Backdoor write-up: n00b16CTF
5 minutes to readHello there, welcome back to another backdoor noob CTF writeup. Today we are going through 7 challenges on n00b16CTF by backdoor. For your information, there are some challenges currently offline (total 4 challenges) while I writing this writeup. Without further ado, let’s get started
There are a total of 11 tasks (4 down) with cumulative 240 points that can be grabbed from this challenge.
- Batman (30 points)
- Magic (10 points)
- Bin-easy (10 points)
- Robots (20 points)
- Bin-medium (50 points)
- Frost (80 points)
- Matrix (40 points)
- rbash - Server down
- whatzdis - Server down
- fool - file missing
- Eula - Server down
1) Batman (30 points)
Link: https://backdoor.sdslabs.co/challenges/BATMAN
Just play around with the GET request parameter and you are good to go.
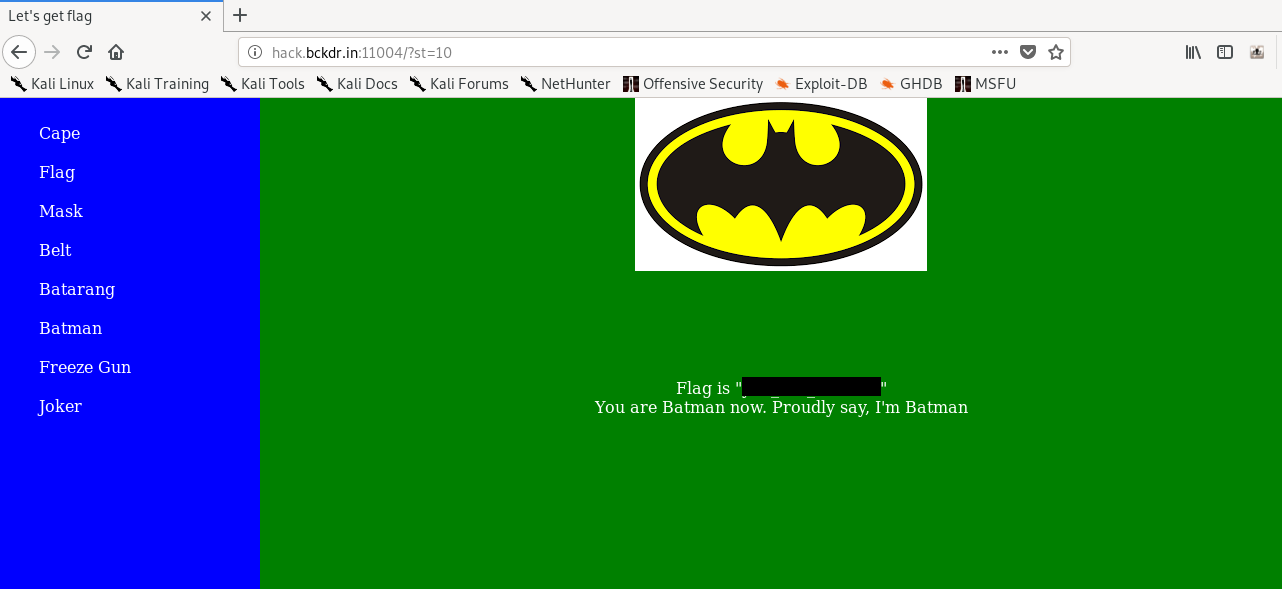
2) Magic (10 points)
Link: https://backdoor.sdslabs.co/challenges/MAGIC
This is a crypto challenge. The sequential To decrypt the given text (UERBIExXT09TS05aIEJLTiBQREEgWURXSEhBSkNBIExXQ0EgRU86IFdIV1pBQUo=) is base64 and then Ceaser cipher.
Note: the flag is a lower-cases
3) Bin-easy (10 points)
Link: https://backdoor.sdslabs.co/challenges/BIN-EASY
Use ‘strings’ command for the flag.
