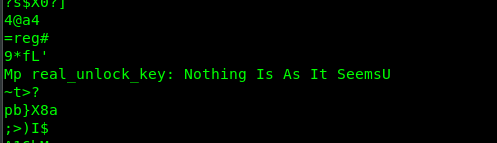
Another image is extracted from the zip. The flag is located at the bottom-right corner.


Hopefully, you can see the flag.
4) Milk’s Best Friend
Link: https://ctflearn.com/challenge/195
Similar to the first task, binwalk the oreo.jpg
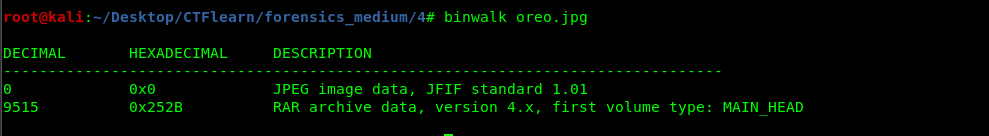
Extract the file with the binwalk.
binwalk --extract --dd=".*" oreo.jpg
After extracting the files, there is another oreo image (2 pieces of oreo). Use ‘strings’ command to locate the flag.
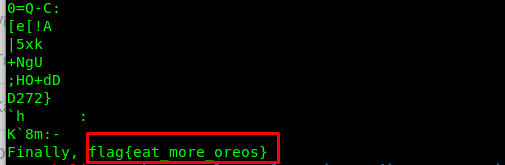
5) Digital Camouflage
Link: https://ctflearn.com/challenge/237
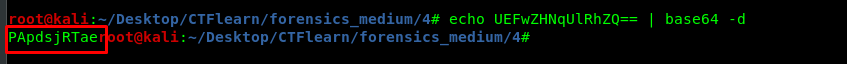
Open up the PCAP file with Wireshark and follow the TCP stream to frame 3.
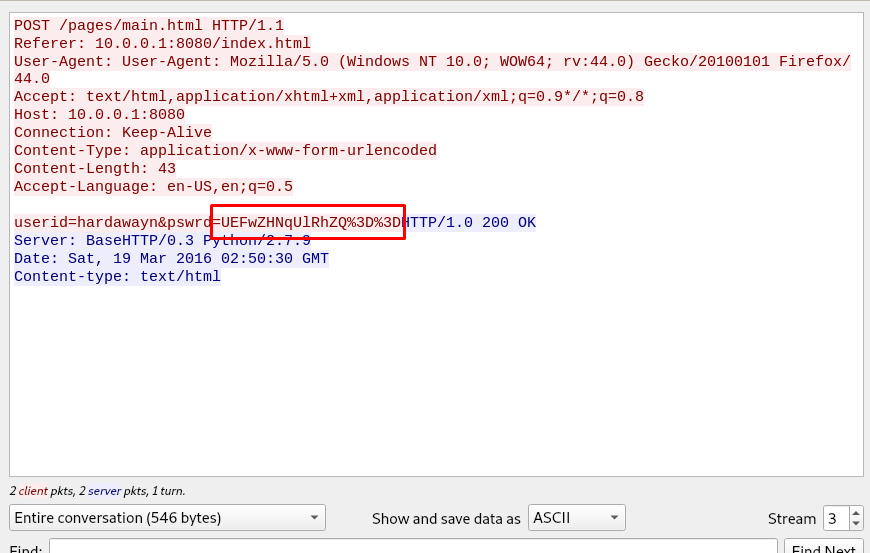
The password is encoded with base64 and make sure to change the URL encoded padding (%3D) to ‘=’.
6) Dumpster
Link: https://ctflearn.com/challenge/355
This is one of the toughest challenges I faced. This is because I’m not really good at Java programming. So, all credits go to this youtube video. First off, open up the dumpster with the visualvm. After that, find the passHash in the dump.
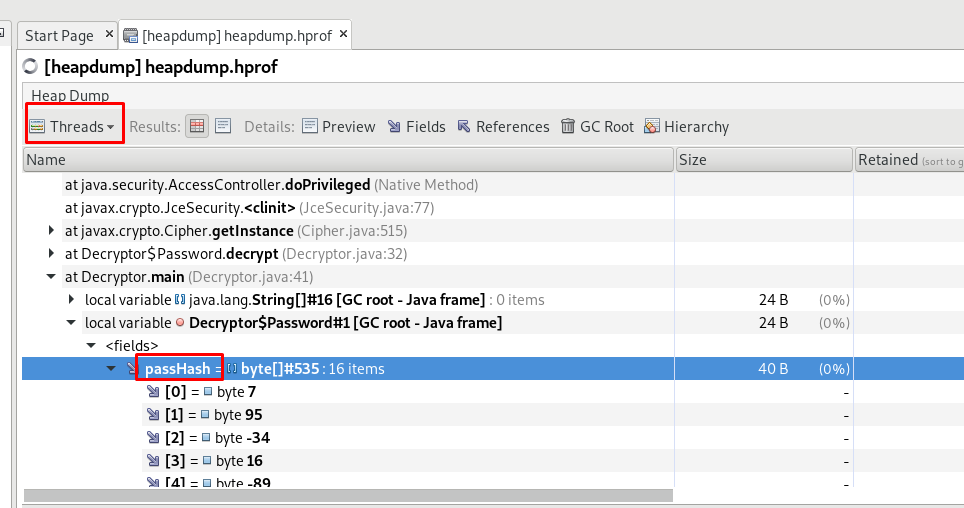
Make sure you have selected the thread. After that, I’ve drafted the following Java code.
import java.security.MessageDigest;
import java.util.Arrays;
import java.util.Base64;
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
public class Decryptor
{
public static final String FLAG = "S+kUZtaHEYpFpv2ixuTnqBdORNzsdVJrAxWznyOljEo=";
public static byte[] decrypt(byte[] msg, byte [] passHash) throws Exception
{
SecretKeySpec spec = new SecretKeySpec(passHash, "AES");
Cipher cipher = Cipher.getInstance("AES/ECB/PKCS5Padding");
cipher.init(Cipher.DECRYPT_MODE, spec);
return cipher.doFinal(msg);
}
public static void main(String[] args) throws Exception
{
byte[] passHash = {7, 95, -34, 16, -89, -86, 73, 108, -128, 71, 43, 41, 100, 40, 53, -24};
System.out.println(new String(decrypt(Base64.getDecoder().decode(FLAG.getBytes()),passHash)));
}
}
Save it as Decryptor.java and run it with the following command.
java Decryptor.java

