Challenge Land write-up: Steganography
2 minutes to readGreeting! Welcome to another challenge land write up Today, we are going to finish off all four steganography challenges. There is one particular challenge that caught my eye which is the first challenge. This is my first time encounter such kind of interesting problem. I’m going to use it for my next CTF room in THM. Also, make sure you slay the correct enemy. Without further ado, let’s begin with our challenge.

Steganography 1
Download the image and start our very first stego task.

Like I said before, this challenge is a little bit unique. In order to complete this task, we need to do a reverse image search using TinEye.
Look like we have plenty of similar image on the internet. Simply download an image and we are going to compare the original with the image with stego text.
diff -a image1.jpeg ori.jpg | hexdump -C
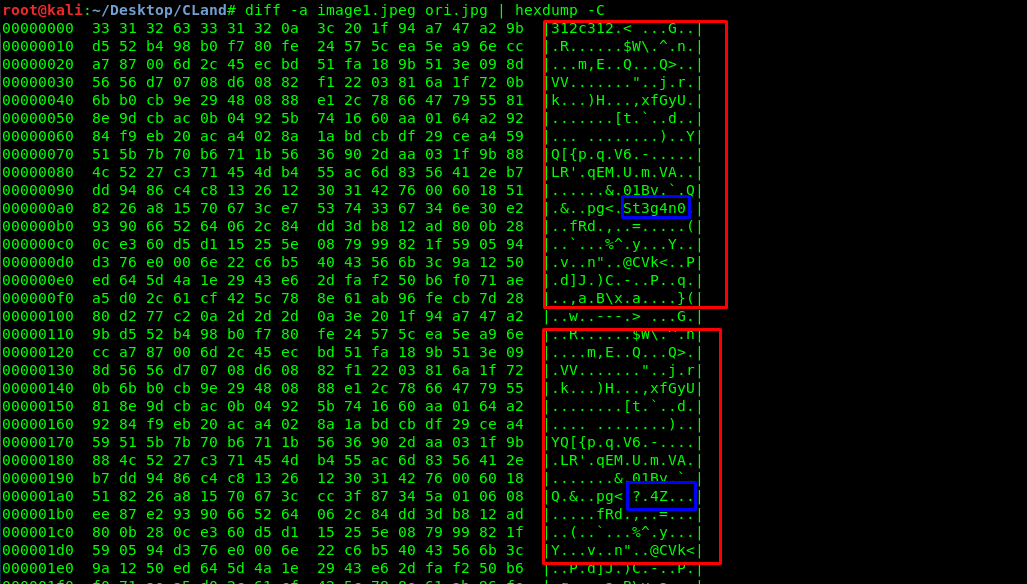
Are you able to distinguish the difference?
Steganography 2
Download the image and you get a similar image as stego 1.

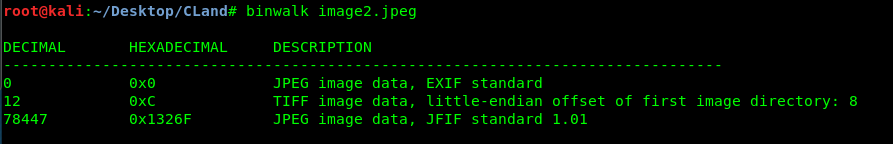
Well, we have an image file within an image file. To extract all the contents within the file, I’m going to use binwalk with the following command.
binwalk --dd='.*' image2.jpeg
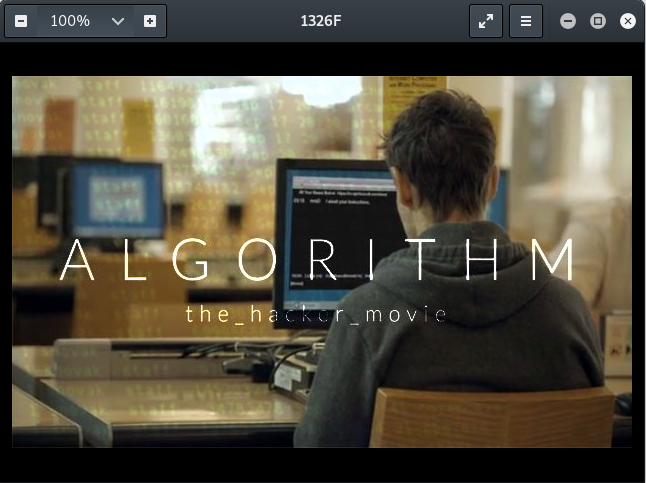
A hidden message inside the image. The flag is the message.
Steganography 3
You get a similar picture.

This one easy, use strings command and finish off the challenge.

Steganography 4
I guess I don’t need to say anything about this.

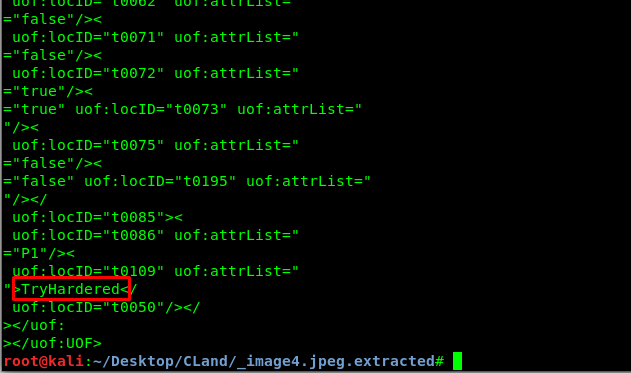
Similar to task 2 but a little bit advance. Extract all the files and read the XML using strings command. You will eventually locate the following flag.
Conclusion
That’s all for the quick and simple steganography challenge. Hope you like it. Until next time.
tags: ChallengeLand - CTF - steganographyThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)