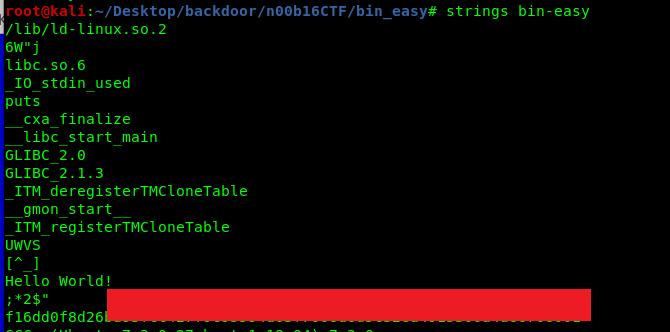
4) Robot (20 points)
Link: https://backdoor.sdslabs.co/challenges/ROBOT
A big hint on the title, the flag is located at robots.txt.
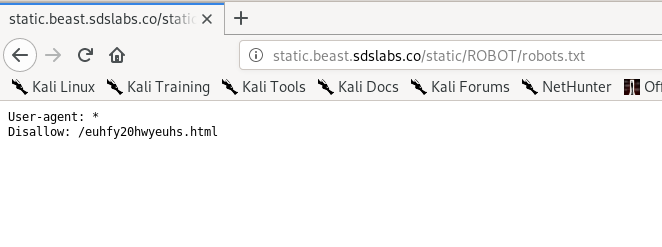
After that, visit the non-indexed site.
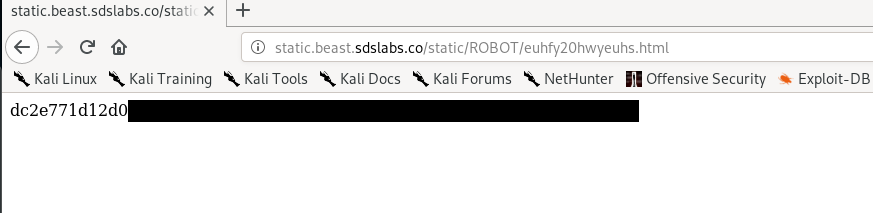
5) Bin-medium (50 points)
Link: https://backdoor.sdslabs.co/challenges/BIN-MEDIUM
There are two ways to complete the challenge:
- (Easy) Change a single byte on the binary
- (Hard) Static analyze the flag inside the memory dump
For the sake of simplicity, I’m only include the easy way in the write-up. First and foremost, let’s inspect the binary.
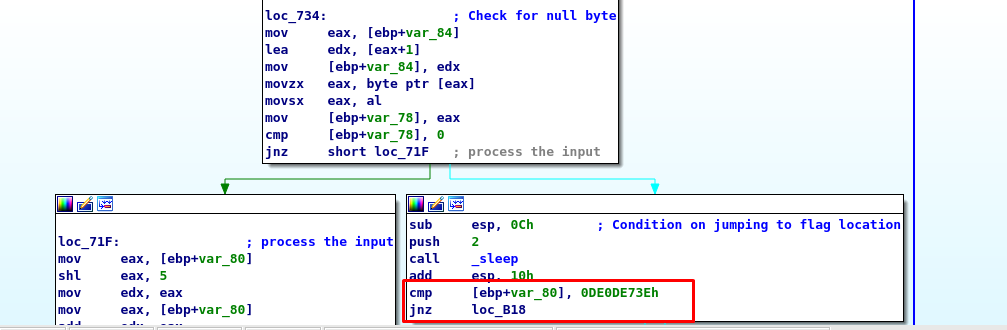
We have 3 important blocks explains the flow of the binary. Firstly, the program checked for any null byte based on our input. If there is no null byte, the binary will perform multiplication and addition operation to the byte and then repeat again with the previously processed byte. the block can be summarized as:
A = (A * 32) + A
where A is the content inside stack [ebp+var_80]
If there is a null byte, the binary will jump the block that compares a certain parameter (0xDE0DE73E). The parameter is important as it leads to the flag. However, we are not sure what kind of input makes the value similar to the 0xDE0DE73E since it involves two operations that depend on the previous. The simplest way is to change the instruction jnz to jz instead
As for the next step, we need to acquire the location of the instruction.
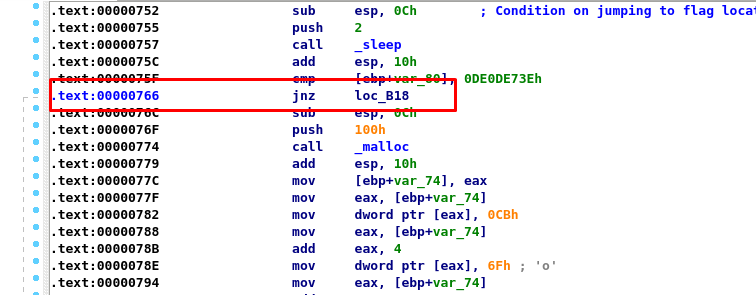
As you can see, the instruction jnz is located at 0x00000766. Then, use a hex editor to change the jnz opcode to jz opcode. By referring to this site, we have to change the byte from 85 to 84.