7) The adventures of Boris Ivanov. Part 1.
Link: https://ctflearn.com/challenge/373
Download the PDF file. No binwalk or steghide for this task, just a normal stereogram. I used stegsolve tool to complete this challenge.
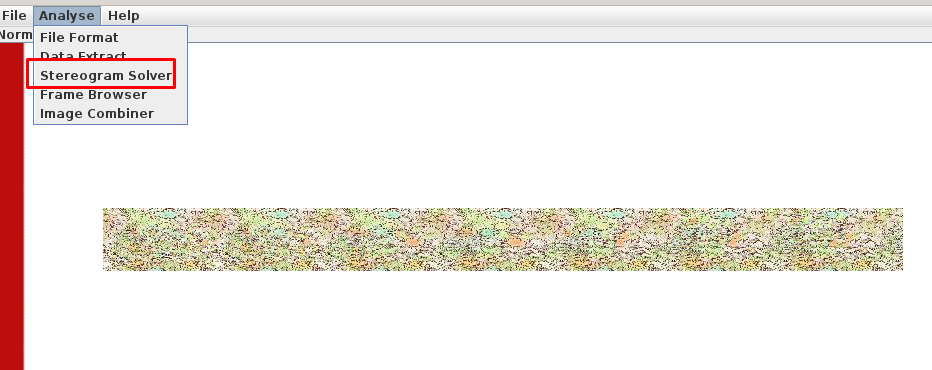
keep pushing the image to left (press right key), you should get the flag at offset 102.

8) Exclusive Santa
Link: https://ctflearn.com/challenge/851
We have two files from the challenge. One is a distorted image and the other is a normal weird image. As the title suggested, the distorted image is somehow XOR between 2 pictures. Our first task is to find one of the picture and XOR it to find another image.
By using the binwalk on the normal image, you will come across the following.
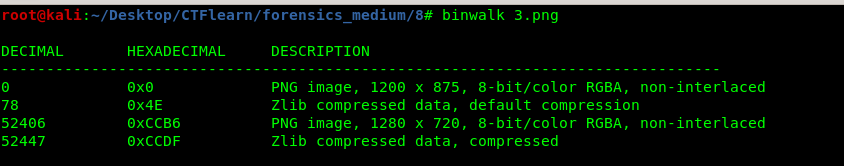
We got another image inside 3.png. Extract all the files within the image, we find what we needed.

Xor the extracted image with the distorted image with stegsolve.

9) F1L3 M1X3R 2 - MP4 Identity Issue
(In progress)
tags: ctflearn - CTF - forensicsThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)