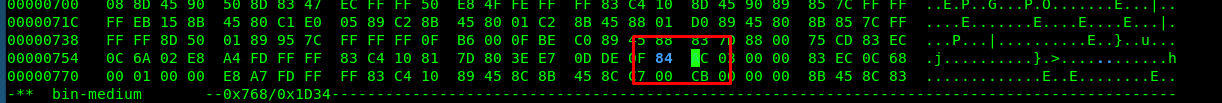
Save it and run the binary.
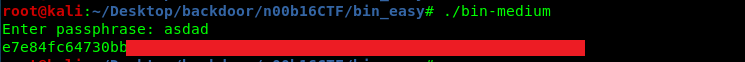
On the other hand, you can analyze the flag inside the following block which will be not covered in this write-up.
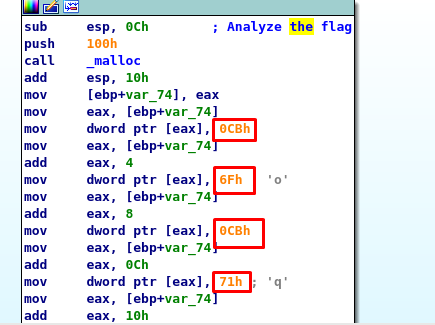
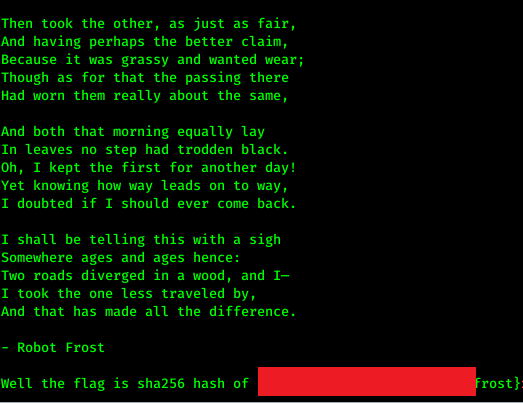
6) Frost (80 points)
Link: https://backdoor.sdslabs.co/challenges/FROST
We have to brute-force the given hex using xortool. But before that, let’s see the highest key probability.
xortool -x frost.hex
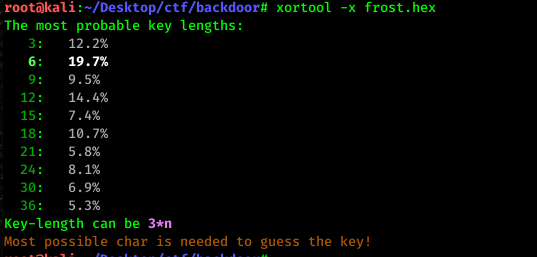
As you can see, the highest guess is 6 keys. Time to brute force the hex with the following command.
xortool -b -l 6 -x frost.hex
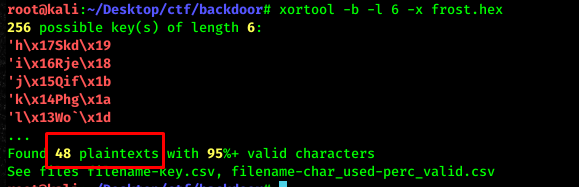
We have like 48 plaintexts with 95%+ of valid characters. All the brute-forced file is usually located at xortool_out. On the next step, we need to find out which output file has a 100% readable character. The summarized report can be found inside the .csv below
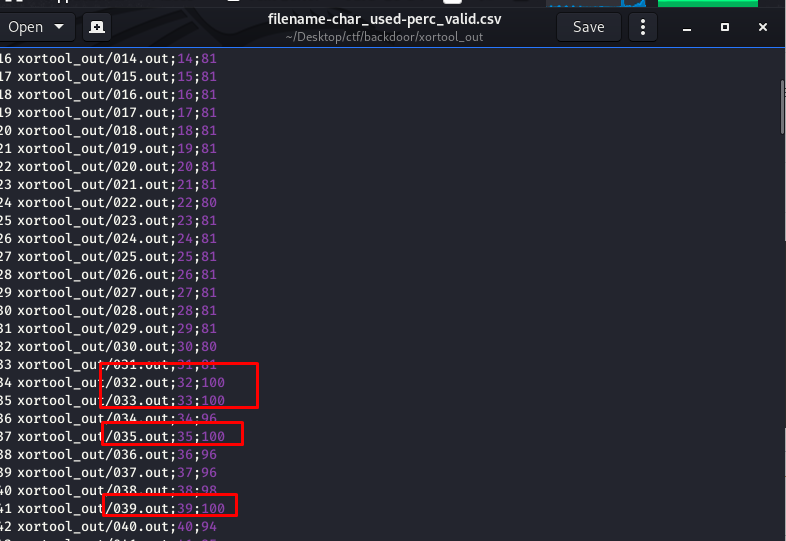
There are like few of it and you have to find it yourself.
7) Matrix (40 points)
[Link: https://backdoor.sdslabs.co/challenges/MATRIX]
This challenge is kinda refreshing to me as this is the only challenge that I looked into the write-up by Jay’s blog. Like jay suggested, the letter ‘g’ act as a delimiter as hex number doesn’t have value ‘g’ in it. We are now going to form the 32 rows 6 columns of letter matrix.
83ad8c
f228bf
c7adf1
4a588e
265a87
cc165d
64ad49
d362ba
d04eed
f459be
9a8ee7
9da116
658f0e
69db80
d3e915
b82986
3e233b
ba40c0
0f42a8
906be0
eec4b7
8fc789
4b7944
366a5e
6cd8cf
5c6f74
033e6a
3e9574
45a461
3390a7
5dedeb
7c944b
After the matrix is formed, we need to transpose it. What does a transpose matrix mean? It means an (M rows N columns) will be reform into an (N rows and M columns) instead. For example, a 2x3 matrix:
1 2
3 4
5 6
will be transposed to a 3x2 matrix:
1 3 5
2 4 6
Similarly, our 32x6 matrix will be transpose into a 6x32 matrix such that:
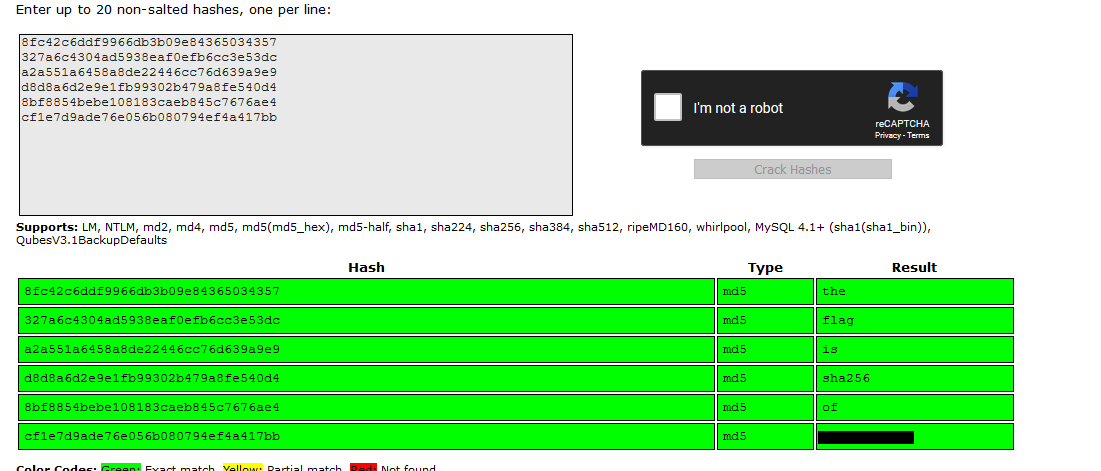
8fc42c6ddf9966db3b09e84365034357
327a6c4304ad5938eaf0efb6cc3e53dc
a2a551a6458a8de22446cc76d639a9e9
d8d8a6d2e9e1fb99302b479a8fe540d4
8bf8854bebe108183caeb845c7676ae4
cf1e7d9ade76e056b080794ef4a417bb
According to Jay, all these character can be cracked with MD5 hash cracking tool.
Conclusion
That’s all for the n00b16CTf write-up. See ya ;)
tags: backdoor - ctfThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)